Ransomware attacks have become one of the most serious cybersecurity threats in today’s digital landscape, affecting both individuals and large organizations worldwide. These attacks cause severe financial losses, operational disruption, psychological stress, and long-term damage to brand reputation, especially for businesses and government platforms.
While anyone can fall victim to ransomware, cybercriminals increasingly target high-profile organizations such as technology companies, financial institutions, educational bodies, and healthcare providers, where sensitive data and critical systems are at stake. As ransomware tactics continue to evolve in 2026, the need for awareness and prevention has never been greater.
This article explains what a ransomware attack is, explores its major types, and outlines practical prevention strategies to help you stay protected in an increasingly hostile cyber environment.
What is Ransomware
Simply put, ransomware occurs when a cybercriminal encrypts a victim’s data or account and demands payment before restoring access.
In today’s world, ransomware has evolved to not just gaining access to the victim’s account but also being able to steal certain information from the account or data. Cybercriminals can sell the stolen data on the dark web to the highest bidder or expose it publicly if it contains sensitive information about the victim.
This creates a double-edged sword for the victim and has remained one of the biggest concerns in the world of cybercrime. Ransomware has a severe impact on organizations, including public services such as hospitals, where attacks can delay treatment for patients in critical conditions.
Why Ransomware Attacks are Becoming More Sophisticated
Ransomware has grown steadily since 1989, when the first known variant, nicknamed the AIDS Trojan, appeared. Ransomware took off in 2017 with WannaCry, catching the attention of cybercriminals eager for profit. In just the first half of 2018, 181.5 million cases were reported worldwide.
When we compare the first 6 months of 2017, we are talking about a 229% increase in 2018. Looking back to June 2014, security company McAfee revealed that ransomware attacks more than doubled in the first quarter compared to their 2013 record.
CryptoLocker, a Trojan designed specifically to attack Microsoft Windows systems, achieved major success in the cybercrime world before authorities eventually shut it down. Before that, CryptoLocker generated revenue up to $3 million.
The Internet Crime Complaint Center (IC3) reported around 2,474 ransomware attacks, resulting in losses exceeding $29.1 million. Statista made mention of $493 million being lost out of 623 million ransomware attack cases in 2023. To show how ransomware has changed the face of cybercrime, victims in 2019 lost $1.1 billion.
Revenue dipped slightly to $999 million in 2020 but rose significantly to $1.25 billion in 2023, marking a record high. Thanks to awareness campaigns and stronger action from authorities, ransomware-related losses dropped sharply to $813 million, a drastic decline from the previous year.
As awareness of ransomware grew, some victims refused to pay ransoms, which likely contributed to the sharp decline that year. In response, cybercriminals launched several new ransomware variants, which continue to pose a serious threat to innocent users.
During the pandemic period. Observers noted that most people began working remotely and relied on the internet for their jobs. The COVID-19 era led to a surge in Internet traffic. Of course, cyber criminals love where there is traffic.
Generally speaking, about 71 percent of companies have fallen victim to ransomware attacks over the years, with an average financial loss of $4.35 million per attack. In 2022, about 7% of organisations in the world faced ransomware attacks. This number rose 10 percent in 2023, showing it’s a trend that is gaining traction, which has come to stay.
