The fact is that the online world is a wild place. Each time you go online, you create a digital footprint that can be tracked. We know it isn’t good, and it shouldn’t be like this. For a long period now, people have been using two very strong alternatives to regain privacy – a Virtual Private Network (VPN) and the Tor Browser. Both VPNs and the Tor Browser protect you, provide anonymity, and promote the theme of security.
However, it’s important to mention that both VPN and the Tor browser are two different tools that operate independently of each other. What is good for one alternative can be a complete nightmare for the other.
So how do you know what is best for you? The decision is not about which option is “better,” it is about which is the best fit for your needs. That’s why we created this guide. We will provide you with a thorough knowledge of both tools and help you make the best decision depending on your needs.
VPN vs. Tor: Quick Comparison Table

| Feature | VPN | Tor |
|---|---|---|
| Purpose | Provides overall online privacy and security for everyday use. | Extreme anonymity and circumvention of censorship. |
| Speed | Fast; usually, very little effect on your internet speed. | Very slow; routing through multiple layers (in addition to possibly slow download speeds) makes it very slow. |
| Encryption | Strong single-hop encryption. | Multiple layers of onion-like encryption. |
| Servers | Private, paid servers run by a VPN company. | Community-run volunteer relays. |
| Ease of use | Simple; one click connects to your VPN provider. | It is slightly more complex to use, especially if you have to configure certain settings. |
| Cost | Usually, a subscription-based service is required for a quality VPN. | Free to use. |
| Anonymity | Good, but depends on the VPN provider. | Extremely high-designed for maximum anonymity. |
| Threats | At risk, only if the VPN provider stores logs or if the server has been compromised. | At risk if the exit node is malicious. |
| What it protects | All your device’s internet traffic (browsers, apps, etc.). | Only that traffic is going through the Tor Browser. |
What is Tor?

If a VPN can be considered an armored car, then the Tor Browser is like a very complex and multi-layered cloak of Invisibility. Tor stands for “The Onion Router” for a reason.
Instead of routing your traffic through a single server, Tor routes your data through three randomly chosen relays run by volunteers over the world. Each relay peels back a single layer like an onion before sending your data to the next relay and eventually on to your destination.
The last relay is called the exit node, which is the first connection to the public internet. The beauty of this process is; no single relay knows from where the data was initiated or the finish location as it passes through the tor network. The browser is designed for anonymity, which is ideal for journalists, activists, and others who need to operate successfully in high-risk environments.
Tor Pros
- Exceptional anonymity: Tor is created for anonymity, and it hides your information very well. The multi-layered encryption makes it very difficult to trace anything back to you.
- Free of charge: The Tor network is operated by volunteers, so it won’t cost you anything to use.
- Bypasses censorship: Tor is your best bet at bypassing internet censorship. Because traffic can’t be identified or blocked. This helps in bypassing censorship in oppressive countries.
- Access to the dark web: Tor is the only way to access .onion websites, which are the anonymous part of the internet, often considered the Dark Web.
Tor Cons
- Very slow: All that hopping and re-encrypting on the Tor network takes time. Your internet speed will drop significantly, which eliminates its usefulness for streaming, gaming, or downloading large files.
- Not a system-wide solution: The Tor Browser will only encrypt traffic that travels through the browser itself. Any other apps on your device, such as your email client or other messaging apps, will not be protected by Tor.
- Bad reputation: Tor is used to conduct illegal activity, and your ISP may flag your connection just for using Tor. (This is one reason people use a VPN with Tor).
- Vulnerable exit nodes: The exit node is where your data leaves the Tor network. It is unencrypted at this point, and if someone is running a malicious exit node, they can potentially watch your activity.
What is a VPN?

A VPN is like a bulletproof vehicle protecting your travels online. When you activate your VPN, it creates an encrypted, secure tunnel between your device and a VPN accessible server.
All of your online traffic, including web traffic, will flow through the encrypted tunnel. No one will ever be able to tell what you are doing online, including your ISP. All they will see is that you are connected to a server in a location, such as New York, and far from your current location. So, they won’t see your activity of downloading files or sites you are looking up.
A good VPN has successful means of masking your IP address and at least making it look like you are browsing from another location. This is an added benefit whenever accessing content that is geo-restricted (like a Netflix movie that only shows in other parts of the world).
The best VPNs (like NordVPN) may even allow the use of another encryption layer, while still being mindful of safe browsing and keeping your speed.
