When it comes to safeguarding your privacy, do you really know what and how to achieve it? You could be missing an essential ingredient. Onion Routing is the revolutionary technology that encrypts your connection layer after layer making denial of privacy almost impossible.
It is the backbone of Tor (The Onion Router), and the foundation of authentic online anonymity for bloggers, journalists, activists, and anyone that takes digital security and privacy seriously.
We break down exactly how this system works, compare it head-to-head with a VPN, and provide you with our step-by-step guide on using it when browsing normally or when visiting sites that a normal browser couldn’t navigate.
What is Onion Routing?

Think of onion routing as sending a secret message. It cloaks your data in several encrypted layers that makes it impossible (nearly) for anyone to trace the message back to you or see its final destination.
Let’s briefly x-ray the onion routing process and how it works.
Understanding Onion Routing
When you are browsing, your computer connects directly to the server of a website. This connection allows your Internet Service Provider (ISP) and sometimes the actual website, to see your IP address and quickly track where your data is originating from, and where it is heading.
Onion routing is an innovative technique that prevents that from happening. It is a privacy-enhancing technology that encrypts data in multiple layers, similar to the layers of an onion, and routes it across multiple network nodes, or onion routers. Onion routing secures your online activity and the content within it.
You can think of your data packet as a letter you want to send privately. Onion routing wraps the letter in several envelopes, each of which is addressed to a different post office that serves as intermediaries and is sealed to minimize the chance of opening. Only when it is received at each post office can they open the envelope, rewrap the letter, and send the letter to the next intermediary post office.
This approach of using multiple layers prevents one point in the network from seeing the origin, the destination, or the content of the letter. No ISP, no government agency, or even the server where the letter is heading, can tell simultaneously where the letter came from, where it is headed, or what the content is. That is the basis of Tor (The Onion Router).
The Genesis of Digital Layers: A Brief History
Onion routing didn’t emerge from a cadre of underground hackers; rather, it appeared in the mid-1990s out of the U.S. Naval Research Laboratory. This technology was developed by researchers Paul Syverson, Michael G. Reed, and David Goldschlag to safeguard U.S. government communications and intelligence on the Internet.
The goal was to create a way for agents to communicate and browse the web without the risk of surveillance or their location being revealed. Later, the technology was adapted for public use with the development of the open-source Tor Project, turning a powerful military tool into the cornerstone of online privacy advocacy for the entire world.
The Core of Onion Routing – Quick Explanation Table
| Feature | Description | Key benefit |
|---|---|---|
| Layered Encryption | Data is wrapped in multiple encryption layers, like an onion. | No single node knows both the source and the final message content. |
| Decentralized Network | Uses a series of relays operated by volunteers (Entry, Middle, Exit). | This ensures there is no central failure or control in operation – making it very difficult to shut down. |
| Anonymity | Conceals the IP address of the users from the destination server. | Secures the identity of the users from websites and network observers. |
| Latency | Slower than a standard connection due to the multi-hop process. | The cost of maximum privacy and resistance to traffic analysis. |
How Does Onion Routing Work?
Onion routing is a unique, simple, and powerful mechanism to encrypt your data, then transmit it through a distributed network made up of volunteers who run their relays.
