The Deep Web isn’t some mysterious underworld—it’s actually a huge part of the internet that you use every day without even knowing it. Many people think the web is just what they see on Google, but it is much more interesting (and far bigger than you’d think).
If you have ever logged into your email, checked your bank account online, or accessed the database of a private company, you have been on the Deep Web. This comprehensive guide will cover everything you need to know about what the Deep Web really is, how it works, and why it can be less intimidating than we have imagined it to be.
There’s a lot of confusion about the Deep Web and the Dark Web, and it’s time to clear it up. This guide lets you know exactly what is in this hidden part of the web and how it applies to your everyday digital life.
What is the Deep Web?
It’s basically those corners of the internet that you cannot see using search engines like Google, Bing, or Yahoo. Think of the internet as a large iceburg. The small tip peeking above the water is the Surface Web (the part that search engines can find and index). The Surface Web consists of the news sites, public blogs, online retail stores, Wikipedia…basically, anything you can find through the normal Google search.
Now, think about the rest of the iceburg submerged under water. That larger bulk of the iceberg, which you can see on the surface unless you plunge deeper into the water? That’s the Deep Web—it contains all online content that is hidden from regular search engines.
Let’s clarify something. That the Deep Web is hidden doesn’t mean it is dangerous or illegal. It is simply just a collection of web pages and content that you need some form of authentication, payment, or authorization to access. Your online banking portal? That’s Deep Web. Your personal email inbox? Deep Web too. That company intranet you log into at work? Yes, it’s Deep Web territory as well.
Computer scientist Mike Bergman coined the term “Deep Web” in 2001. When he coined the term, he believed this hidden web was roughly 500 times larger than the surface web. While it is hard to know if those numbers are accurate nowadays, the Deep Web is still much larger than what most people perceive as “the internet.”
Most Deep Web content sits behind what security experts call “walled gardens”—secure areas that require credentials, subscriptions, or permissions to access. Nothing sinister here, it’s about privacy, security, and legitimate business processes.
How Does the Deep Web Work?
The Deep Web operates through a number of mechanisms that keep content hidden from conventional search engine indexing. By understanding these mechanisms, you will see why so much of the internet is invisible to casual users.
- Authentication barriers: Paywalls, access control, and login screens are used to make most Deep Web content hidden and inaccessible. That means, unless search engines can get past these barriers, there is no way for them to index what’s in there. For example, when you log in to your bank account, the pages you see are dynamically generated for you and can’t be replicated or indexed by a search engine.
- Technical limitations: Search engine crawlers—the automated programs that scan and index web content—can’t interact with certain types of content. The crawlers cannot deal well with javascript heavy sites, database query sites or pages that require user interaction in order to generate. This all means that a lot of legitimate content is essentially invisible in search results.
- Robots.txt files and meta tags: Sometimes, admins directly tell the search engines not to index the pages on their site. They do so with the help of e robots.txt file or noindex meta tags. Many organizations use this method to hide specific parts of a webpage from search results while allowing authorized clients or employees to access them.
- Dynamic content generation: Unlike static web pages that exist in a fixed form, much of the Deep Web contains content generated on the fly. When you search for a company’s internal database or request an account balance, the system creates that page specifically for you, at that moment.
- Private networks and protocols: Some content in the Deep Web works on private networks or utilizes protocols outside of standard HTTP/HTTPS. These may require special software, VPN connections, or access to their network (intranet, etc.)
The infrastructure that supports the Deep Web relies mostly on server-side technologies, encrypted connections, and most probably, some effective access control systems. The Deep Web is not meant to be mysterious. It is meant to be functional, secure, and private.
Deep Web Examples: What’s Actually Hiding Under There?

Understanding what exists on the Deep Web can help you understand the whole concept. Here are some common examples you are probably likely to interact with everyday:
- Password-protected content and sites: Sites or pages that require a user name, password, or both: Your private social media profiles, online banking systems, email accounts, the internal HR portal of your company, and paid services like Netflix and Amazon Prime are all aspects of the Deep Web. You are engaging with Deep Web content the moment you log in with your credentials.