Different Stages of Ransomware
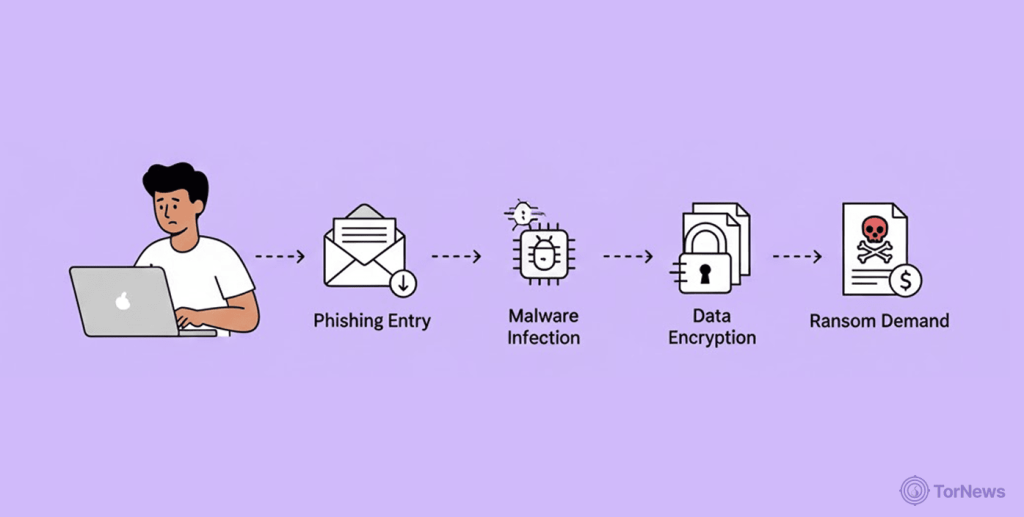
There are different types of ransomware out there, but all of them have these steps in common:
First Entry and Infection
Cybercriminals can compromise a victim’s Remote Desktop Protocol by stealing login information to access the system. That’s why experts advise using strong passwords and avoiding common choices, such as your own or family members’ birthdays.
Cybercriminals can use a direct approach, such as the WannaCry variant that exploited EternalBlue. Alternatively, they may rely on phishing emails that lure victims into clicking malicious links. Once a victim clicks the link, the ransomware downloads onto the computer and begins executing its intended task, taking control of the system.
Also, if the software used on the system has any vulnerabilities, these cyber criminals are most likely to check them out. In 2025, cybercriminals increasingly exploited vulnerabilities in third-party vendors. Attackers exploited any unpatched software on a supplier’s system to gain access.
The hacker can gain access through the stolen login details of the vendor. Once hackers achieve this, they exploit the trusted network connection between the vendor and the targeted organization. Because the organization has already vetted the supplier, the attackers can completely bypass its defenses.
Exfiltration, Encryption, and Execution
The moment ransomware has successfully downloaded into the victim’s system, what follows becomes very systematic. First, it starts to encrypt available files on the device. Prior encryption does not stop attackers from targeting the files.
The ransomware would take control of the encryption with an attack-minded key, giving them complete control of the files. Ransomware locks up your valuable files while leaving essential system functions untouched so that you can still operate the computer.
Depending on the ransomware version, some would delete any backup or copies of the files to make it more difficult for the victim to retrieve their data. With this option eliminated for the victim, they have no choice but to depend on the mercy of the hacker.
Demand for Ransom
Once the ransomware takes a foothold on the device system, it prepares to make a demand from the victim. There are lots of ways this can be done, but the most common way is for a text to be displayed on each of the encrypted file tags. Other hackers prefer the entire screen to display the ransom text.
Usually, this message demands a certain amount of funds in cryptocurrency. This mode of payment is very deliberate because cryptocurrencies are very hard to trace. Attackers require the victim to pay before restoring access to the files.
The hacker gives the victim the symmetric encryption key after receiving payment. Another way is to give the victims a copy of the private keys used for the symmetric encryption key.
The victim then enters this information into a decryption program. This too is provided by the hacker. The program will reverse the process, granting the victim access to their lost data or account.
These steps outline a typical ransomware attack. However, different ransomware variants may follow other paths or add extra stages. For example, WannaCry first scans for vulnerable devices, while Maze searches for data to steal, such as registry details and files, before carrying out the main attack stages.
Ransomware Categories
Over the years, this method of cybercrime has gone through changes over time, giving birth to new ways of doing it. Let’s briefly discuss them:
Data-stealing Ransomware
These are the sorts of ransomware that deal with data theft only. It’s swift, more efficient, and gets straight to important information. Hackers prefer this type of ransomware because it lets them avoid spending time compromising an entire system.
Another problem with encrypting the entire system is that the victim or company could notice what’s going on and initiate a countermeasure.
Double Extortion
This type not only encrypts the victim’s system but also combines it with data theft. Some victims refuse to pay the ransom despite a system breach.
In some cases, organisations will opt to retrieve information from their bank accounts. So hackers have learnt to steal the data also, with threats to release such information to the public if they don’t pay the ransom.
Triple Extortion
As companies become smarter and the refusal to pay ransom becomes a thing, hackers have added another style to the double extortion method. When the hacker comes across data that will affect the company’s customers, they go after them and threaten to release the information to the public. Triple extortion extends to the third party.