VPN Pros
- Speed: A paid VPN is usually fast, and the minimal extra process should not really be noticed as a difference. Because of this speed, it makes VPN an ideal choice for regular use and things like streaming, gaming, and video calls.
- Ease of use: From the very beginning, the VPN apps are implemented with user experience as a priority. To be honest, you simply push a button, and you are connected. Unlike many other tech products, you don’t have to search for and install complicated software. Besides, there’s no need to obtain any special technical knowledge.
- System-wide protection: A VPN app keeps your entire device traffic protected—not merely your web browsing traffic. The VPN app protection expands into other apps, games, or anything that performs something related to the Internet.
- Versatile: Aside from using a VPN to remain anonymous, you can also use a VPN to bypass geo-blocks, enhance your connection when experiencing ISP throttling, and a VPN can assist as protection against certain DDoS attacks.
VPN Cons
- You must trust the provider: Even with a VPN, your traffic still goes through their servers. You are trusting that company not to log your information. That’s why it’s important to choose a VPN that’s established, with an audited, strict no-logging policy.
- Cost: There are free VPNs, but they often limit your data allowance, slow down your connection speed, or worse yet, may sell your data to make money. A good VPN service will likely involve a subscription fee.
- Can be blocked: Some websites, especially streaming services, will actively block traffic from known VPN servers. Although VPN providers continue attempts to avoid blocks, circumventing the block can be a constant battle.
Tor Onion Routing and Single-Hop VPN Routing
This is where the real technical difference begins. A VPN uses single-hop routing. Data is encrypted from your device and sent to that single exit (VPN) server.
It is decrypted there and then sent on its way. The VPN provides a direct connection.
Tor onion routing is multi-hop routing. Your data is encrypted three times before it leaves your device. The data first goes to the entry node from your device (which knows your IP address, but does not know your destination).
From the entry node, the data goes to the middle node (which does not know anything about you or where your data is coming from or any destination). When the data leaves the middle node, it will go to the exit node (which knows the destination on the internet, but does not know your IP address).
Each of these “routing hops” is an additional layer of complexity which can provide anonymity; however, they take time to route the data from hop to hop.
You can think about it as receiving or sending a package, where you have to send a package to three different post offices, each with an envelope with the next specific destination. Though each post office knows its own destination only, they will have no recollection of where the package started.
The Tor Browser vs. VPN Apps
This is an important distinction to make. A VPN app is a system-wide tool. Once you turn it on, it encrypts all web traffic from your device – your web browser, your messaging apps, your streaming services, everything. It’s a full-time, constantly-on bodyguard for your data.
The Tor Browser is a stand-alone application. It is a modified version of Firefox and only directs traffic that goes through the browser itself. Any other app running on your computer – like your email client or chat service will not be protected by Tor.
This is a huge detail that is often overlooked. If you want to protect everything on your device, a VPN app is your only real option.
Can You Use Tor and a VPN at the Same Time?
This is an excellent question. Usually, it is possible to use both simultaneously, which may afford one more layer of privacy protection, but probably not everyone wants to add the complication of trying to use both at the same time.
Typically, the combination is used for a very specific purpose: to mask the fact that you are using Tor in the first place. Here are your two main options.
Tor over VPN
This is the usual and most favored method. You first connect to the VPN, and then you launch the Tor Browser. Your traffic goes through your device to the VPN server, then into the Tor network.
- Benefits: Your ISP can’t see that you’re using Tor; they just see that you’re connected to the VPN. The Tor entry node can’t see your real IP address either; it only sees the VPN server’s IP.
- Drawbacks: It can be incredibly slow, and you’re still trusting the VPN provider.