Here are the steps involved in anonymizing your internet traffic:
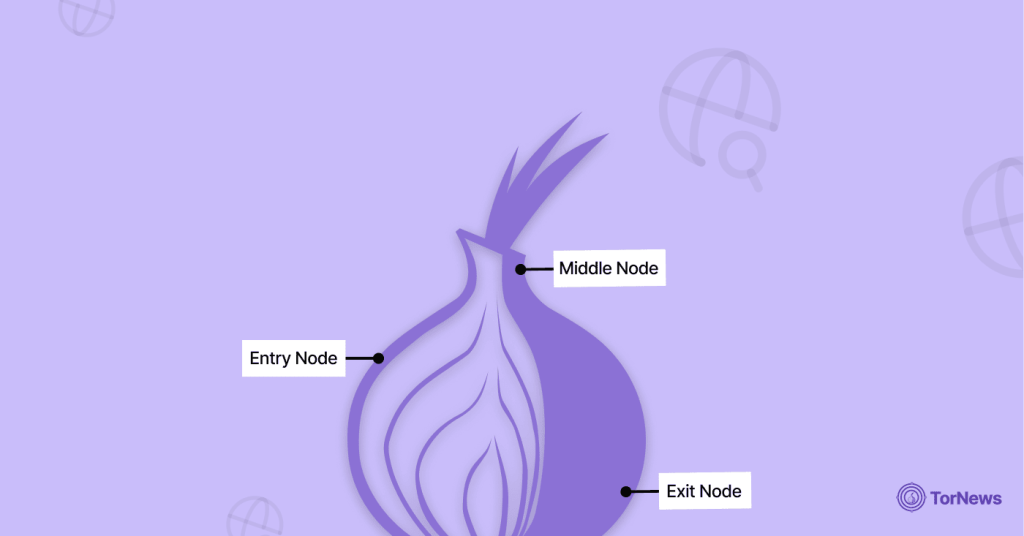
The Three-Hop Journey: Entry, Middle, and Exit
The Three-Hop Journey: Entry, Middle and Exit
Once you connect to an onion routing client (like Tor Browser), your data is relayed along a randomly selected path through at least three specific node types:
- Entry Node (Guard): This is the first node to which your encrypted traffic connects. The Entry Node can see your real IP address, but it only sees the outer layer of encryption, not the end destination you are trying to access. The main job of it is to pass the data onto the next node.
- Middle Node (Relay): This node takes the connection from the Entry Node and strips off one layer of encryption before sending it on to the Exit Node. The Middle Node knows neither your real IP address nor the website you connect to; but only knows the Entry Node and the Exit Node.
- Exit Node: This is the last stop. It removes the last layer of encryption and therefore displays the original (decrypted) data. It can see the content and the final destination address but does not know your original IP address. It only knows the address of the Middle Node. The Exit Node will then send the traffic to the destination website.
Because no single node knows both your identity (IP address) and the final destination, it is extremely difficult to trace the communication back to the original source.
The Magic of Layered Encryption
The “onion” analogy is meant to be precise. The data is encapsulated in three encryption layers, each one secured to a node:
- As your client (for example, Tor Browser) establishes a connection, it completes encryption for the Exit Node first, followed by encrypting again for the Middle Node before encrypting again for the Entry Node.
- The Entry Node peels away the outer layer revealing the address of the Middle Node. It passes the still-encrypted bundle to the Middle Node.
- The Middle Node peels off its layer, revealing the address of the Exit Node that it then sends along with the data.
- The Exit Node peels off the final layer and reveals the original unencrypted request (unless it has HTTPS) and sends that request to the final destination server.
Anonymity Achieved
Through the layered process as described above, you will achieve structural anonymity, which is part of onion routing.
By routing your data through multiple independent, unique, volunteered-operated relays, as well as incorporating layered encryption, it becomes extremely difficult for any one entity, even information which monitors multiple locations, to identify the original source of your data, or connect it to the destination of the data.
What are Real-world Applications of Onion Routing?