- Private databases; intranets: Corporate proprietary databases, university library systems, medical records, private and legal document depositories, and governmental databases make up a large chunk of Deep Web content. Researchers connect these private networks to form what they call a “Deep Web Nest” of information. The files within it hold valuable data that their owners intentionally hide from search engines.
- Dynamic and Real-time content: Search engines can’t index pages that generate content from user input—such as search results from member-only sites, internal searches, real-time stock data, or recommended products.
- Unlinked content: Some web pages exist without any links, such as draft blog posts, temporary pages, or deleted content that still resides on servers.
- Fee-based/paywalled content: Organizations intentionally place authorization systems for accessing academic journals, news archives, professional reports, and specialized databases within the Deep Web.
The Deep Web also encompasses technical elements such as private networks, overlay networks, and peer-to-peer systems operating outside of conventional web protocols. It is essentially any online content that requires you to do more than just enter a URL into the browser.
In a nutshell, here are some examples of Deep Web you probably already use (and maybe even enjoy):
- Logging in to Netflix to view your watch list.
- Logging in to your Gmail inbox.
- Logging in to see your Amazon order history.
- Logging in to your online library journals from university.
- Using a government website portal to file your taxes.
- Logging in to your company’s project management software.
See? Nothing scary. It is pretty much the everyday operational infrastructure of your internet experience. That said, what is the Deep Web used for? Mostly, it is used for making sure your private stuff remains private and for services that require user-specific data.
How Big is the Deep Web?
The size of the Deep Web is truly massive. However, it is difficult to get precise measurements because much of the content we are dealing with is intentionally hidden from the conventional indexing methods.
Some believe the Deep Web is anywhere between 400 and 5,000 times larger than the surface web, which is the part we all interact with every day. It’s more like billions and billions of pages and databases, increasing every second, that regular search engines cannot see.
Historical Estimates
Back in 2001, researcher Michael Bergman estimated the Deep Web to be 500 times larger than the surface web. His work indicated that the Deep Web had over 550 billion documents, while search engines at the time were indexing roughly 1 billion documents.
Current Scale
While the original ratios have shifted as search engines have improved, the content on the Deep Web has grown as well. Recent estimates suggest the Deep Web contains hundreds of times more content than what search engines can access, though the exact figures vary depending on how that content is defined and measured.
Account and Database Content
A large amount of the size of the Deep Web comes from accounts and databases. All Facebook user accounts, Amazon product listings, and banking transactions exist online, but search engines like Google don’t directly crawl or index that information.
- With 5.41 billion people (65.7% of humanity) engaged on social platforms, we’ve created a duplicate internet behind our login screens (Source: DataReportal).
- It’s estimated that up to 376.4 billion emails move through servers each day worldwide – enough to bury every human in 47 emails per day.
- Data suggests that hundreds of millions of people store photos, tax returns, and creative projects on Google Drive, iCloud, and Dropbox.
Considering the billions of user accounts on major platforms and the trillions of data points linked to them is truly mind-boggling.
Storage vs. Accessibility
It’s important to understand that “size” may differ in many ways. Are we referring to the number of unique pages? Are we referring to the amount of storage? Or are we referring to entries in a database? Whichever method used to measure the content gives vastly different results, and that is why estimates vary so widely.
What If Fueling the Growth of the Deep Web?
A number of factors are responsible for the massive size of the Deep Web:
- The growing popularity of password-protected data and private user accounts
- The sheer volume of corporate and government databases
- Real-time and dynamically generated content
- The increase in subscriptions and paywalled content
- Increased concern for privacy means more private content
One thing is certain: The Deep Web constitutes the largest percentage of information available on the internet. The surface web accessed through search engines is merely a tiny part of the digital information infrastructure—just a little glimpse of the far larger web that is under the surface.
Some researchers think that more than 96% of internet content is located in the Deep Web, and it has made the visible web compared to the rest of the digital world seeming just small and insignificant.