Ransom as a Service (RaaS)
This is a group effort by hackers. There are notorious groups of hackers with a very large network. When they spot potential victims, they can grant access to their malware to some of the hackers associated with them.
Once the ransomware attack becomes successful, the hackers will share the ransom from victims with the hackers who developed the malware.
Locker Ransomware
Attackers can deny victims access to their data by encrypting it. They can also lock the entire system or device, preventing use until the ransom is paid.
This method is more convenient as it saves time for the hacker and reduces the chances of the victim taking countermeasures. It’s swift.
Wiper
This type of malware is different from ransomware. Though it follows most of the process of encryption that’s found in ransomware, the goal is not to collect ransom.
The goal is to prevent the victim from having access to their data permanently. In some cases, attackers demand no ransom and instead delete the only key that can decrypt the compromised data.
Crypto Ransomware
Hackers often demand cryptocurrency payments to avoid detection, as these transactions are harder to track.
Ransomware Variants (Popular Ones)
Over the years, developers have created many ransomware variants with unique protocols that set them apart.
Some ransomware gangs have been very successful with some of these malware, while others have struggled with different ransomware.
Let’s look at some of the successful variants that have become very popular:
1. Lapsus$
This is a South American ransomware gang with a reputation for hitting very big organisations. They usually extort money from these high-profile targets by threatening to release sensitive information they have to the public.
This is achieved by using stolen source code, which is used to mask their malware and make such malicious files look legit. Some of the high-profile victims the gang has claimed to hit include Ubisoft, Nvidia, and Samsung, among others.
2. RansomHub
This ransomware gang was noticed in February 2024 and has since gained more popularity by adding members from other groups that were taken down, like LockBit and ALPHV.
Though payments were relatively low, the sharing model of funds in the group gave rise to more ransomware attacks like the types noticed in both July and August in the same year.
This Ransomware-as-a-service(RaaS) gang usually attacks businesses in Brazil and the US. The group built this malware using C++ and Golang, armed it with EDRKillShifter, and designed it for fast, remote encryption.
3. DearCry
Microsoft announced patches that showed four vulnerabilities in their exchange servers. This is where DearCry comes in. A new variant of ransomware, it was solely designed to exploit the vulnerabilities announced by Microsoft. Talk of washing your dirty laundry in public.
Instead of encrypting everything in sight, this malware targets only certain file types. When it finishes the job, a ransom note appears telling the victim to contact the hackers by email. That’s when they get the full rundown on how to pay the ransom and, if all goes well, regain access to their files.
4. Maze
When we talk about ransomware attacks that use the combination of encrypting files together with data theft, Maze was the first variant to do so. Because some high-profile organisations refused to play ball with the ransom, hackers found a way to steal data completely away from their system or device.
With the stolen data in their hands, the hackers have gained more bargaining power to force payment. If the company is still stubborn, the hackers can threaten to release the sensitive information to the public or, worse, sell it to the highest bidder on the dark web. In most cases, the victims have no choice but to pay.
The gang that used this variant has officially stopped their operations, with some of their associates moving on to other ransomware platforms like Egregor ransomware, which is believed to share the same source. With Mase and Sekhmet This means the ransomware attacks have not reduced in any way.
5. Akira
Probably one of the most advanced ransomware out there. With ChaCha2008 encryption, this variant was noticed in 2023. It was designed to support (rather than compromise) Windows and Linux operating systems.
The malware operates through phishing with emails to bypass systems. VPNs are not safe either, as Akira also exploits vulnerabilities there. Did we mention it was highly intuitive?
To climb up the privilege ladder without setting off alarms, the malware steals credentials and makes use of those trusted LOLBins already living on the system. And to fly under the radar of any firewall defenses, it encrypts files at random, irregular intervals instead of all at once.
Akira does not waste time encrypting the victim’s entire systems or files. Instead. Data theft and demanding ransom are what they are interested in. Going for the jugular. Large sums are demanded by the Akira group, which is why most of their victims are high-profile targets in Australia, Europe, and North America.
The sectors that are usually targeted are health care, education, finance, and manufacturing. Akira is one of the most elusive variants of ransomware, and that makes it very dangerous.
