The dark web is a network of hidden websites that operate outside the reach of standard browsers and search engines. Buying or trading on the dark web is inherently risky. The anonymity that defines it makes verifying anyone’s trustworthiness nearly impossible, especially when dealing in illicit goods or services. To reduce these risks, many marketplaces rely on reputable escrow services, a trusted third-party that holds funds until both parties fulfill their part of the deal. This ensures that neither side gets scammed. Yes, criminals and scammers scam each other, too.
In this guide, we’ll break down how escrow works on the dark web, the step-by-step process of using it, common types of escrow systems, and tips to avoid fake or malicious escrow sites. Whether you’re researching dark web operations or exploring cybersecurity concepts, understanding escrow is key to grasping how trust and transactions function in the hidden internet.
Disclaimer: This guide is for informational and cybersecurity research purposes only. We do not endorse or encourage any illegal activities.
What is Escrow?
Basically, escrow is a simple idea. It’s a financial arrangement where a neutral third party holds payment while two anonymous parties buy and sell goods or services, ensuring neither side can cheat the other. The intermediary only releases the funds once both parties fulfill their obligations according to the agreed-upon terms.
In the surface web, a trusted intermediary is common, for example, when buying a house. The funds are held until all terms are met. On the dark web, the same mechanism secures transactions for illicit goods or services, where legal recourse doesn’t exist. This ensures the seller can’t run away with your down payment and that the seller has confidence that you will follow through on purchasing the item.
On the dark web, the idea is the same, but the stakes are higher due to the total absence of legal recourse and the prevalence of sophisticated cybercriminals. Here, the holding service becomes your essential protector.
The seller lists the item for sale. You agree to purchase the item. Instead of sending your funds directly to the seller (the scary move known as “finalizing early”), you send them to the payment intermediary that the darknet platform provides.
Because the seller knows their funds are locked in, and they know they’re going to be paid, they ship your item. You get the package, you inspect it, and as long as it’s as described, you tell the payment intermediary to send the funds to the seller. If it isn’t as described, your money doesn’t move.
You have leverage. Have got a voice. You have a fighting chance. By using secure payment lock services, you leverage a leap of faith into a formal, secure system. It is the difference between handing cash to a stranger in a darkened alley and using a secured, monitored drop point.
How Does Escrow Work on the Dark Web?

Escrow transactions on a well-maintained dark web marketplace are typically very efficient. The goal is to provide a very low-friction experience to transact securely. Here’s the full lifecycle of a standard deal.
The life cycle of a dark web escrow transaction:
- The agreement: You are browsing the platform and locate a product you wish to purchase. You determine the seller is reputable (more on this below) and you accept the price. You add the item to your cart and to the checkout process.
- Escrow activation: This step usually happens automatically. Upon confirming your purchase, the marketplace’s mechanism creates the escrow contract immediately. The order page is now your place to take action and manage the entire transaction process.
- The deposit: The system creates a unique one-time-use cryptocurrency address for you to send the exact amount of cryptocurrency (plus the fee for the network) to. This specific address is tied to your order. You simply send the funds from your private wallet, and the marketplace’s escrow mechanism detects the deposit and updates your order status to “Paid.” Once the seller has confirmed your deposit being secured in escrow, they will begin shipping your item.
- Delivery: The seller will then pack and send your item to the shipping address you provided. Once they have sent it, the seller will mark the order as “Shipped” and include the tracking information, if available.
- The inspection period (The most important part): You get the package. You cannot rush. You open it carefully and check that everything matches the product description. Is it the correct model? The correct quantity? Does it work? Now is your time to check everything.
- The Finalization: If you are completely satisfied, head back to the order page and click “Finalize” or “Release Funds.” This action releases the cryptocurrency from the escrow pool to the seller’s darknet hub wallet. The transaction is done, and now you can leave feedback.
- The Dispute (Your “Plan B”): If the product is incorrect, damaged, or never arrived, DO NOT finalize the deal. Instead, click “Open Dispute.” At this point, your funds are frozen in escrow, and a marketplace moderator is notified, and they will act as the judge.
- That entire dance centers around one moment: you clicking finalize. That one click is your biggest power. Do not give it up easily.
Why Use Escrow on the Dark Web?