Deep Web is Dangerous: Myth or Fact?

This might be one of the biggest misconceptions, and we are going to set the record straight.
Myth: The Deep Web is Dangerous
Most Deep Web content is totally mundane and safe. Your email, online banking, subscription services, and work intranets all exist in the Deep Web. These things aren’t dangerous. They’re just private. Accessing them via legit means (typically involving strong security protocols like HTTPS) is not more dangerous than using the surface web we all know.
Fact: Accessing Some Portions of the Deep Web Comes With Risks
Like any part of the internet, some areas of the Deep Web can be dangerous. But the said risks are mostly confined to specific corners (primarily the Dark Web) rather than the entire Deep Web.
- What causes the misconception: Much of the fear regarding the Deep Web comes from mixing it up with the Dark Web. Several media reports on illegal marketplaces, forums for crime, and dangerous places describe Dark Web activities, not the broader Deep Web ecosystem.
- Actual risks in perspective: Although security risks in Deep Web spaces do exist, they are usually similar to the risks that exist in the surface web. These include phishing attempts, malware, scams, and social engineering attempts. The difference may not necessarily be in the type of threat, but rather the level of sophistication of the attacker or the target they are after.
- Corporate/institutional security: Many organizations actually take advantage of the Deep Web infrastructure to enhance their security. They do so because the Deep Web private networks, encrypted databases and password-protected systems provide better security than the surface web where content is publicly visible.
- Personal safety considerations: For the average user, the biggest risk comes from actively looking for illegal or dangerous material—not accidentally engaging with a Deep Web space while using the internet as normal. The content you access via the Deep Web daily (email, a bank, a subscription) is typically safer than your routine surface web browsing. So, here is the bottom line. The Deep Web is not a digital Wild West, with dangers around every corner. The vast majority of the Deep Web content is simply private, password-protected, or subscription content—existing on the web for legitimate reasons.
Surface Web vs. Deep Web: How They Work
Think of Google search results, like an exclusive party: a page gets in only by being invited directly. That “invitation” comes in the form of crawl access given by the owners of the websites. It works like this:
How Pages Get to Surface Web (like Google):
- Publish content: This can take the form of a blog post, a product page, video – whatever you want, it is then on the web.
- You “Roll Out the Welcome Mat”: You submit a sitemap or meet the required best practice to allow search engine bots (Googlebot, etc.) to crawl your site. This is a make-it-or-break-it step, and your explicit invitation.
- Bots explore your site: Bots are automated crawlers (sometimes referred to spiders, or spider bots) that crawl the pages – examining content, links, and structure.
- Search engines index it: The findings of the crawlers will then be added to the search engine’s index – it’s index of the web – saves the crawler’s findings.
- Results are returned: When someone requests related terms in the search engine, the search engine will query their index and return matching pages that are part of its surface web index.
The Deep Web is Hidden (By Design!)
The main point here is that crawling sites is 100% at the discretion of the site owner. Deep web operators make a deliberate choice:
- They DON’T submit sitemaps;
- They block search engine bots (technologies like robots.txt files, login walls) on purpose;
- They all basically say, “No bots allowed!”
Why is the Deep Web hidden? It’s all about Privacy, Security and Protection:
- Your private data: Now, imagine your online banking dashboard or your medical information portal, or your Netflix watching list popping up in a Google search, open for whoever cares to see. That will be frightening. The deep web way of hiding just keeps the general public from seeing certain sensitive personal data (think stored credit card!!).
- Securing Sensitive Systems: Company intranets, government databases, and subscription archives must remain accessible and functional without being exposed to the general public.
- Protecting Intellectual Property: Hubs for academics, like the Social Science Research Network, have over a million papers in their network. Requiring users to create an account—and blocking search engines from indexing the content—helps protect copyrights and control who can access and benefit from valuable research. “You cannot find me via a Google search.”