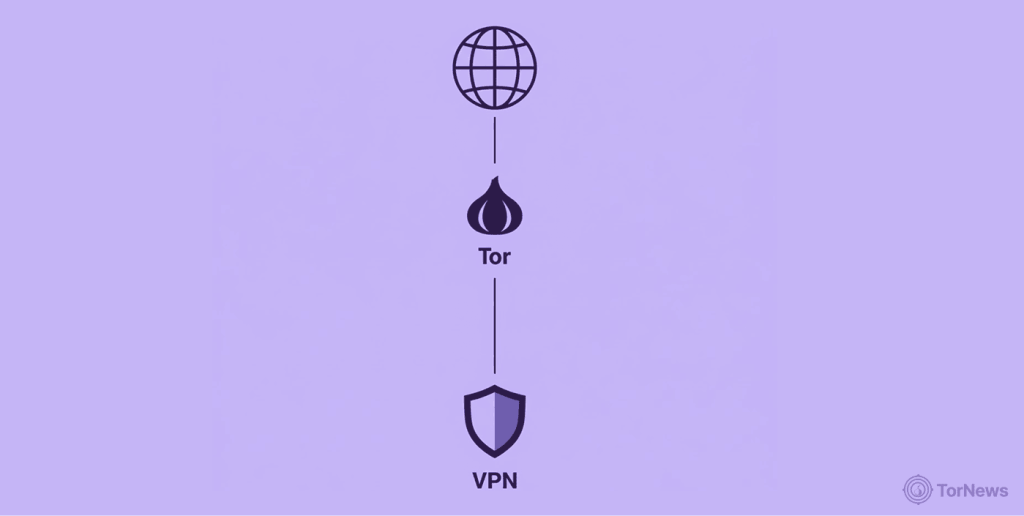
VPN over Tor
This method is rarely recommended. In this case, you connect to the Tor network first, then you connect to a VPN server:
- Benefits: Your traffic is encrypted on the Tor network, and then is also encrypted by the VPN. This is a major plus if you’re worried about a malicious Tor exit node.
- Drawbacks: Your ISP can still see that you’re using Tor. And because your traffic is decrypted at the VPN server, that provider still gets to see your browsing activity, which defeats some of the purpose of using Tor for anonymity in the first place.
Are VPNs and Tor legal?
Most people often ask this question, and here’s the word: both a VPN and the Tor Browser are legal in most countries. Using them is a legal act.
The concern? It’s not on the tool; it’s on what you do with the tool. A screwdriver might be a legal (and useful) tool, but used to open a locked door. So, a VPN and Tor can certainly be utilized for illegal purposes, and they are illegal even if you are utilizing a legal tool to commit that illegal purpose.
Sadly, a very small number of countries feel that it is not correct to give their citizens this level of privacy and have enacted outright bans or severe restrictions on using VPNs or Tor.
- Countries with Complete Bans: There are countries where VPNs are outright banned entirely, such as Belarus, Iraq, Turkmenistan, and North Korea. These countries feel that VPNs pose a threat to their right to surveillance and have awareness of information traveling through their jurisdictions. The penalties for VPN use in these countries can range from heavy fines to imprisonment.
- Countries with restrictions: There are also countries, such as China, Russia, Iran, and the UAE, that do not have a complete ban, but do have restrictions for VPN use. VPN usage should only be allowed from Government-approved VPN services, which somewhat defeats the purpose by providing logs of your data. Alternatively, countries such as Russia have laws restricting the sharing of information on bypassing state-mandated internet filters, so VPN providers find it difficult to operate.
A tool can raise a red flag, even in places where the tool is legal. In some countries, while the tool itself is not illegal, your ISP may flag your connection to the VPN or Tor network simply by virtue of the tool’s association with the act of bypassing censorship.
That’s where the Tor over VPN setup can help, since you are hiding the fact that you are using Tor from your ISP, and therefore may be a necessary precaution for individuals living in a restrictive country.
Conclusion
Ultimately, the decision between using a Tor vs. a VPN service is completely subjective based on your safety needs. If you’re looking for basic everyday privacy, streaming, and securing your browsing, we believe a VPN wins – hands down! VPNs have the speed and ease of use, and will safeguard your whole device.
However, if you are an activist, a journalist, or someone trying to escape strong censorship in an environment where true anonymity is paramount to your safety, the Tor Browser is a necessary tool in your toolkit. It can be slow and a little clunky, but from our experience, it is simply the best option for the type of service it provides.
Regardless of what you choose, the important part is that you must remember the following: always keep your privacy at the forefront of your mind. Don’t just browse, but do so smartly.
FAQs
The primary threat is the exit node. That is the last computer through which your information is transmitted before it is visible to the web. At the exit node, your information is not encrypted. If a criminal runs the exit node, they can look at your activity.
People utilize them together because the combination provides even more anonymity. The most common way to do this is Tor over VPN (connect to a VPN first). This direction will bring your Tor traffic through the VPN, which disguises that you are using Tor to your ISP. The combination is important for activists or journalists in a country with restrictive laws.
A paid VPN is much faster. A VPN only uses one server, and there is a negligible speed loss. Tor is slow because your data hops along three random computers around the world that are volunteer-run. That is why Tor is bad for streaming, gaming, or downloading large files.