For organisations to protect themselves from this threat, they should conduct anti-ransomware measures, network segmentation, constant backup of data, patch management, and create awareness of cybersecurity.
6. Ryuk
This group was first noticed in 2018 and is responsible for making big ransoms from high-profile targets, a culture in the cybercrime world. For instance, their ransom demands are $1 million dollars on average for each victim.
Since big companies usually rely on back-ups to leverage not paying hackers, the Ryuk variant has been designed to delete file backups. It can also disable a system’s ability to make backups or restoration of deleted data. This goes a long way to force big companies to part with large sums of money.
The hackers are able to gain access to the victim’s system through phishing with emails or the victim’s login information (when it has been compromised). Once inside the system, the malware scans through all the files in the system.
The moment they spot certain categories of files and secures it, they lock out the victim from accessing the file. They are very careful not to tamper with files that help to stabilise the system. From here, the ransom is made known to the victim.
7. CryptoLocker
With a reputation of jump starting the modern-day ransomware attacks, CryptoLocker entered the stage of malware in September 2013. This ransomware is usually initiated through a network of computers that have been compromised (botnet) and is one of the early ransomware groups to encrypt victims’ files.
Before their operations were shut down by law enforcement in 2014, CryptoLocker managed to raise $3 million in revenue. After its demise, a lot of variants stepped into the stage, inspired by CryptoLocker. We are talking about variants like Petya, Ryuk, and WannaCry that later started the fever of ransomware attacks.
8. WannaCry
Exploiting the vulnerability in Microsoft Windows known as EternalBlue, WannaCry compromised more than 200,000 computers in 150 nations. This is the first cryptoworm ransomware with a high profile.
After gaining entry into the victim’s computer, it encrypts files, informs the victim of a threat to delete the files if ransom is not paid within days.
WannaCry has made its mark as one of the biggest ransomware attacks, with a record of about $4 million in revenue. WannaCry contributed to the boom experienced in ransomware attacks in modern Times.
9. Play
Since 2022, PlayCript, popularly known simply as Play, has attacked more than 300 organisations in the world, which include notable companies like the City of Oakland, Microsoft Cuba, and even the Swiss government.
They use encryption at irregular intervals on specific files. This helps them to avoid being detected by law enforcement agencies.
They also use double extortion, where, after encrypting the victims’ files, they steal them, taking them away from the system, and threaten the victim with releasing the information to the public if ransom is not paid.
The vulnerabilities that are exploited here are exposed RDP servers and FortiOS. It is from these weak links that they download their ransomware through Group Policy Objects as tasks that are scheduled.
Interestingly, they have a blog on the Tor network to make their attacks known, including the information they stole. This usually puts pressure on the victim to pay.
10. REvil
Speaking of ransomware attacks that are focused on big companies, REvil made its entrance in 2019. The Russian-speaking group has compromised big organisations like JBS and Kaseya and has been a strong competitor to Ryuk, striving to take the title of the most expensive ransomware attack unit. To buttress this point, REvil has been known to make demands of $800,000 from a single victim.
Initially, they began as a regular ransomware unit but later upgraded to using double extortion, where, after encrypting the victims’ files, they would also steal them. They would make ransom demands for the file to be encrypted.
Afterwards, they might still make another demand from the victim with the threat of releasing the decrypted files to the public. Ever wonder why their name almost sounds like devil?
11. Qilin
This one falls into the category of Ransomware-as-a-Service (RaaS) and is extremely customisable and known to hit different kinds of organisations in the world.
The variant was noticed in April 2025 when they topped the list of ransomware attacks. Just like the devil, sorry, REvil, they use the double extortion method of encrypting the victim’s files and data theft, with a threat to release the data to the public if ransom is not paid.
Some of the features used by Qilin include having lots of encryption modes, eliminating certain processes, changing filename extensions, and changing attack tactics depending on the type of victim they have targeted.
They have a platform on the dark web where they also announce their attacks and stolen data. It should be noted that after the fall of RansomHub, a lot of its associates joined Qilin.
12. LockBit
LockBit is another Ransom-as-a-service that was noticed in September 2019, and just like many of such ransomware, its target was usually high-profile companies.
The operation to compromise a system is so swift that IT/SOC teams, security appliances, and other security checks fail to see it in time.