Let’s say you decide to make a purchase (maybe software, a digital service, or even a batch of stolen data) without escrow. You spot a seller with a somewhat presentable profile. By paying directly, you expose a fundamental vulnerability: you have zero leverage.
You pay them 0.5 Bitcoin for a high-end graphics card. Now you wait. And wait. A week goes by. You send a message. No reply. Two weeks. Nothing… Your Bitcoin is gone, the seller’s account has been deleted, and you’ve now learned a hard lesson about that critical weakness.
This happens thousands of times a day. The dark web is ruthless to those who are not prepared. Using some of the best online escrow services significantly alters the power response. Here are some reasons why it’s absolutely critical:
- It resolves the “Trust” issue: You do not have to rely on the seller’s intentions. Instead, you must trust the rules of the middleman system, for a trustworthy escrow system has transparent and enforced rules. The escrow system itself serves as the trusted entity.
- It provides you with leverage if there is a dispute: A seller has zero motive to resolve any issues once you have given them your money. With a third-party holding protocol, you are holding the trump card, the payment. If the item is defective, counterfeit, or never arrives, you can stop the transaction and make your argument to a moderator.
- It eliminates the worst scammers: The laziest crooks avoid platforms with strong escrow. They target users in direct deals for quick theft. By using a protected market, you set a higher safety bar against not just fraud, but also scams designed to enable identity theft.
- It’s for secure trade, not laundering: Escrow protects a single transaction between two parties. It is not a tool for laundering money or obscuring large-scale criminal finance, which involves complex chains of transactions to hide the origin of funds.
- It gives you a step-by-step process: Confusion in the bidding operation is a scammer’s best ally. Escrow presents stability. It offers a detailed plan for the entire exchange, from your first deposit to what to do if things go wrong.
Finding an Escrow Service on the Dark Web
A common misconception is that you, the buyer, need to go out and find an online escrow service yourself. For the vast majority of dark web purchases, this isn’t how it works. The service is built directly into the marketplace.
Therefore, your primary mission isn’t to find a secure payment lock provider, but to find a platform that has a proven, trustworthy escrow system. Your choice of marketplace is your choice of escrow.
So, how do you find these reputable hubs?
- Dark web forums are your new best friend: The single most valuable resource is the dark web equivalent of Reddit, a forum called Dread. Users are discussing in real-time all sorts of markets, vendors, and scams. Look for positive reviews from lots of people over a long time regarding the market’s dispute resolution process. Is it fair? Are moderators active?
- Steer clear of new, “Too-Good-To-Be-True” markets: Flashy platforms that pop up overnight are often setting up for an exit scam. They’ll build trust with low fees and promotions, accumulating cryptocurrency in escrow. Then, they vanish, taking all the locked funds with them. This is the primary reason to stick with established markets that have a multi-year track record.
- URLs and PGP keys: Reputable markets will have established, confirmed URLs and use PGP encryption for all communication types. If you cannot find a verified public key for the market admins, that is a huge red flag.
You’re not just looking for a website with products. You’re looking for a digital city with a strong, honest police force. The model of escrows is the police force.
Setting Up an Escrow Transaction
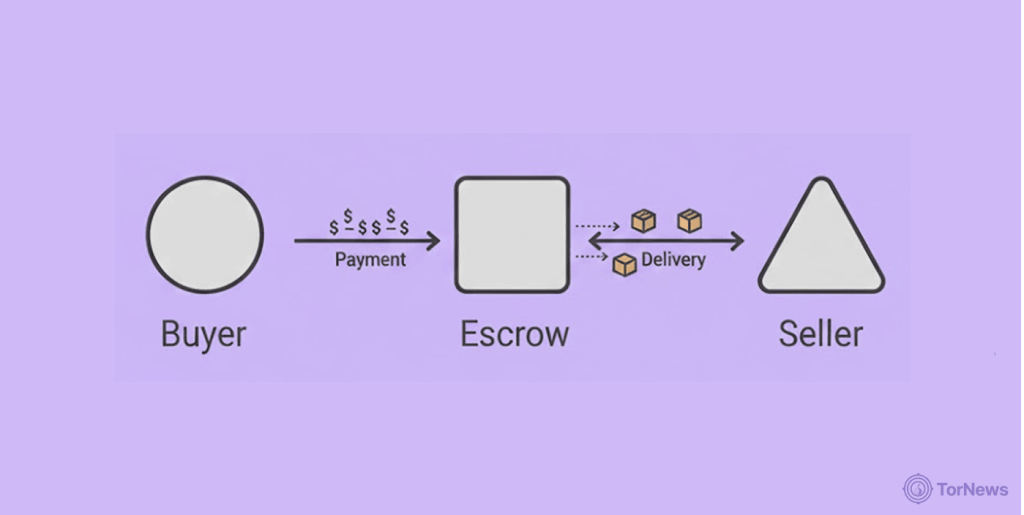
Once you’ve identified a reliable marketplace and the item you’re looking for. Here’s what to expect.