Deep Web vs. Dark Web: What are the Key Differences
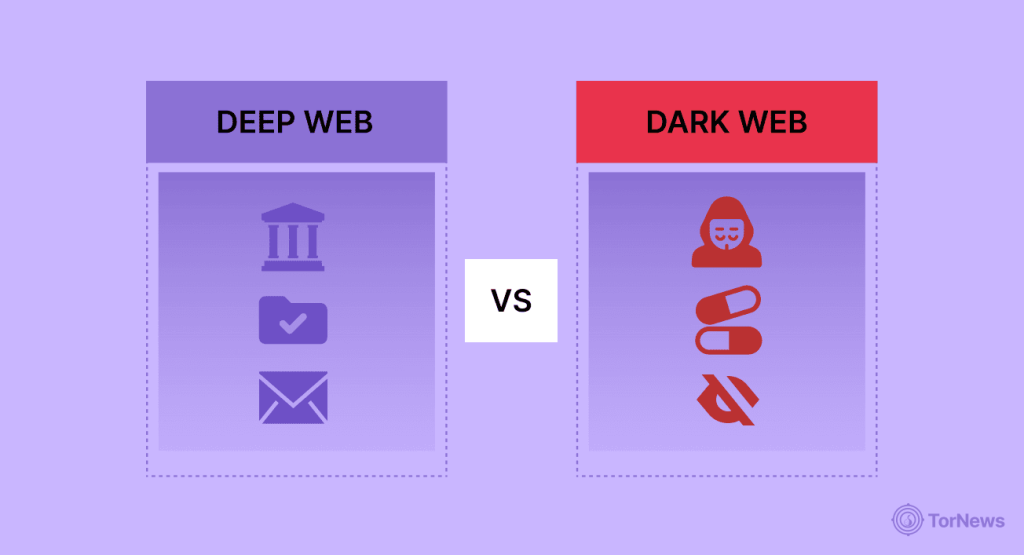
This is where it gets essential, because mixing up Deep Web and Dark Web creates unnecessary panic and subsequent confusion. Although both are “hidden,” the Deep Web and Dark Web represent entirely different concepts.
Like we said earlier, the Deep Web includes all web content that search engines can’t index—meaning your email inbox, company databases, and everything else. It is mostly nothing more than reasonable everyday usage of the internet, with a little added privacy or protection via passwords. Virtually all content in the Deep Web is legal and completely normal.
Specialized software like Tor is required to access the Dark Web, a small, hidden, encrypted part of the Deep Web. Sites on the Dark Web use .onion domains instead of regular web addresses. While the Dark Web hosts illegal markets and other criminal activity, journalists, activists, and ordinary citizens in oppressive regimes also use it legitimately to avoid exposure.
Here’s the size difference that may shock you. If the entire internet were a city, the surface web would be more like the downtown area, with all of the visible stores, businesses, and attractions.
The Deep Web would be all of the private homes, office buildings, and restricted buildings throughout the entire metropolitan area. The Dark Web? It would be like a few hidden speakeasies located underground and throughout the city—there, yet a very small part of the whole city.
Access Methods for Deep Web vs. Dark Web
You can access the Deep Web using traditional browsers, but it requires a login, subscription payment, or valid credentials. Accessing the Dark Web online usually requires some special software (such as Tor, I2P, or even Freenet).
The Nature of the Deep Web Content vs. Dark Web Content
Deep Web content is typically private, but legitimate, and includes things like medical records, legal documents or contracts, subscription services, private social media profiles. The Dark Web has content ranging from privacy tools and whistleblower sites to illegal marketplaces and criminal forums.
Dark Web vs. Deep Web User Intention
Most users of the Deep Web are simply accessing their email, work systems, or subscription services. The Dark Web users are usually looking for anonymous access for legitimate privacy purposes but would fall under the illicit category for other reasons.
