To be honest, the digital world is a dangerous place. You’re just minding your own business, browsing the internet, checking emails, or downloading a file, and before you know it, something sketchy has wormed its way into your computer. That “something” is malware.
Malware is not a type of threat. It’s a general term for any program or software that is malicious and intended to harm your work or gain unauthorized access to your computer or network.
You can think of it like a computer virus, and there are as many different types of malware as there are diseases in the world; some causing a few minor problems and others causing huge damage. The harsh reality is that it can all come from one little click.
This guide provides you with a better understanding of what malware is, how it works, and ways to prevent and even get rid of it. In addition, we have also covered. Let’s roll!
What is Malware?

In the realm of computing, malware, short for “malicious software,” is a somewhat catch-all term. Whenever a program or application slips onto your computing device and does something you did not consent to, it is classified as malware.
Depending on the purpose of the program, it could be any number of things, including spying on your activity, extorting you for your files, etc. Hackers and other bad actors create malware to cause harm—by stealing your data, destroying your system, or taking over your machine for their own gain.
Furthermore, when it comes to malware vs. virus, many users refer to malware and viruses as the same thing. However, it is actually important to understand the distinction. A virus is just one type of malware. To use a somewhat imperfect analogy, all spiders are arachnids, but not every arachnid is a spider.
This distinction is important since viruses must attach to or “piggyback” on a host file to survive, and they can also replicate themselves by attempting to infect other files and parts on your computer. Other forms of malware are even more insidious and do not rely on attaching to or piggybacking on anything at all.
What is the Purpose of Malware?
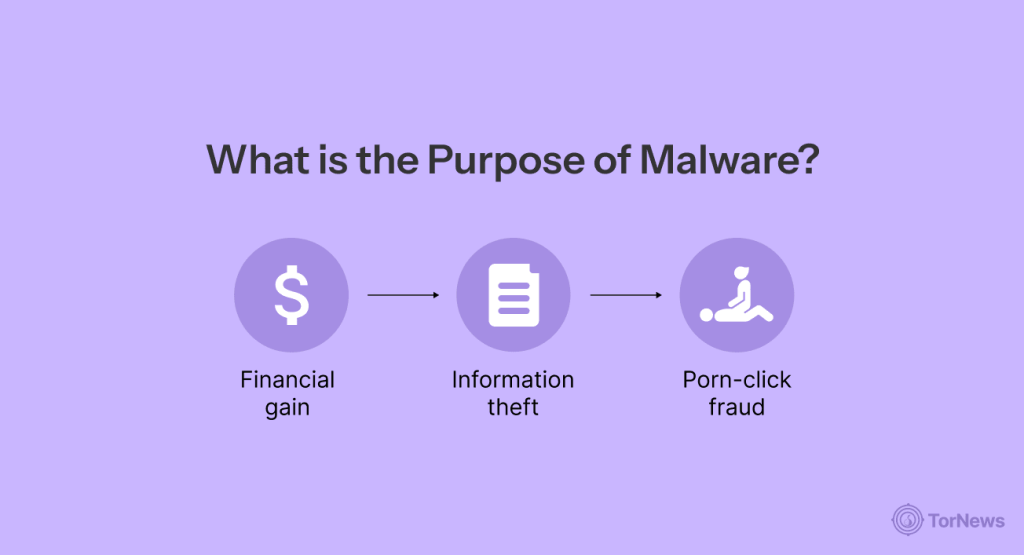
Malware is not designed without a purpose; it’s often designed for malicious reasons. And the reason is mainly assigned to why the malware exists, but the “why” is as important as the “what.”
- Financial gain: This is the biggest reason. Most cybercriminals commit cybercrime to make money. Ransomware can lock your computer and demand a ransom. Spyware can steal credit-card information, and banking Trojans can hijack your financial accounts.
- Espionage: Not every hacker is seeking cash; some attackers are looking to spy on personal information. Nations and corporations use malware to spy on other companies or countries to extract sensitive information, trade secrets, or political information.
- Disruption: In some cases, the goal is just to mess up things. Some malware attacks exist simply to crash a network. Others might just shut down the whole system (even if critical), and some to delete really important files.
- Information theft: Personal information is a valuable commodity. Malware can be used to steal your identity and sell personal information on the dark web, or use the information to develop future well-targeted attacks.
- Porn-click fraud: This is a surprisingly common goal. Hackers use malware to force your computer to click on pornographic ads, generating revenue for them at your expense. It’s a gross and invasive use of your machine.