13. Clop
A variant of Cryptomix malware(also a ransom-as-a-service malware), Clop is interested only in companies with very sensitive information, like finance and health care. It could be that the hacker noticed funds that came to the victim or company through an illegal entity, which could have legal implications. Perhaps, it’s the confidential health record of some high-profile persons in society.
At the mention of the release of such information to the public, we will know the double extortion method was used because they didn’t just stop at encrypting the files and asking for ransom to decrypt them, but went along with data theft as an insurance policy to get the victim to pay. How do they bypass security “checkpoints” in a system?
Two ways. By exploring zero-day vulnerabilities and phishing through emails. The malware spreads throughout the system this way, making it incredibly difficult to spot the attack. This variant specifically goes after corporate networks, leverages SDBOT for its operations, demands huge ransoms, and even digitally signs its code to appear trustworthy.
To avoid attacks coming from Clop, it is highly recommended that organisations have a solid authentication process, awareness training for the staff on phishing, locking away of infected files from the rest of the system, be observant of unusual activities, and also threat detection that is done by an AI.
How Ransomware Infects a System or Device

There are a lot of ways that ransomware can compromise systems:
1. Drive-by Downloads
The use of websites to transfer ransomware to devices has become a serious concern. Most often, the user isn’t aware of the mode of transfer or that their devices are hacked until it’s too late.
Websites that have already been compromised are used to check for vulnerabilities in the user’s web browser. They do this through exploit kits.
2. Phishing/Social Engineering Attacks
Most hackers use social engineering to execute email phishing. The potential victim gets an email that looks friendly.
They play on the psychology of the user to make them gain trust in the hacker, where they will finally be convinced to click on any link that is malicious. Of course, these links or attachments usually appear harmless to the visitor.
Other ways of transferring the malware are to convince the visitor to visit a malicious website and probably scan a QR code that transfers the ransomware into the visitor’s web browser.
3. Credential Theft
Hackers can gain access to the user’s account or files either through guesswork, going to the dark web to buy the credentials, and using them to log in to the user’s computer or network and transfer the ransomware to wreak havoc.
One major vulnerability used by hackers is Microsoft’s Remote Desktop Protocol (RDP), which is used to remotely gain access to a computer.
4. Operating System and Software Vulnerabilities
Every device’s operating system has vulnerabilities. The question is whether the patch has been updated. There is a vulnerability called a zero-day vulnerability.
This vulnerability isn’t known to most security communities or users, leading to patches being open for exploitation by hackers. Some ransomware gangs are known to go to Zero-day to buy flaws. The vendors are also their fellow hackers on the dark web.
These exploits are then deployed in devastating attacks. A prime example is the Cl0p ransomware gang’s breach of security giant Entrust, which was executed by exploiting a previously unknown (zero-day) flaw in an Oracle product, bypassing defenses entirely.
Patched vulnerabilities have been used as attack points successfully, as was the case with the WannaCry attack in 2017.
5. Other Malware
Not all hackers build their ransomware from scratch. Sometimes they borrow malware designed for other jobs. The Trickbot Trojan is a perfect example: it was originally built to steal banking logins, but attackers turned around and used it throughout 2021 to drop the Conti ransomware onto systems.
The Effects of Ransomware Attacks on Businesses

When successfully done, ransomware attacks could have a devastating effect on businesses that might have a ripple effect that’s damaging for its continued existence. Here are some of them:
Loss of Data
Given that most of these ransomware platforms don’t stop encryption of the victims’ files, data theft has become a thing where the victim loses some of their data even when the hacker has given them a decryption key. On rare occasions, there won’t be a ransom demand when data theft is done.
In some cases, that data isn’t coming back. Maybe the hacker has their own reasons for holding onto it. Maybe it’s personal. You never know, right? Or they might go through the whole song and dance of demanding payment, collect the ransom, and then simply never bother to restore access.
Dent on Brand Image
When an organisation’s system has been compromised, and it goes public, the brand’s image will be tainted, and it certainly leaves a bad taste in the mouth.
Customers or potential clients of the company will lose both trust and faith in the platform. And this could scare them away from fear of their own data being compromised, too.
Financial Loss
Organisations or individuals lose large sums of funds to these ransomware attacks, as we know. But also, the company can still lose money because its brand image has been dented.