- Establishing an account: Generally speaking, you will set up a username and a really strong, unique password. You will want to activate two-factor authentication (2FA) immediately if it is available. This will provide a valuable level of security to your account.
- Funding your marketplace wallet: Some digital bazaars might require you to deposit funds into a wallet built into the market before you can purchase an item. Other storefronts will give you a direct payment address for each order you make. The direct payment option is often safer because you don’t have to hold funds on a potentially volatile dark website.
- The checkout: Once you reach the checkout, you will need to provide your “Shipping Address”. Ensure to provide a secure, non-personal, and convenient address to pick up your order. The form will make it clear that you will not use your real name. Be clear and consistent.
- The “Finalize Early” Trap (use caution here): You may see a pre-checked option labeled “FE” or “Finalize Early.” This is a huge red flag. Shady sellers use this to trick buyers into waiving all protection. If you see this, UNCHECK THE BOX immediately. Finalizing early sends your money directly to the seller with no way to get it back. Cancel the order if the seller insists on it.
- Confirm: Review and verify the total amount purchased, the shipping address, and the payment address. Copy and paste again from your wallet, making sure that the first and last four characters are right, so there are no mistakes.
This setup is very easy. The hard part is being vigilant.
Comparing Legitimate vs. Fraudulent Dark Web Transactions
Be sure to keep all exchanges regarding your order, including between you and escrow moderators or sellers, within the marketplace’s encrypted chat system. Avoid using other platforms such as WhatsApp, Telegram, or email. Never.
These other platforms remove the protections and record-keeping that the vendor forum provides. An escrow moderator will not be able to review email correspondence as potential evidence in a dispute.
Additionally, be professional and concise in all of your chats with a seller; for example: “Good morning! Can you confirm the estimated shipping time?” If a dispute arises with the holding service moderator, this tone is very important. Stay factual, not emotional.
Here’s an Example of a Bad Dispute Message:
“This seller is a scammer! He ripped me off! I want my money back NOW!!!’
Here’s an Example of a Good Dispute Message:
“Hello, Moderator. I am writing regarding my order #12345. The seller advertised the item as a new, sealed iPhone 13. I received a used Android phone that is a different model, which I can provide pictures of. Additionally, the tracking number provided is invalid, and I have not completed the order, and I would like a complete refund.”
In the second message, the moderator has everything they need – a calm description of the problem, the order number, the specific difference, and proof. This is a business negotiation, not a dispute on the street.
Verifying Seller and Buyer Authenticity
Before clicking “buy,” you need to vet the dark web vendors on the other side of the screen. The difference between becoming a victim and a successful user often comes down to this due diligence. Here’s how to use escrow service on dark web iOS, Android, and across other platforms.
Here’s how to vet a seller:
- Feedback score and history: Don’t just look at the number. Click down and read the comments. Are the reviews specific about the product or shipping? Be wary of dozens of generic “Great seller A+!!!” posts made on the same day. Natural feedback history has peaks and valleys.
- Account age: An account that has been active for two years will generally be a much safer bet than a two-week account. Longevity is a good indicator, although, as with anything in life, it still doesn’t guarantee the vendor is reliable.
- PGP key: A known, market-signed PGP key is one sign of a professional vendor. Vendors who sign their posts demonstrate a basic understanding of operational security and show that they are established.
- Check their other listings: Do they offer the same product or services, or a random assortment of high (and unverified) value electronics, digital goods, and services? Specialization is generally always more knowledgeable or reliable than an average liquidator.