Quick Comparison Table
| Feature | Deep Web | Dark Web |
|---|---|---|
| Definition | Unindexed web content (requires login/paywall or subscription/ proper credentials) | Part of the Deep Web requiring special tools |
| Access | Standard browsers like Chrome, Firefox, Safari | Requires special browsers (e.g., Tor, 12P, Freenet) |
| Primary purpose | Privacy, security, functionality | Anonymity (used for both good & bad) |
| Size | Vastly larger (90-95% of the internet) | Much smaller fraction |
| Content examples | Your email, online banking, Netflix account | Anonymous forums, black markets (historically) |
| Legality | Overwhelmingly legal & essential | Mix of legal (whistleblowing) & illegal activity |
What If I Want to Access the Deep Web?
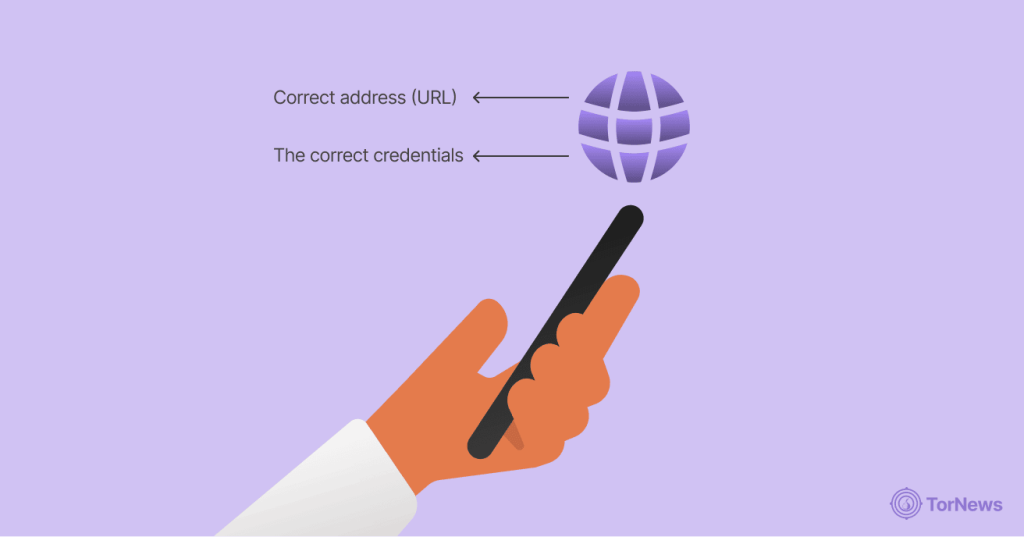
The truth is, you’re already accessing the Deep Web each day without even knowing it! From the technical point of view, you don’t really need any special tools to access the Deep Web most of the time. Every time you log into your email, and look at your bank accounts, or access other password-protected sites, you are accessing the Deep Web.
To access the deep web, you just need these:
- The correct address (URL) of the resource: The web address of the service you want to access (like https://onlinebanking.yourbank.com).
- The correct credentials: Username, password, or permissions to access the content.
When you log into your email, the browser will send your credentials to the email server for validation. Once it validates your credentials, the server lets your browser access your unique inbox content, information not available publicly anywhere. All that content lives on the Deep Web. The process uses familiar internet protocols (HTTP/HTTPS), but restricts access based on authentication. It’s that simple!
But if you want to venture into corners of the Deep Web that are not part of your everyday routine, here are some legitimate ways to access it:
Academic Databases and Libraries
Many universities have access to databases of research materials, databases that are not accessible through standard search engines. These include academic papers, historical documents, specialized research collections, and some of these materials are publicly accessible through library cards or free registration.
Professional Databases
Certain industries, such as law, medicine, and finance maintain extensive databases of professional information. Some of these databases are only accessible through some subscription structure, or require professional credentials, but many have limited free time access or trial access.
Government Databases
Multiple government agencies run publicly searchable databases containing public records, court documents, regulatory filings, and statistical data on the Deep Web. These databases are available for free, but the real deal is in knowing what agencies to search and how and where to look.
Deep Web Search Engines
Some search engines like Pipl, TinEye, or Yippy only focus on the deep web. Sometimes, they can find information that regular search engines can’t. Why? Because they use a different method of crawling or they access different data sources.