They could lose customers they already have and stop potential customers from becoming ones. Either way, the organisation loses money on multiple fronts. We have not even started talking about legal fees the company could face or the financial cost of putting up better measures to manage future infections of their systems.
Data Breach
This poses a lot of problems. First off, having your data compromised is already a nightmare. But it gets worse—not only did the hacker encrypt your files, but they also stole them.
Downtime
After the damage done to compromise the data, the company will experience some downtime of their operations because the information that’s encrypted or stolen is needed for their operations.
This operational paralysis is the core goal of many cyberattacks, not just ransomware. Coordinated Denial-of-Service (DDoS) attacks, for instance, are explicitly designed to overwhelm and shut down critical public services, causing massive disruption without the need for data theft or encryption.
Legal Penalties
For a ransomware attack to actually succeed, there had to be some kind of slip-up somewhere in the organization. And those overlooked gaps? They might have violated internal policies—or even opened the door to lawsuits down the line.
The Most Common Victims of Ransomware Attacks
Ransomware attacks can be done to any organisation, no matter area such organisation covers. But bad actors have preferences. Let’s find out the ones they favour the most.
1. Manufacturing
According to a security report by IBM in 2024, these industries are some of the most attacked by ransomware. This makes ransomware and other malware to be considered the highest threat in the cyber world.
Applied Materials, a well-known corporation in the US worth billions of dollars, announced a ransomware attack on one of its suppliers in February 2023. This attack cost them about $250 million.
Vulnerabilities in the supply chain continue to increase because most organisations don’t have a solid security protocol to counter such malware. That’s why hackers continue to exploit this weak link.
Attacks on software supply chains amount to 12% of such while attacks on business partners are responsible for 16% in 2023, according to an IBM security report on data breaches. In this report, it was stated that a supply chain breach costs 11.8% more and takes up a lot of time, about 12.8% more than usual before the threat is recognised and contained.
2. Health Care Industry
Arguably, the most lucrative industry for hackers. The highest number of compromised systems took place in the health department in 2023, and has never been that frequent since 2019.
Seeking for financial gains is what prompts these hackers to breach health institutions. For instance, when a medical record has been stolen, it can be used to have illegal access to get medical prescriptions or data.
On average, the health care departments have heavily to ransomware attacks, much more than the other industries. As can be seen from IBM’s report on the cost of data breaches, the medical industry lost $10.93 million to hackers in 2023 alone.
Let’s get to human error. This alone contributed to the highest reason for data leaks in health institutions in 2023, 28th makes it easy for hackers to pounce on them with their malware.
It would surprise you to know that threats from malicious hackers were no longer on the top three list of cyber threats in 2023. The top three most common causes of data breaches in that year were miscellaneous errors, system intrusion, and web application attacks.
Though not in the top three causes, vulnerabilities from third-party apps have proven to be a great concern in recent times.
3. Finance and Insurance Industry
Financial institutions are very much aware that they would be a prime target for hackers because of financial gains.
That’s why they have taken measures to counter such attacks by managing whatever vulnerabilities that exist in their systems, including TPRM (Third-party risk management). Bottom line, it’s very difficult to hack into banking systems.
But trust hackers, they always find a way. A lot of attacks on financial institutions are done through web applications. Because lots of people use web applications, it makes it very difficult for the victim to detect or even trace after the deed has been done.
A report by Verizon in 2023 showed that insiders are responsible for 34% of breaches in the financial sector. The IBM report previously mentioned also states that the financial institutions have recorded the second most expensive ransoms per victim.
Threats from outside increased for financial organisations from 2018 to 2023, which was significantly more when compared to attacks from the inside. It should be noted that threats from insiders continued to grow within this period, while attacks from outside dropped over time.
4. Education and Research
As technology keeps growing, educational institutions have seen how easy it is to manage and keep data digitally. But it comes with a disadvantage. Now they are exposed to bad actors online.
What do hackers compromise? Physics lessons? Actually, the hackers target research data, personal information of employees or students, faculty details, and financial records. This industry was in the top ten for money lost to hackers in 2025.
The misconfiguration of databases for knowledge is one of the leading causes of cyber attacks in this industry, especially when they lack access control. Hackers can get their hands on lots of information in the education system, which can be research data, accounting information, health records, PII data, and bank transfer details.