8 Common Types of Malware
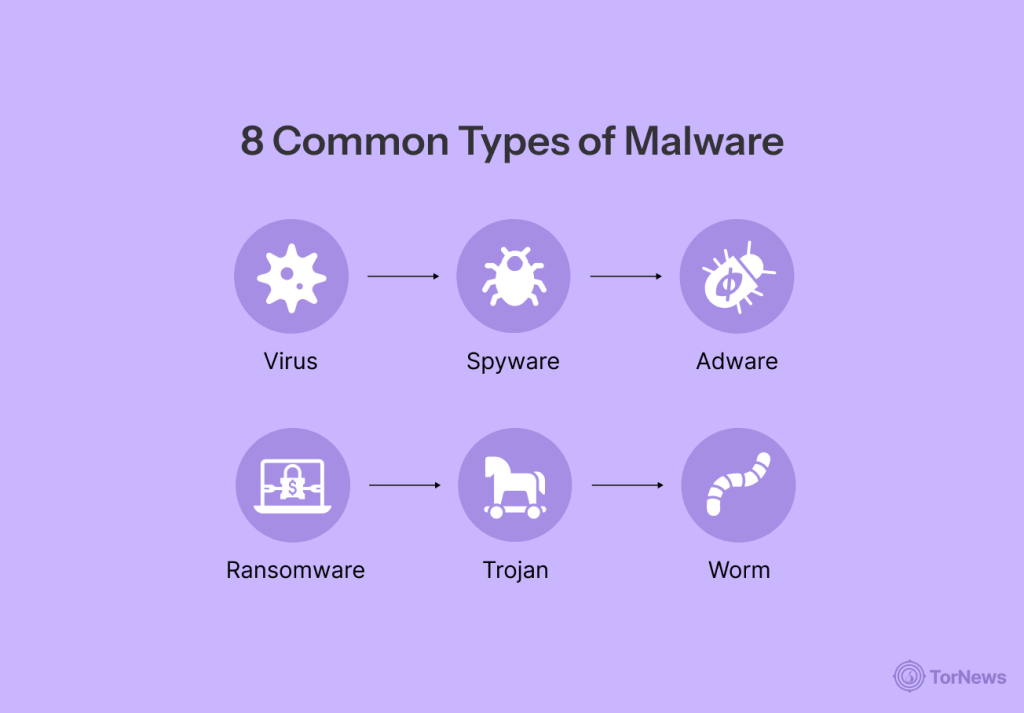
Malware may be likened to a villain wearing many masks, as it can take many shapes. Some malware is loud and destructive, while others act like silent ninjas that we would not pick up on without the help of a decent antivirus.
Let’s get into some of the most common types of malware examples.
1. Virus
This is the classic. A virus is a piece of code that attaches itself to a legitimate program. After you open that legitimate program, the virus will then execute, corrupt your files, and spread to other applications.
2. Spyware
Spyware, as the name implies, spies on you secretly running in the background. It tracks your online activities and can steal sensitive information like passwords, login details, and credit card numbers—often without you realizing it.
3. Adware
Adware is more than an annoyance. It is dangerous. It will flood your computer with unwanted pop-ups and ads, slowing your computer down. In some cases, the adware may even redirect you to malicious websites.
4. Ransomware
Ransomware is the stuff of nightmares. The type of malware holds your system hostage by encrypting your files and data and then demanding payment (ransom) to decrypt them.
If you don’t have data backup, you’re in great trouble. Sometimes, the hackers don’t decrypt the data even after you pay the ransom. That’s why it’s a nasty and frequently destructive form of malware attack.
5. Trojan
This one is a sneaky imposter. A Trojan acts like a legitimate program or useful utility (such as a free game or a software update) to trick you into downloading it. It can open a backdoor for other malware or hackers to exploit your device once installed on your computer.
6. Worm
A worm is an independent software that can self-replicate without a host file, thus allowing it to spread across a network. They are especially good at infecting multiple devices, which makes them incredibly problematic in business firewalls. They multiply continuously.
7. Botnets
A botnet is a network of hijacked computers (or “bots”), all controlled by a single attacker for malicious purposes like sending spam or launching a large-scale attack on a website. Your computer could be a zombie in an army of them, and you’d never know.
8. Rootkit
This is one of the most terrifying ones. A rootkit is a set of tools that enables a hacker to have admin-level access to your computer and remain 100% invisible. A rootkit hides itself to a point where it is nearly impossible for normal antivirus applications to detect and remove it.
How Do I Get Malware?
It is relatively easy to get infected by malware. You may do something truly foolish, but most of the time, it is simply a matter of a lapse in judgment or just pure chance.
Regardless, this is how infections normally get to your computer:
- Email attachments: This is an old method that still works. You receive an email, seemingly harmless and legitimate from some organization, a bank, a delivery service, or social media site. Once you open the attachment, your device gets a Trojan or a virus.