Though typically associated with the dark web, onion routing serves important, legit functions in many fields:
| Application type | Examples | Description |
|---|---|---|
| Anonymous communication platforms | Tor Messenger, Ricochet | These applications use onion routing for encrypted conversations and protect the identity of every participant in the conversation. |
| Secure browsing tools | Tor Browser, Onion Browser | These applications engage onion routing to access the normal (surface) web without revealing their IP address, so that ISPs or websites cannot track them. |
| Bypassing censorship | Accessing blocked news sites, social media | Onion routing is a fantastic way for users to circumvent censorship firewalls and create experiences of a free and open internet when they are in a country that limits access through government-sponsored censorship of the internet. |
| Surveillance resistance | SecureDrop, GlobalLeaks | Accounts use onion routing to allow whistle-blowers and journalists to provide a means to submit articles and content while maintaining anonymity in fear of being identified through the submission process. |
Seven Key Features of Onion Routing – Its Pros
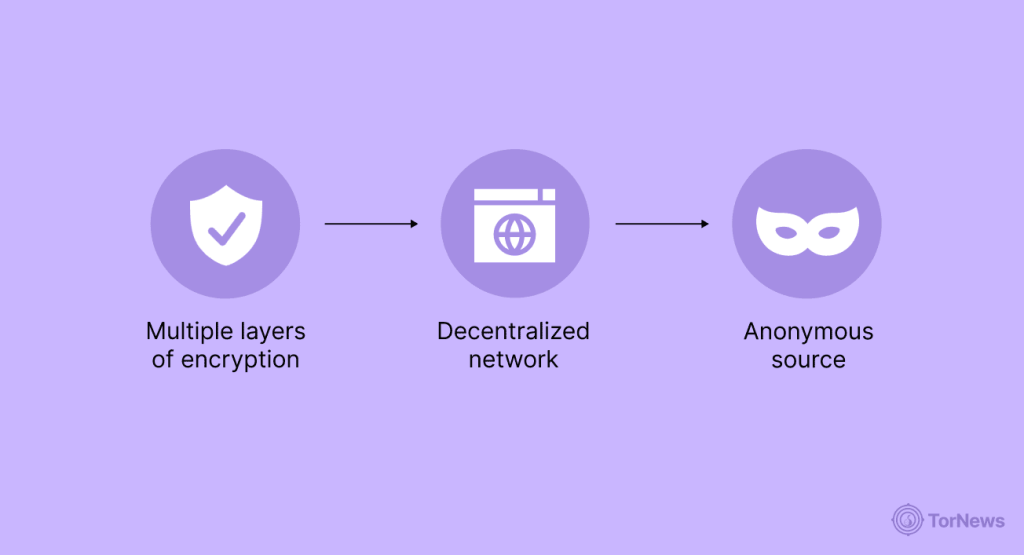
The architecture and design of onion routing provide some useful features:
- Multiple layers of encryption: Data is categorized within many layers of encryption, meaning no one relay is ever aware of both the source of the traffic and the end destination.
- Decentralized network: The network is operated globally using thousands of relay nodes run by volunteers, and thus is very robust to shut down and control.
- Anonymous source: The user’s original IP address is not disclosed to the destination server and to some of the relays in the circuit.
- Destination anonymity (hidden services): The network supports “Hidden Services” (known as .onion sites) where both the service provider and the user remain anonymous, as traffic never leaves the Tor network.
- Traffic eavesdropping protection: No single node is unconditionally trusted, but layered encryption keeps eavesdroppers on any single hop from reading the entire contents or knowing the entire path.
- Trustless operation: The system is constructed, so that the user does not have to trust any single relay will to keep them anonymous, but only trusting that no single powerful entity can compromise all relays in the path.
- Censorship circumvention: Citizens in certain regions gain access to the network that may allow them to bypass local filtering to access either the public Internet or private services.
Potential Risks and Downsides of Onion Routing – The Cons

Onion Routing can be a powerful means for anonymity, but it has various built-in downsides and risks:
- Slower speed: The process of routing data through multiple relays and completing multiple rounds of encryption/decryption process comes with significantly higher latency, making it slower than direct connections or standard VPN connections.
- Weakness of exit nodes: The Exit Node is where traffic is decrypted. If the connection from the exit node to the ultimate destination is not HTTPS, then an attacker controlling the exit node could snoop the final data (such as log-in credentials).
- Traffic correlation attacks: An adversary that is both global and wealthy (e.g., a state actor) that can effectively control or monitor a statistically relevant number of entry nodes and exit nodes could theoretically perform a traffic timing and pattern analysis of traffic to de-anonymize users.