One notable example is what happened at Connecticut College in March 2023, where personal information of both students and teachers alike was leaked because of unauthorized access by an entity.
5. Energies and Utilities
Just like the educational sector, the energy and utility industries have seen the need to go digital with their operations, giving hackers the opportunity to look for vulnerabilities in their systems.
According to a report by Rockwell, industries in the energy category are attacked 3 times more than any other infrastructure departments. Looking at things from a general point of view, the energy sector is the fifth most attacked industry in the world.
Attackers usually target operational and utility companies because they provide essential public services. Shutting them down temporarily will put such organisations under immense pressure from the public. Once their operations are shut down, time becomes their greatest enemy.
The pressure from the public gives the hacker enough leverage to ensure the victim pays the ransom. Attackers shut down systems using remote service exploitation, phishing, and ransomware. Most of the breach comes from IT compromise.
An unusual situation occurs every now and then. Nearly 60% of the attacks done on energy and utility departments are carried out by associate groups in the country. Infiltration that is led by persons in the government.
A third of them came from personnel inside the organisation. In 2023, Stellafield, the UK’s most dangerous nuclear site, reported a breach carried out by cyber groups allegedly linked to China and Russia.
A sleeper malware has been compromising the site’s IT system since 2015. Experts remain uncertain about how long it has been installed or who is responsible.
6. Public Administration
This industry isn’t immune to cyber attacks either. Government data theft is highly profitable, making it a prime target for hackers. Or espionage? That too.
Sensitive information has been stolen from government databases, such as the case where a Russian state-sponsored hacker group infiltrated U.S. defense contractors. From January 2020 to February 2023, they stole both communications and military infrastructure data.
Russian cybercriminals have attacked numerous federal institutions, targeting sensitive data that could benefit foreign governments. Sponsored cyberattacks are now a key tool in espionage.
7. Retail
Business transactions have always been an attractive enterprise to criminals. As technology advanced in the modern world, people did their transactions digitally. Criminals have also moved their malicious activities over to the digital world.
Retailers have experienced a lot of cyber attacks, and most especially from card skimmers and DDoS attacks on both their websites and stores.
The most frequent reason for cyber attacks on retailers is a low quality standard in security. This is because in most cases, retailers use third-party platforms for security services. They rarely bother with security themselves. Negligent.
Card transactions have become a major target for cybercriminals, accounting for 37% of breaches experienced by retailers.
How to Prevent Ransomware Attacks

The need to stop or at least to reduce the effects of ransomware attacks cannot be overstated. We have discussed extensively on some of these negative effects. Now is the time to address how to manage these threats.
Cyber Education and Awareness Training
Most cyberattacks are carried out via phishing emails. Companies and institutions should train their staff on how to identify these threats. The hackers could initially send mail that has no malicious content.
This will make the user trust the bad actor. When the hacker sees the user trusts them, they will send an email with a malicious link, telling the user the link comes with good intentions.
Staff need to know all these to be able to detect these threats long before they become a problem. Training programs are the first crucial step in managing cybercrime attacks.
Authentication of User
This is where two-factor authentication becomes very useful. Using strong passwords helps prevent hackers from stealing login credentials.
Avoid using the date of birth, either yours or that of your child. It’s easy for hackers to get such information and try it out as your password. In most cases, it works for them.
Continuously Backing Up Data
To ensure the victim has no other option but to pay the ransom, hackers not only encrypt or steal data but also wipe out any backups they see. When a user has a backup, there is a chance they won’t pay.
It’s important to do as many backups as you possibly can. Automated, regular backups are ideal. It doesn’t just help to avoid payment but also reduces complete data loss.
Patching
Most vulnerabilities come from unpatched software, and hackers constantly look for these gaps to exploit. Using an unpatched system is like putting a target on your back. Keeping software updated with the latest patches reduces the risk of a breach.
Reduction of Attack Surface
There is a saying, “prevention is better than a cure,” and this goes for cyber threat management. Prevention is always the best way to stop attacks:
- Mobile malware security protocols
- Setting up email protection against phishing emails, like Harmony Email Security
- The use of external risk management, like Check Point ERM
Use Anti-Ransomware Solutions
The fact that ransomware can encrypt all the files in a user’s system means the malware has a signature when going through the system.
