-
An alleged database of 60 million records from AI music platform Suno, including user contacts and source code, was listed for sale.
-
A massive dump of 80 million credit card records, purportedly with CVV details, appeared alongside claims of unauthorized access to ASUS and Air France systems.
-
The Air France access listing claims it could expose over 2 million user and job candidate records containing sensitive personal information.

The dark web is bustling with unsettling new listings this week. Threat actors are hawking everything from AI music data to millions of credit cards.
Several major brands are implicated in these alleged breaches. The scale of the data involved is significant and potentially very damaging.
New Dark Web Listings Emerge
Our dark web research team uncovered many new underground flea market listings of worrying proportions this week. The team spotted fresh posts advertising stolen data and system access linked to well-known companies.
These listings look like Christmas wish lists from hackers, such as an AI Music company, a multinational technology organisation, a major airline, and thousands of credit cards. Here is a breakdown of what these cyber crooks are promoting in the various shady dark web forums.
Alleged Suno Database and Source Code for Sale
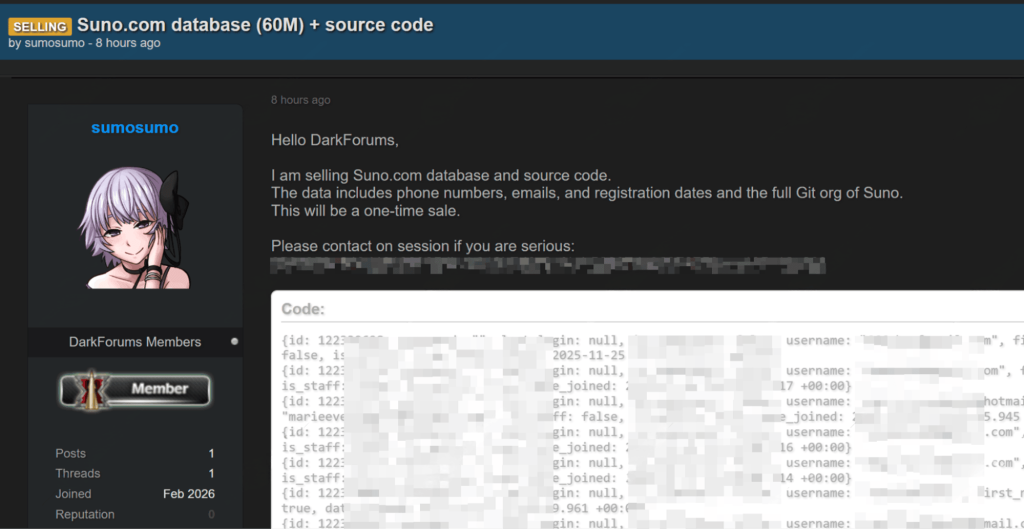
First up is Suno, the popular platform that generates music from text prompts. A threat actor is advertising what they claim is Suno’s entire database and source code. The posted details are specific and alarming.
The seller says the dataset contains about 60 million user records. This allegedly includes phone numbers, email addresses, and registration dates. Perhaps more damaging for the company, the actor also claims to be selling access to Suno’s full Git organization. This means Suno’s proprietary source code, which powers its AI models, is probably now up for sale to the highest bidder.
If this is what actually happened, then we are looking at a serious violation of user privacy and corporate intellectual property. Suno users might face targeted phishing campaigns. The company’s core technology could also be exposed to rivals or malicious actors.
A Massive Card Dump and Corporate Access Claims
The data bazaar didn’t stop there. Another listing promises a huge aggregated dump of 80 million credit card records. The seller mentions that the data includes CVV numbers and has cards with expiration dates stretching to 2039.
Here, we would like to note a crucial detail, however. Collections this large are rarely from a single new breach. They are typically “aggregated collections” stitched together from many old breaches, malware logs, and card-skimming operations.
This is the same model seen in recent targeted discoveries, such as the finding of over 1,800 stolen UK bank cards being sold in a single dark web marketplace, illustrating how localized breaches feed into the global stolen data economy.
This means the data is likely duplicative and may contain many expired or canceled cards. But even a small percentage of valid cards can mean big money for criminals.
Alleged Asus Database on Sale
In separate posts, threat actors made bold claims about accessing corporate systems. One claims to have infiltrated ASUS, the Taiwanese computer hardware company. They advertise access to order data, work orders, device serial numbers, and customer info. They even boast of having admin-level access for internal lookups.
Alleged Admin Access Linked to Air France Listed for Sale
Another post targets Air France. The actor claims to be selling “unauthorized administrative access” to the airline’s systems. They say this access allows the extraction of over 2 million records related to user purchases and job candidates. The listed data fields are extensive, including names, emails, phone numbers, dates of birth, and even application metadata.
Navigating the Murky Digital Underground
Dealing with these kinds of threats is not easy, but it’s also non-negotiable for security teams. Scanning dark web forums manually to detect data leaks is a dangerous venture and also takes time.
If you make any slight mistake and click the wrong link, your computer might end up with a malware infection. That’s why getting a professional dark web monitoring service is no longer an afterthought, but the smart thing to do to boost your security.
These services help companies enter the deepest parts of the dark web, scanning and tracking these threats so that your teams don’t have to go in themselves. A lot goes on in the shady corners of the internet, so to avoid drowning your team with all that noise, dark web monitoring tools often filter alerts by industry or region, enabling you to stay ahead of potential attacks.
We’ve seen how brazen these crooks are getting with their auctions of stolen data. Accurate or not, this week’s listings remind us that the cybercrime landscape is getting more aggressive and our digital data is the target. This aggression was recently crystallized in the confirmed sale of a major retailer’s core source code, a stark reminder that these dark web listings can represent very real and devastating breaches. We should treat it with utmost care.