- Sketchy downloads: Downloading software, music, or movies from unverified sources (such as torrent sites) may also lead to downloading malware. The downloaded file may contain spyware, viruses, or some manner of malware. So, always download files from verified sources.
- Malicious ads (malvertising): You’re doing some web browsing, and a seemingly innocuous ad opens up. You don’t even have to click on it, merely looking at it sometimes will trigger a drive-by install that infects your machine.
- Infected removable devices: Plugging a USB stick into your computer could transfer a virus within a few seconds. Using a removable device in a computer is an extremely common method of spreading malware in an office or school environment.
- Social engineering: This is when a hacker tricks you into giving them access. They might pretend to be a customer support agent or perhaps a friend in need, and get you to click a link or give out your password.
How to Prevent Malware

Avoiding miserable malware is definitely easier than dealing with it. You will not be able to rid yourself of all risk factors, but you can actively minimize the risks. Here’s how to avoid malware and protect your devices.
1. Use Antivirus & Antimalware Software
This is serious. Antivirus is non-negotiable. Ensure that you have a reputable antivirus product, such as Malwarebytes or Windows Defender, installed on your device. Also, make certain that you keep it up to date. It is your first line of defense against all sorts of potential threats to your devices.
2. Keep Your Software Updated
When a software manufacturer releases an update, it is not just for the manufacturer to add features. Software updates generally have important security fixes that correct vulnerabilities that hackers use to attack a system. Be sure to update your operating system, web browser, and applications regularly, whether their updates are detected manually or automatically.
3. Think Before You Click
This is a big one. Be suspicious of attachments, links, and pop-ups. If an email looks a little sketchy, just delete it. If a site is telling you that you need to download some type of file to continue on to the site, just close the tab.
4. Use a VPN
A VPN (Virtual Private Network) is a service that offers an encrypted connection from your device to the internet. It is an added bonus perk, especially when using free Wi-Fi, because it offers anonymity for your online activity. Therefore, when performing actions where sensitive information needs to be communicated, it provides a level of protection that is extremely difficult to bypass by hackers if the VPN is designed well.
5. Use a Firewall
Your computer’s firewall is the hedge between your machine and the internet, monitoring incoming and outgoing traffic. Ensure that it is enabled to block unauthorized access to your machine.
6. Back Up Your Data
This is a no-brainer. Ideally, if you’ve been hit with ransomware, having recently backed up important files means that you don’t have to pay the ransom; instead, you can wipe your computer and restore everything from your backup.
How to Know If Your Device has Malware
At times, malware announces its takeover with a bang. However, it can be a silent invader. Therefore, knowing what signs to look for is the best way to protect yourself.
Malicious code does not discriminate and can infect any device. So, you should know the signs of compromise, which can look different depending on the device you are using.
Below is a list of indicators of a malware infection for each of your primary devices:
On Your Computer System (PC or Mac)
Your computer system is likely the most common device you use and will typically generate plenty of alerts and signs. The key is recognizing when you notice some weird things.
- It’s unbelievably slow: Your PC or Mac suddenly crawls, freezes up, or takes forever to load any relatively simple program. Malware can take up your computer’s available memory and processor time, leaving nothing left for you.
- A tidal wave of pop-ups and ads: You have a barrage of pop-ups constantly, even while not browsing the web. This is a classic sign of adware since it is built with the intent of throwing as many ads in your face as possible.
- Your browser looks weird: Are you seeing a new and unrecognizable toolbar? Has your homepage changed to a search engine that you have never seen before? These indicate that you may have installed a browser hijacker.
- Programs start acting up: Applications that you use every day suddenly crash for reasons beyond your understanding. In a far more serious attack, your antivirus software might become mysteriously disabled and refuse to turn back on. When this happens, it should be a huge red flag that a hacker wants to remove your protections.
- Your files are gone or won’t open: This is a horror story we have all considered, but it can happen. If you are missing important files or cannot access them, you could be dealing with either a strong virus or ransomware that has encrypted your files.
On Your Android Device
Android is a popular target due to the sheer volume of users. Here are some problems to see on your phone or tablet.
- The battery drains faster than usual: You’re hardly using your phone, and yet your battery is dead in a few hours. Malware usually runs 24/7, and its sustenance is battery power. So, typically, you can’t see that it is there, draining your battery.
- Your data usage skyrockets: There has never been a problem before, but suddenly, you get warnings that your data cap is about to be hit when you weren’t watching videos all day. That means malware sends information to a hacker’s server that is unknown to you and uses up your phone’s valuable data.
- Strange app icons on the home screen: If you see an icon of a mobile application that you never downloaded, it is a strong indication that a bad program has hijacked your phone to install itself.