As a Buyer, Your Reputation is Important:
Yes, as a new buyer, high-quality retailers may limit what you can purchase. This limit is based on the vendor’s concern for their safety in dealing with law enforcement and/or untrustworthy customers.
Start small, pay your bill, communicate professionally, and build your reputation. As your reputation as a good buyer grows, you may get better service and/or be part of new listings before the general public.
Depositing Funds Into Escrow

At this point, the holding service takes control of your funds—specifically, your cryptocurrencies—and secures them digitally. This technical side is where things can get trickier.
- The Presented Address: After locking in your order, the marketplace will display a deposit address for Bitcoin or Monero (or another accepted cryptocurrency). This long alphanumeric string is unique to your order.
- The Copy and Paste Risk: It’s best practice to simply copy and paste the address over to your wallet. However, it’s possible, though rare, that a sophisticated malware called a clipper is lying in wait on your machine and replaces the copied cryptocurrency address with one in possession of the hacker. This is the case, where you’re pasting it into your wallet, that it’s best practice to always visually verify the first four and last four characters. If one is different, abort immediately.
- Network Charges: Keep in mind that exchanges in cryptocurrency incur a fee. Your wallet will display the network transaction fee. Verify that you are sending the exact amount that the escrow system requires, and ensure you also have a small amount extra in your wallet to cover this fee. If someone is below the required amount, you run the risk of exchange failure or long delays.
- Confirmation: When you’ve finished broadcasting the deal on the dark web, the network confirms it. Depending on congestion on the network, confirmation could take a few minutes or up to an hour. Following the confirmation, your order status is changed to “Paid.”
Wrapping Up the Trade

When you’ve successfully received your package, ensure you follow the steps below to finalize your transaction.
- The unboxing: When opening the product, proceed slowly and with caution. If you feel suspicious, record the unboxing by taking a photo or video of the package’s condition before opening it and of the item as you unwrap it. This is good evidence if you end up having to dispute the item later.
- The Inspection: Check to see if the item is correct. Is it the correct brand and model as advertised? Does it turn on? Is the quantity you ordered what you received? Compare it very carefully to the product listing.
- The Decision:
- If Everything is in Order, log into the marketplace, locate your order, and click the finalize button so that funds are released to the vendor. It is considered polite to leave honest, constructive feedback for the seller once you finalize. This helps out the entire community.
- If there is ANY Problem: Don’t finalize. Just reach out to the seller through the market’s messaging system. Allow them an opportunity to make good. They might’ve sent you the wrong item and will ask about sending the right one. If not, then you can go into a formal dispute if they are not responsive/helpful.
Don’t ever finalize early. No matter what the seller is telling you. No matter how much they are pressuring you. Your only assurance is the finalize button.
Dispute Resolution with Escrow
The seller has sent you a box of rocks instead of a laptop, and hasn’t messaged you back. This is where the escrow framework shines.
- Open a dispute: On your order page, before the auto-finalize timer runs out, there is an “Open Dispute” or “Raise Dispute” button that you can push. This will immediately lock the funds in a trusted intermediary and notify a moderator of the marketplace.
- State your case: You will be taken to a dispute thread where you can communicate with the seller and the moderator. This is your time to use your best calm, factual communication skills. Write a calm, factual summary of the situation. “Ordered Item A, received Item B. See attached photos. The seller is ignoring my messages.”
- Submitting evidence: Post all evidence you have gathered. This will include:
- Screenshots of the product listing.
- Screenshots of communication with the seller.
- Photos of what you actually received, including pictures of the packaging and the wrong/wrong item.
- Any other relevant information.
- The moderator will review the evidence from both sides. The seller will also be allowed to respond. The moderator will intend to try to determine what a fair outcome is based on the evidence submitted.
- The Ruling: The moderator has a few options.
- Refund the buyer: If you obviously didn’t get what you were supposed to get, the moderator will release the funds from escrow back to your marketplace wallet.
- Release to the seller: If the seller can provide sufficient evidence that they shipped the correct item (for example, a valid tracking number that shows delivery to your city and the weight of the product), it may be ruled in the seller’s favor.
- Split the difference: In unclear cases, a moderator may propose a partial refund. Remember, any fees charged by the escrow service are usually non-refundable and will be deducted from the settled amount.