- Blocked access: Numerous websites, services, and even entire networks (i.e. corporate, academic sites) will block traffic from Tor exit nodes based on an association with illegal activities. Such access is mostly blocked with a CAPTCHA or some other response denying access.
- Risk of malicious software/exploits: The Tor Browser is a modified version of Firefox, and vulnerabilities inherent in the browser or third-party plugins could provide an avenue for de-anonymization of users.
- Suspicion of use: In some countries or with some Internet Service Providers (ISPs), the act of using the Tor network raises suspicion or is considered evidence of intent for illegal activity regardless of whether the user is involved with legal, protected speech.
Tor vs. I2P: What is the Differences Between Onion and Garlic Routing
Tor and the Invisible Internet Project (I2P) are both anonymity networks; however, they differ in their routing protocols and they serve very different purposes.
| Features | Tor: The Onion Router | I2P: Invisible Internet Project |
|---|---|---|
| Technique of Routing | Onion Routing (Layered Encryption) | Garlic Routing (Bundling Messages) |
| Primary Focus | Anonymous access to the Public Internet (Clearnet) and Hidden Services (.onion) | Anonymous communication within its own network (eepsites/.i2p), with clearnet access being secondary. |
| Type of Circuit | Bi-directional (Traffic flows to its destination and back along the same circuit.) | Uni-directional (Separate, single path tunnels for inbound traffic and outbound traffic to make traffic analysis more difficult.) |
| Encryption Unit | A single message is wrapped in multiple layers of encryption. | Multiple messages (cloves) are bundled together into a single encrypted packet (garlic). |
| Network Structure | Directory-based (More centralized in the beginning for network status). | Fully Distributed (No centralized directory, no authority). |
| Speed | Fastest in accessing the public internet, being a larger, better optimized network. | Generally slower for clearnet access, but faster for internal network services. |
In Summary:
- Tor (Onion Routing): Best for users whose desire is to safely browse the public internet or access .onion sites. Its bi-directional circuits and single-message encryption is fast and suitable for browsing the web.
- I2P (Garlic Routing): The design to deliver an anonymous and self-sustaining network that enables secure service (websites) hosting and communications. I2P provides unidirectional tunnels and bundled messages (garlic routing) distinctly, but always focuses on resilience and privacy in the network.
Onion Routing vs. VPNs: Which is Better for You?

Both onion routing (Tor) and a Virtual Private Network (VPN) are measures of online privacy, but they operate on fundamentally different principles, and offer different forms of anonymity. This is often the moment where someone asks, “Onion routing vs. VPN?”
The Core Difference: Decentralized vs Centralized
- VPNs are based on a centralized model. You access a secure server that is owned and operated by an organization. Your traffic is encrypted from your device to the server, which provides you with a new IP address. You are anonymous based on trusting the VPN service entirely.
- Onion Routing (Tor) is based on a decentralized model. Your traffic travels through a random path of three (or more) volunteer-operated nodes. Your anonymity relies on the impossibility of knowing the entire path from any single volunteer node.
Speed, Trust, and Use Case Comparison Table
| Feature | Tor (Onion Routing) | VPN |
|---|---|---|
| Anonymity level | Extremely High (Multiple layers of encryption over a decentralized network) | Moderate to High (Single layer of encryption over trusted provider) |
| Speed | Very Slow (Because of the Multiple hops and encryption/decryption) | Fast (Very little speed loss, perfect for streaming/downloads) |
| Cost | Free (Volunteer-run/non-profit) | Requires a subscription for a reliable service |
| Trust requirement | No need to trust a single entity (trust is distributed across relays). | Requires absolute trust in the VPN provider’s no-logs policy. |
| Traffic visibility | ISP sees you are connecting to a Tor Entry Node. | ISP sees you are connecting to a VPN server. |
| Use case | Whistle Blowing, political activity, visiting .onion sites, maximum anonymity. | Typical secure browsing, geo-blocked content, streaming, P2P file sharing. |
The Hybrid Solution: Onion Over VPN
With the highest level of security, many users combine the two options. This is often called Tor Over VPN or Onion Over VPN.