An anti-ransomware system can detect threats before they cause damage.
You can tell a good anti-ransomware solution by the following qualities:
- A restoration method that does not rely on tools like Shadow Copy, which are very common and usually exploited by hackers.
- A broader detection of ransomware variants
- Automated restoration
- Quick detection
Management of Active Ransomware Infection

- Quick backup: The good news is that some variants of ransomware can allow the user to unlock some of the data while the infection is ongoing. Once you unlock, back up those files and store them somewhere that is outside your computer. It keeps the files safe from damage.
- Wipe and restore: Once you have saved your files outside the computer, wipe off everything(a factory reset). The ransomware will be removed, along with any programs that weren’t preinstalled on the system. Then go back to the external storage and restore back your data to the system. We should point out that after this, you should take measures to ensure such malware attacks don’t happen again. Once beaten, twice shy.
- Quarantine the computer: Doing this can only work if you have detected the infection and acted quickly. If you notice a breach, immediately disconnect the system from other devices. There are variants of ransomware that work their way up from the infected computer to other devices. This measure isolates the infected machine from contaminating other machines.
- Do not switch off: Contrary to what you may think, it’s better to leave the device on while the infection is taking place. Turning off the device during an infection can damage its memory, making it harder to recover data after the attack.
- Availability of decryptors: At times, a platform called No More Ransom Project might have free decryptors. Always check for available tools to decrypt your files to avoid paying a ransom to hackers.
- Seek help: If you didn’t make a backup of your precious files, your device, at times, stores a backup on its own. Ask for help from people who know better about computers to help to restore some of those backups.
Key Strategies to Prevent Ransomware Attacks
- Use a good security check: Using a security system that has a lot of layers will be of great help. It could have email security, web filtering, and firewalls. Sandboxing separates applications from others to safely check for breaches.
- Frequent updates: Regularly updating apps blocks potential vulnerabilities. In most cases, updates take care of old vulnerabilities. If the operating system of the device brings security patches at intervals, please always update those.
- Awareness training: Training workers should be done to stop attacks. Human mistakes can open up doors for these criminals to get into their system. They should know phishing emails before they cause any damage.
- Backup data: Do you know why having a backup is important? That’s because it will help you to get back some of your lost information instead of losing everything. With the information you were able to get back, you can get back to work with them, and this helps to reduce downtime.
- Reduce business interruption with security protection: Ransomware is something nobody wants to experience. You should use tools like Fortinet Ransomware Hub. With this tool, you can rest easy, knowing your work is safe. A lot of people or companies don’t know how fast ransomware attacks can be, and that is because they lack training to create awareness of the dangers. A security tool is very important.
- Install antivirus protection: A good antivirus is a recommended first step to take to protect your device from malware. Filters from emails help to stop dangerous attachments from getting to the user. Also, as you update your apps, also update your antivirus to keep tabs on new threats.
- Legal software: When installing apps, make sure you download the ones approved to work on your system. The firewall usually alerts the user if new software doesn’t meet up with the approved standard of apps. If you suspect something fishy about the new app, delete it as soon as possible.
- Authenticate software: When you are not downloading and installing apps from your app store, you need to be careful. Installation of third-party apps should come from verified platforms. Hackers always use third-party apps to find vulnerabilities.
All in all, ransomware has become a major concern for everyone who uses the Internet or the digital world, with many folks becoming victims. As technology gets better, cyber criminals find smarter ways to bypass file securities. Ransomware affects most businesses, and some even go bankrupt as a result.
Well, there is good news. There are countermeasures you can take to secure your files from these bad actors, including how to manage the damage during or after infection.
The most important countermeasure is to create awareness of the danger by training the workers on how to identify such threats. Check Points remain the most effective tool to push back on ransomware attacks in 2026.
FAQs
Yes. Reboot the device to safe mode. That’s when you will try to install anti-ransomware and use it to scan the system. It will remove the ransomware the moment it sees it. Also, verify that your backup files are not damaged.
If you’re hit by ransomware, you can report it through official government channels—like CISA’s online form or the FBI’s IC3 website. These are the places where authorities track cybercrime and jump into action.
Pretty much anybody, but these days, it’s more of organisations, business platforms, and government institutions.
They can be called crypto trojans, encryption trojans, or blackmail trojans.