- Unusual overheating issues: If the device feels unusually warm overall and you were not using any heavy applications on it, it could suggest that some program is invisibly utilizing your phone’s processor.
On Your iPhone or iPad
iPhones and iPads tend to be more secure than other devices. However, that doesn’t mean they’re completely immune — you still need to be aware of the malware signs, especially if you’ve jailbroken your device (which circumvents Apple’s safety).
- Unexpected crashes or freezes: If your apps and devices tend to crash and freeze regularly, there might be a serious problem.
- Rapid battery depletion and overheating: Similar to Android, rapid battery drain and overheating could mean you have a malicious process running in the background.
- Data usage you can’t explain: Any unexpected uptick in your data use should raise a red flag.
- The appearance of strange pop-ups in your browser: Getting lots of pop-up ads in Safari could be a sign that you’ve clicked a malicious link.
How to Get Rid of Malware

You’ve faced the nightmare and suspect you have malware. Don’t panic. Follow these tips to minimize the damage:
- Disconnect from the internet: Once you suspect an infection, you should disconnect from the internet. Unplug the system from the network or disable your Wi-Fi. This step prevents the malware from contacting its “master” and stops it from growing or spreading.
- Enter safe mode: Restart your system into Safe Mode. This will only load the essential programs and drivers and will likely prevent most malware from executing and allow you a “cleaner” workspace (i.e., none of your installed programs will run).
- Run a full scan: Scan your system with a trusted antivirus or antimalware service to identify the malware. This utility will report on the malware, put it into “quarantine”, and help you to remove it.
- Delete temporary files: Malware usually creates some temporary files. It is safer to delete them after scanning to avoid possibly getting infected again.
- Restore to a previous point: If you can’t get rid of the malware, consider restoring to a period before the infection. This might not save your last files, but it will save you from malware.
A Brief History of Malware
Have you ever wondered what malware is in cybersecurity? Malware is not a concept that began with the Internet. This has a much older origin, and the history of malware in cybersecurity is fun to explore!
- 1970s: The Creeper: The Creeper was the first virus ever built. It was actually a worm that was harmless in nature, but rather an experiment. The nature of this malware was to display the message “I’m the Creeper, catch me if you can!” on the screen of a computer.
- 1980s: The Brain Virus: The Brain virus was the first real, true computer virus that affected IBM PCs. This virus was written by two brothers from Pakistan to punish people for pirating their software. The virus was not malicious. However, it did identify a problem of significant vulnerability.
- 1990s: The Rise of Mass-Mailers: As the internet became more integrated into daily life, malware became more widespread as well. At this point, viruses like Melissa and I Love You spread rapidly by email, crashing servers and costing millions of dollars.
- 2000s: Botnets and Spyware: Rather than the common intent of causing damage, malware use began to shift toward generating monetary gains. Malware was aimed more at stealthy data service use than at disallowing access to it. This is also when botnets took on popularity as a large-scale attacking tool.
- 2010s to today: Ransomware Reigns: The last decade has certainly been under the rule of ransomware. For hackers, this has been a lucrative business model as we have seen ransomware take down hospitals, schools, and corporations in headline news.
FAQs
Viruses and worms are types of malware. Think of a virus as a computer parasite that cannot survive independently and must first attach itself to a bona fide file or program. When you launch that program, the virus wakes up and damages your files or computer. A worm is a self-sustaining malware that does not attach to a host file to live. It can access your computer, replicate itself, and then make copies of itself across a network. This is dangerous to home or corporate networks, since if one computer is infected, potentially, all such systems can have worms in them as well.
No, Macs are not actually safe from malware. They have indeed been traditionally considered more secure than PCs, but this was largely because PC users were a much more enticing target for hackers. However, Mac malware is out there, and it’s increasing. Over the past few years, we’ve seen increasing examples of Mac-specific spyware and ransomware. So, Mac is not a bulletproof vest; you should still use antivirus software to stay safe.
Absolutely. Malware infections are a growing and serious problem with smartphones and tablets. It usually comes disguised as a malicious app, either by appearing as a harmless app that collects your information or by hijacking some sort of resource on your phone. These shady apps can sometimes get pushed through an app store that’s not official. But it’s very important to always download apps using the actual Google Play Store or Apple App Store. Other avenues for your phone getting infected are by clicking on phishing links from text messages or emails, or going to compromised websites. It exists, and your phone needs to be protected just like your computer.
No, but it is an easy mistake to make. Here’s one way to think of this: all spyware is an example of malware, but not all malware is spyware. Malware is the overarching term for any malicious software. Spyware, however, is a little more specific in its goals. It is a particularly devious and dishonest type of software designed to spy on you and steal your data. It is intended to stealthily collect your login details, passwords, and browsing behavior without you realizing it.