- Firstly, connect to your VPN server.
- Then, you start your Tor Browser.
This obscures your original IP address from the Tor Entry Node, which is (usually) the only portion of the Tor network that knows your true location. The added bonus is that your Internet Service Provider does not know that you are using Tor, providing a new level of privacy.
What are the Limitations of Onion Routing?
Amid its helpful uses, onion routing is not without limitations, and knowing them will ensure your proper usage of the technology.
The Speed Trade-Off
The most obvious and unavoidable limitation is the slow speed of browsing your onion routed connections. Your data has to be encrypted and decrypted three times as it travels through at least 3 relays (most often run by volunteers with limited bandwidth) every time you use it.
So the latency can become significant and can make many activities or functions dependent on data (like streaming video or downloading large files) very irritating.
Exit Node Vulnerabilities
The traffic is encrypted only while inside the Tor network. Once your data passes through the Exit Node, the data is sent to a standard non-HTTPS website without encryption. Hence, the Exit Node operator can practically eavesdrop on your data if you are using a non-secure (HTTP) site. This assumption is why the use of Tor and end-to-end encryption (such as HTTPS) is a requirement.
Incomplete Anonymity & User Error
Onion routing provides anonymity at the network level and cannot protect you from your own identity-revealing actions:
- Logging into your personal email or social media accounts while using Tor.
- Using your identifiable credentials across different sites.
- Browser exploits (see below) and/or not keeping your software up-to-date.
- Using any application other than the Tor Browser unless the application is specifically designed for use on the Tor network.
Can Attackers Compromise Onion Routing?

Although the onion routing protocol is highly sophisticated, no system is completely secure. Advanced adversaries, particularly those that are state-sponsored, can conduct complex adversarial action leveraging the capabilities of onion routing.
Correlation Attacks
The most complex and resource-heavy attack is the Correlation Attack. An adversary who controls or monitors a large portion of the network, specifically both the Entry Node (seeing you connect) and the Exit Node (seeing the traffic leave), could attempt to correlate the timing and volume of the traffic flowing between the two points.
If the patterns match, it can lead to the de-anonymization of the user. This is a complex, but possible, attack for highly-funded entities.
Exploiting Software Vulnerabilities
Another method threat actors can utilize is exploiting any vulnerabilities that are discovered within the client software itself, mainly the Tor Browser. In the past, for instance, law enforcement used malware to compromise the software Tor Browser users relied on to do an investigation resulting in revealing the user’s actual IP address.
This is an example of understanding why using the latest Tor Browser software is important, especially if there is a patch related to a vulnerability because of that software being used.
How is Onion Routing Connected to the Dark Web?
It is the core technology that makes the dark web accessible. The dark net is defined as part of the web that has intentionally hidden content that can only be reached with specific software (primarily the Tor Browser). With the Tor network, the client connects and becomes invisible to all—including your Internet Service Provider (ISP).
.onion Sites and Hidden Services
The dark web sites with the special top-level domain .onion. These are known as Onion Services (or “hidden services”).
These Onion Services use the same routing protocol to hide their location. This means the server hosting the website is as anonymous as the user accessing it. The benefits of Onion Services include:
- Location hiding: Hidden/obscured IP address of the server location is guaranteed.
- End-to-End authentication: The user can be confident that the content received when reaching an .onion address is from that service and not an entity impersonating it.
These sites aren’t indexed by Google, and finding them requires specialized tools. Find out which dark web search engines are the most effective and private in our guide.
This type of anonymity is one of the functions of the dark web’s design that allows a person or a collective to go public and publish anything they want, without fear of one-of-a-kind censorship or backlash from the same entity.
