-
Insider data services are for sale on the dark web for as low as $500, with claims of direct access to employees at major tech firms.
-
Sensitive personal information, from physical addresses to IP data, is being packaged and sold, enabling highly targeted fraud and identity theft.
-
Experts recommend “high observability” of employee behavior and dark web monitoring as critical defenses against these insider threats.
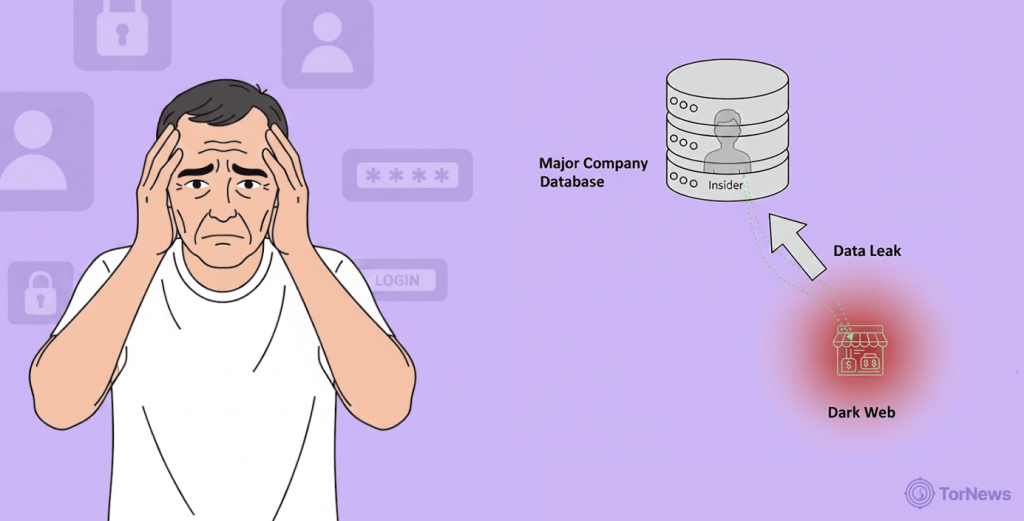
A new cybersecurity research revealed that the majority of confidential information from big companies offered for sale on the dark web isn’t from faceless hackers, but from company insiders.
According to the research findings, insiders from companies like Facebook, Instagram, and Amazon are collaborating with criminals to leak user info online. This turns a serious data breach into an intimate betrayal of user trust.
The Dark Web’s Insider Marketplace
The threat exposure management platform NordStellar has identified a disturbing trend. So far this year, researchers have found 35 dark web posts openly selling services powered by insider data.
Cybercriminals claim to have direct connections to employees at household-name companies. For a fee, they offer to look up and leak any user’s confidential details. This adds another dangerous vector for corporate data to reach the dark web, complementing external breaches like the recent Logitech zero-day incident.
“The majority of the posts offer various look-up services,”explains Vakaris Noreika, a cybersecurity expert at NordStellar. The information for sale is deeply personal, including full names, IP addresses, phone numbers, email addresses, and even physical home addresses.
This goes beyond mere violation of privacy—it’s a toolkit for crime. With these details, criminals can launch precision phishing scams. They can commit fraud or steal someone’s entire identity.
The price tag for this invasion is shockingly low. A basic look-up service starts at just $500. That bargain fee gets a buyer someone’s phone number and a linked email.
For $1,000 or more, customers can purchase “advanced packages.” These contain even more sensitive data, like a user’s date of birth and IP address history.
Beyond Data Leaks: The Service Economy of Crime
The dark web offerings go beyond simple data dumps. A particularly damaging service is account “unbanning.”
Criminals promise to restore social media or e-commerce accounts that were shut down for policy violations. This service is especially harmful to the brands involved.
“Users are often banned for violating the company’s policies or engaging in fraudulent activity,” notes Noreika. By paying an insider to unban an account, a scammer can immediately return to their harmful activities.
This allows them to target more victims. It also severely damages the platform’s reputation and safety efforts. It makes a company’s own security tools and rules seem powerless against internal corruption.
Measures to Mitigate or Combat this Risk
Insider threats aren’t easy to deal with, but there’s still a way – experts say having a solid cybersecurity plan can cut the risk. According to Noreika, two key things strengthen your defense: good monitoring and behavioral analysis.
The first step is ensuring complete visibility into user actions inside company systems. Security teams must be able to see what data employees are accessing.
Once they have that visibility, they can hunt for dangerous anomalies. The goal is to spot potential malicious activity early.
Teams should look for clear warning signs. Is an employee accessing sensitive user data without a valid business reason? Are there signs they are sending that information to personal accounts or devices?
Noreika also stresses foundational security practices. Companies should make sure employees only get access to the data they need for their jobs – it’s called “principle of least privilege.”
Good network setup and data loss prevention tools are also key – when put in place, employees can’t share or download files unless they obtain permission.
Another important thing is dark web monitoring – companies should be on the lookout for posts where their names are mentioned or services supposedly powered by their internal data. For a deeper understanding of this hidden ecosystem, you can explore our comprehensive report on dark web statistics. Having a prepared incident response plan is critical to react swiftly if a malicious insider is discovered.
The battle for data security is increasingly happening on two fronts. Companies must defend against external hackers while also ensuring trust within their own walls. As this research shows, when that internal trust breaks, the cost to everyone’s privacy is devastatingly low.