Library, Archive Systems
Many libraries, digital libraries, museum collections, and historical archives have deep web content. And with the right credentials or even through an academic institution, you can access them.
You do not need special software to legally explore the deep web. You just need to know what to look for, where to look, and have the appropriate credentials to access it. The harmful or illegal content people associate with the Deep Web actually exists on the Dark Web, which requires special tools like the Tor Browser and carries far greater risk.
Is the Silk Road Still Up and Running?
The original Silk Road (a Dark Web site that became well-known for trading illegal drugs, fake IDs, and other items) got shutdown by the FBI in October 2013. Law enforcement also arrested the site operator, Ross Ulbricht, known as “Dread Pirate Roberts,” and sentenced him to life in prison without parole.
Here’s a concise active-voice rewrite:
Things got complicated when the Silk Road identity didn’t end with the original site. Successor sites like Silk Road 2.0 and 3.0 quickly emerged, trying to capitalize on its name recognition. But law enforcement agencies on both sides of the Atlantic have continued to try to knock down these successor sites. This has led to a cat-and-mouse game of new launches and shutdowns.
Current Status
Now, today, there is no “official” Silk Road marketplace that is still running. Most sites claiming to be Silk Road successors are scams or honeypots run by law enforcement to track illegal activities.
Some sites create what looks like a Silk Road marketplace, but law enforcement shuts them down soon after they launch. The Dark Web marketplace is still alive, but has simply moved on to another platform, with different names and platforms altogether.
What Replaced It
There are countless Dark Web marketplaces that have taken the place of Silk Road, all with their own security protocols, reputations, and lifetimes. Typically, these markets run for months or years before exiting fraudulently or being shut down by law enforcement.
Law Enforcement Response
The FBI, DEA, and Europol have gotten much better at tracking Dark Web activity. Law enforcement agencies have become much more adept at infiltrating these marketplaces.
The takedown of AlphaBay and Hansa Market in 2017 showed that no illegal marketplace is fully protected from law enforcement infiltration.
For anyone interested in this subject, it is worth noting that attempting to access illegal marketplaces can still attract significant legal consequences, regardless of whether you are actually making a purchase or not. Law enforcement agencies have a vested interest in monitoring these sites and they can track all user activity, even when the user believes they are anonymous.
How to Ensure Your Safety on the Deep Web?

Although the Deep Web itself isn’t dangerous, it is always a good idea to exercise good digital security, regardless of whether you are checking your emails or searching specialized databases online.
Implement Strong Security Practices
- Strong passwords: Most parts of the Deep Web require some kind of login credentials. To be prudent, you want to be using strong and different passwords for each of your services. A password manager will help you remember and utilize a complex password, instead of a simple or common password for a service.
- Two-factor authentication: You will definitely want to set-up 2FA on as many services as possible. This is most critical on sensitive accounts at your bank, certain emails, and work systems. 2FA adds another layer of security and helps protect your account if your password gets exposed.
- Changing passwords: Always remember to change the password for important accounts from time to time. Immediately change it if you suspect a security breach.
Securing Endpoints
- Update regularly: Make sure that you keep your browser, operating system, and security software fully patched with current updates. Most attacks on the Deep Web often happen in using exploits in outdated software.
- Use good Antivirus: While you may get lucky avoiding malware in your email, there are some areas of the Deep Web, especially close to Dark Web territory, that may have malicious content. So, using antivirus will help ensure you are not at risk of any lurking threat.
- Browser security settings: Similar to any software, as a minimum you should configure your browser to have the security settings that best compliments your situation. Block or disable plugins that are not necessary, turn on ad blockers, and think about using a browser with increased privacy features for sensitive Deep Web activity.
Learn Smart Browsing Habits
- Website authentication: Before logging into any Deep Web site, double-check that you are on the legitimate site before entering your credentials. Phishing sites frequently mirror the login pages of well-known sites.
- Secure connection: Before entering any login credentials, or any sensitive information, you should also ensure that you are using a secure connection (we look for the locked padlock icon on the browser). When you use a secure connection, the website encrypts all the information you send or receive.