How Can You Use Onion Routing Safely

While the Onion Routing protocol provides strong anonymity, the effectiveness of Onion Routing is very dependent on how it’s used; hence, you must follow operational security best practices to protect yourself best.
Operational Security Best Practices for Maximum Anonymity
- Use a VPN in conjunction with Onion Routing (Tor Over VPN): As mentioned earlier, connect to the VPN before you connect to Onion Routing. This will keep your ISP from knowing that you are using Onion Routing – this is another potential level of security, possibly related to your IP.
- Keep the Tor Browser updated: Make sure that your browser is up to date to take advantage of the latest security updates against known vulnerabilities.
- Disable Scripts and Plugins: Tor Browser has built-in user’s capability of switching between levels of security. Use the “Safest” security level to disable JavaScript and other browser plugins which could be abused for fingerprinting or de-anonymizing.
- Do not log into any personal accounts: While using Tor, never log into any service that could link your real identity (your personal email, Amazon, social media) to your use of the browser. You want to keep your anonymous use of Tor separate from your real identity.
- Use bridges if necessary: If Tor is blocked in your country, you can use Tor bridges as unlisted entry points in some instances of country-leveled censorship. Use the bridge if you want to access the network invisibly.
- Always use HTTPS: Make sure the web pages you visit use HTTPS. This helps to keep your traffic encrypted even after it leaves the Exit Node. It protects you from compromising malicious Exit Node operators.
Is It Legal to Use an Onion Router?

This is one of the concerns about the technology, and the general answer is yes, but it has crucial context.
In the vast majority of countries, there is nothing illegal about just using the Tor Browser or Onion Routing technology.
It is being lawfully used every day by:
- Journalists who want to protect their sources.
- Activists and human rights defenders communicating in a surveillance-heavy part of the world.
- A business doing market research and protecting its location.
- Regular people who care about their privacy from corporate tracking or mass surveillance.
The association of the network with the dark web and illegal acts still may make the use of the network more suspicious to authorities in some districts.
Regardless of Tor’s legal status as a tool, you can still be arrested for any illegal activity you were engaged in while using it. Always be conscious of local laws related to encryption and privacy tools when in your jurisdiction.
Final Word
Onion routing is much more than the technological foundation of the dark web; it is a powerful technology that upholds privacy and free expression in a digital world. Onion routing offers anonymity that would not otherwise be available via traditional VPN or browsers by wrapping your data in layers of protection while routing information across a decentralized and worldwide network.
Understanding the Onion routing protocol, what it is, how it is not fast, and how to prevent risks like Exit Node compromise establishes the ability to reclaim your digital life.
When used properly and responsibly, these tools like the Tor Browser can allow individuals to communicate and browse the internet confidently knowing they are using one of the most advanced protections against surveillance and censorship today.
FAQs
Tor means The Onion Router. It refers to both the open-source software project and the global, volunteer operated network using onion routing. Tor Browser is the popular software that almost everybody uses to connect and do stuff using Tor via the web.
The least complicated and safest way of initializing onion routing is to download and install the Tor Browser. This is just a modified version of Firefox that has the default Tor protocol to work with any complexities of running the onion routing protocol. Once installed, the Tor Browser will ensure your browser traffic is always routed through the Tor network, handling the entry, middle, and exit relays for you in the background. Another option is services like NordVPN with “Onion Over VPN” feature, in which Tor functionality can be accessed through the VPN app instead of a browser.
An Onion Service is essentially a website or some other kind of service that operates through the Tor network on .onion domain suffixes. An Onion Service, like other Tor services, aids in the anonymity of both the service provider and the client by using onion routing in the background to hide the true location/IP address of the user.
No. While both tools aim to protect your privacy, the Tor Network is decentralized and is multi-hop routing for the utmost anonymity and expression, which results in slower speed. A VPN is centralized and is a single-hop routing that aims to find a balance between security and speed, which is better for everyday activities like streaming and downloading.