The internal dispute process is far from perfect, but it’s infinitely better than having no recourse at all. Remember, this is a self-regulated system; involving actual law enforcement agencies is not an option here without incriminating yourself. The escrow moderator is the only judge you get.
Precautions When Utilizing Escrow on the Dark Web
The core goal of using escrow is to protect yourself from scams. But to do that effectively, you must layer it with strong personal security. Any dark web activities, including using an escrow service, come with inherent risk. You are operating in a high-stakes environment where safety is not guaranteed. Therefore, your operational security (opsec) should always be attentive.
- Always choose a reputable VPN. A Virtual Private Network conceals your IP address so that it is harder for someone to link what you are doing back to your address. This is non-negotiable; in fact, you should first turn on your VPN, such as NordVPN, before even opening the Tor browser.
- Your Tor browser is Your Entry Point. Never go into dark web markets on a regular browser. Use the latest and stable release of Tor Browser, which is optimized for bringing anonymity to your traffic.
- Antivirus and anti-malware are non-negotiable. The dark web is a breeding ground for digital threats—malicious scripts, phishing traps, and keyloggers. A solid, real-time security application is your essential shield against these attacks.
- Never use the same password twice. A password manager is now universally available on all smartphones, to make it easy to generate and store undoubtedly long, unique, and complex passwords for every site you utilize, especially marketplaces on the dark web.
- Encrypt everything you own: Ensure to acquaint yourself with the fundamentals of PGP (Pretty Good Privacy). It’s good practice to apply PGP to encrypt any communications concerning sensitive details you receive from the dark web, which includes your shipping address. Many reputable vendors require this.
- Trust your gut. Always. This is the #1 rule. If anything feels ‘off’, if the deal is too good, if the seller is being too pushy, if the pages look ‘wrong’, close the tab and walk away. Recklessness doesn’t get a person a reward on the dark web.
For organizations, understanding these escrow mechanics is a part of effective dark web monitoring. Knowing how transactions are secured helps analysts distinguish between credible threats and background noise when tracking stolen data or compromised credentials.
Conclusion
Mastering escrow on the dark web is more than following steps; it’s adopting a mindset of defensive engagement. Whether you’re a researcher or a digital privacy advocate, understanding these systems is about navigating risk, not inviting it. It is understood that within an environment devoid of traditional rules, you must develop a set of rules to provide a guarded experience. This set of rules is escrow.
This guide equips you with advanced knowledge, from finding a market and completing a deal to navigating a dispute. You have the ability to assess the signs of a legitimate transaction and the screaming red flags of a scam. You understand that your agency lies within that last “Finalize” button and a dependency on layers of protection: a VPN, Tor, anti-virus, and the still more important disposition of your own sharp instincts.
The dark web does not need to be a digital death wish. By allowing escrow to illuminate your path and your vigilance to guide you, you can navigate this space with informed caution. Remember, this knowledge is for understanding the mechanics of trust in a hidden economy, not for facilitating illegal activities. You now know the boundaries; proceed with extreme care.
FAQs
If you want to use such services on the dark web, you can expect to pay about 3% to 15% of the deal amount. The charge is typically based on the exchange amount, complexity of the transaction, and risk involved. You are required to pay the fee regardless of whether the transaction is completed.
Yes, you can use your iOS smartphone to manage escrow payment handoffs. However, Apple demands that all mobile browsers make use of the restrictive WebKit engine, which is a serious security challenge. This restricts mobile Tor apps from executing the full privacy components of the desktop browser, which can also risk revealing your device’s IP address during important escrow steps.
A verified marketplace builds genuine escrow functionality directly into its platform and uses a multisig crypto wallet. Imposter websites are standalone, illegitimate websites posing as a real service. They often use confusingly similar names and ask for payments through untraceable methods like wire transfers, something a genuine third-party holding system would never do.
You can begin the dispute resolution procedures if the seller fails to send your purchased item to you. An arbiter withholds payment while reviewing evidence from you and the seller. Once the arbiter has reviewed all evidence, they’ll render a decision and notify both parties. If the arbiter determines the buyer’s evidence was sufficient to prove their claim, it can mean the buyer would receive the money back.