- Phishing: Always be cautious of any emails or messages that appear to request information such as your login credentials or personal information, even if they do not seem to be suspicious. Always check the sender and always avoid clicking on links that seem suspicious whatsoever. If a legitimate service requests your password via email – just delete the email and never reply, as they are not a legitimate company.
- Avoid downloading suspicious material: If you are unfamiliar with the source of a file, even if it looks legitimate, do not download it from the Deep Web. Attackers have downloaded malware from breached public databases or private sites in some cases.
- Use a VPN: You may be thinking that the average user of the Deep Web does not need to use a VPN for everyday access. However, if you want some minor level of increased privacy and security, even if you are just accessing content (especially sensitive content), or if you’re on public WiFi, using a reputable VPN is always advisable. A good VPN offers features such as “Stealth,” IP leak protection, a no-logs policy, and ultra-fast https: (or secure with the using wireguard or OpenVPN) protocols that help keep you safe while accessing content on a Deep Web.
Be careful with personal information
- Limit exposure of personal information: Only submit necessary personal information when accessing Deep Web services. Many legitimate services will ask for far more data than they actually need.
- Know data retention policies: For those Deep Web services that you use regularly, read the Privacy Policies, especially if you are submitting sensitive personal or financial information.
- Audit account use: Make a point to monitor your accounts for suspicious activity. This might be something you do out of habit. Pay particular close attention to your financial accounts and services that include your personal information.
Know Your Legal Constraints
- Know terms of service: Many Deep Web services will have explicit terms of service for how their site is used. Violating these will not only terminate your ability to use that site, but can also cause you serious legal problems.
- Avoid illicit content: Only a small percentage of the Deep Web is composed of illegal content. Of course, if you feel you are heading into a gray area, proceed with caution, so you do not mistakenly click or download illegal content.
- Protect intellectual property: Along with legal constraints, intellectual property is abundant on the Deep Web. Keep in mind that many Deep Web resources are copyrighted and accessible only to authorized users. Using or distributing one of these resources without explicit permission may attract legal action for misuse.
If You’re Accessing the Dark Web
- Use a Tor browser: Only download a Tor Browser from the Tor Project site (https://www.torproject.org/). Also, do not update the Tor Browser or download add-ons that may compromise your anonymity.
- Disable scripts: Go to Tor Browser preferences, and set the security level to “Safest” (or at least “Safer”). This will turn off JavaScript and any potentially harmful scripts by default.
- Never use your real personal information: When you are on Tor Browser do not log into your personal accounts (e.g., Facebook or main email). If you must log into personal accounts, then create fake ones when you go to suspicious dark web sites. Avoid using your “real” identity (be extra careful on this)
- Don’t download files: Downloading files with Tor Browser is risky. The file might have malware in it. If you have to open downloaded files from the Tor Browser, scan them with your security software (in a secure environment) before you open the file.
- Be suspicious (no really): Consider everything as hostile. Don’t trust links or files. Don’t provide personal information. Do not just assume that your anonymity cannot be tampered with (especially if you mess up). To be safe when you are accessing the Deep Web, always apply the same common precautions you employ anytime you go online. And perhaps put more deliberate thought around authentication procedures and privacy settings. In fact, the overwhelming majority of risk comes from poor security hygiene, not the Deep Web environment itself.
Best VPN for Accessing the Deep Web: NordVPN

NordVPN is more like the Swiss Army knife for dark web tools. It doesn’t just hide your IP but will also take proactive measures to protect you from lurking threats. With auto-optimized routing for Tor, it is a brilliant tool for a new user, and their audited zero-logs policies give a suspicious user peace of mind.
Special servers that route traffic directly through Tor (you don’t need any separate Tor browser for basic protection). Blocks ads, trackers, and sites that have malware. It scans your info (like emails) on the dark web to see if it appears on leak sites.
It doesn’t keep record of your online activities, so snoopers or even your ISP won’t know you’ve been to the Deep Web or the Dark Web. It hides your VPN traffic and makes it appear as regular HTTPS – crucial for bypassing firewalls in restrictive regions.
How to Access .Onion Sites with the Tor Browser (Step-by-Step)
You can consider the Tor browser your digital invisibility cloak. It sends your signal across more than 7000 volunteers from all over the world, and by doing so, it wipes out your digital trail. It can get you access to .onion, but more than that it is a critical line of defense for journalists, activists and anyone trying to circumvent censorship or surveillance.
It can also provide an additional level of privacy and anonymity when you want access to specific Deep Web platforms. Are you wondering how you can navigate the dark web using the Tor browser online?
Here’s a step by step guide:
Works on Windows, Mac, Linux & Android. iOS offers only a few options.
1. Your first step is to download the Tor Browser
- Go to the official Tor Project site (https://www.torproject.org).
- Click the “Download for…” your operating system. Never download Tor from third-party sites!
2. Next, Install It like you would any app
- Open the .exe (Windows) or .dmg (Mac) file.
- Select a place to install (default is fine).
- Launch the Tor browser after it is installed.
3. Connect to Tor
- If this is your first time running the Tor browser, click the big “Connect” button (most will not need to configure it).
- Advanced tip: if you are in a censored country (e.g., China/Iran) and need to enable bridge, click “Configure” instead of “Connect”.
4. Navigate the web safely
- For browsing the surface web – you can use DuckDuckGo (it is pre-loaded).
- For .onion websites – you must type the ENTIRE onion address, just like links on the surface web. For example, you need to enter http://bbcnewsv2vjtpsuy.onion.
Can’t tell which onion links are legit? Use Tor.Dog or Dark.Fail for verified onion directory sites (but still be cautious!).
Conclusion
The Deep Web is not the dark and mysterious digital underworld portrayed in popular media. Rather, it is simply a gigantic collection of private, password-protected content that everyone engages with every day without even realizing it. We are talking email inboxes, online banking, subscriptions with username and password access, etc.
Think of it as the private side of the internet, which has been intentionally made more secure than the Surface Web. Confusing the Deep Web with the tiny, but more dangerous Dark Web has made people fear what is really just a normal, legitimate part of the internet.
Knowing the difference is really important for digital literacy. To use the Deep Web, you do not need any special precaution; just every day online safety practices. All you need to do is practice good cybersecurity (strong passwords, updated software regularly, carefully handling your personal information, etc…).
So, the next time someone says “the mysterious Deep Web”, you will (or should) know it is anything but mysterious. It is simply doing what it was designed to do, which is make your interactions safe and entirely private.
FAQs
Accessing the Deep Web is totally legal. In fact, you access the Deep Web all the time when you check your email or log into your bank account online. Only specific illegal activities – no matter where they occur online – are illegal.
All content on the Deep Web (besides the Dark Web, which is a tiny subset of the Deep Web) can be accessed through typical browsers, using a login, subscription or other proper authorization. The dark web is the only part of the Deep Web that you need special software to access.
No, search engines cannot search or index any Deep Web content by definition. But services you use may be keeping record of your activity based on their privacy policies. Always read the terms of service before using any service.
Early estimates offered rough figures, but measuring the exact size of the Deep Web is impossible because much of it remains hidden. While current estimates vary widely, it’s clear that the Deep Web contains far more content than search engines can access.
The Deep Web accounts for all of the content that search engines cannot access – mostly all legitimate private content like email accounts, subscription databases, etc. The Dark Web is a small part of the Deep Web that is also hidden and can only be accessed using special software. Some of these websites on the Dark Web are legitimate privacy tools, while the vast majority are illegal content.
You are not likely to encounter illegal materials from general Deep Web usage like checking e-mail, accessing subscription databases, etc. Illegal content is largely concentrated in a small part of the Deep Web called the Dark Web, and you generally need special software to access it.
There is no real requirement to use a VPN to access typical Deep Web content such as online banking, checking in your e-mail, etc. However, a VPN can provide a greater measure of privacy and security in accessing sensitive information via the Deep Web and if you are using a public WiFi source.