Cyberattacks have become a reality for businesses of every size, especially in the world we all currently live in. But to mitigate such threats, businesses must go beyond just preventing them from occurring, and also rapidly detecting the threat and responding to it.
To help businesses act quickly to the latter, Indicators of Compromise (IoCs) can become invaluable to organizations. IoCs are best considered as traces left by cyber attackers that allow you to know that you have been hacked. They act as an early warning system, which enables security teams to detect the presence of a cyber-threat and take informed decisions.
In this article, we will explore what IoCs are, how they work, what types of IoCs exist, and most importantly, how you can take advantage of them to design an even better cybersecurity roadmap for your organization.
What are Indicators of Compromise (IoCs)?
IoCs are pieces of data indicating that a computer network or system has experienced a security compromise. Cybersecurity experts, such as forensic science teams, use IoCs to investigate and confirm the presence of an attack.
In its Special Publication 800-150, the National Institute of Standards and Technology (NIST) defined IoCs as technical artifacts or observable variables indicating that an attack is anticipated, occurring, or has occurred. This goes a long way to show how IoCs are important in early threat recognition and impact mitigation.
Hence, timely recognition of these indicators could be the difference between a minor incident and a significant or devastating data breach. By recognizing the IoCs observed, an organization has the capacity to take immediate action, contain the threat, and put up a prevention mechanism.
Dwell time — the period an attacker remains undetected in a system, often lasting weeks to months — shrinks when teams use smart IoCs, which hinder attackers and shorten their time on target.
For cybersecurity professionals, IoCs don’t only function as a final solution to a cybersecurity issue, but they are valuable information after an incident. Also, during forensic investigations, IoCs provide the essential evidence needed to determine the source/entry points of a breach, the type of attack, as well as the goal(s) of the attacker.
By understanding the ‘what’ and ‘how,’ organizations can improve their existing security controls, policies, and holistic approach to their overall cybersecurity resilience. Also, IoCs not only provide posterior investigation insights, but they are the foundation of a joint defense and community approach to threat intelligence.
How Do Indicators of Compromise Work?
Indicators of Compromise (IoCs) are the equivalent of digital “flags” for cybersecurity practitioners. They allow us to detect abnormal activity that denotes a compromised system.
By looking for the digital traces of a cybersecurity attack, IoCs are often contained in log files. Usually, these log files are obtained from many, if not all, of the systems and devices that an organization runs as part of its IT infrastructure.
The discovery of these important IoCs is done using various methods, including:
- Observation: Continuously looking for abnormal activity or behavior across systems and devices.
- Analysis: Delving further into suspicious activity to determine its characteristics, severity, potential impacts, etc.
- Signature matching: Recognizing known malware IoC list signatures from databases of these signatures.
However, the emergence of new sophisticated cyber threats daily makes manual detection of potential indicators of compromise (IoCs) unrealistic, if not impossible. When it comes to detecting today’s threats for all organizations, we will have to rely increasingly more on a predominantly automated process driven by AI/ML rather than human analysts.
In other words, where an organization has to review a hundred thousand lines of log file data to identify patterns of IoCs, this is not sustainable. This will yield multiple thousands of alerts, or for many organizations, low-to-no-priority alerts that could also lead to analyst “alert fatigue”. That is, making alerts meaningful only to miss some critical alerts.
The main cause of this is that the sheer volume of alerts becomes overwhelming to manage. Another possible cause would be giving up engagement altogether because the patterns they reviewed were not meaningful. Prominent solutions for the issues described above include modern Security Information and Event Management (SIEM) and Extended Detection and Response (XDR). These solutions employ the use of AI and machine learning.
With an AI-powered solution, there will be a baseline for acceptable activity and the generation of real-time alerts as activity deviates from the baseline. AI is capable of ingesting and analyzing millions of security events at once, and identifying anomalies also quickly.
But more importantly, AI can identify IoCs that static detection systems reliant on rules and signatures would miss. AI-powered solutions allow for a higher level of computing efficiency to drastically reduce the time and effort organizations invest in security incidents.
They do this by removing unknown and false indicators and prioritizing the blue team’s response to higher confidence alerts and raw IoC data piles for additional investigation. Indicators of Compromise (IoCs) for an active breach or live attack will be handled faster, removing the threat and cleaning up the system, thereby limiting the extent of any damage.
Different Types of Indicators of Compromise
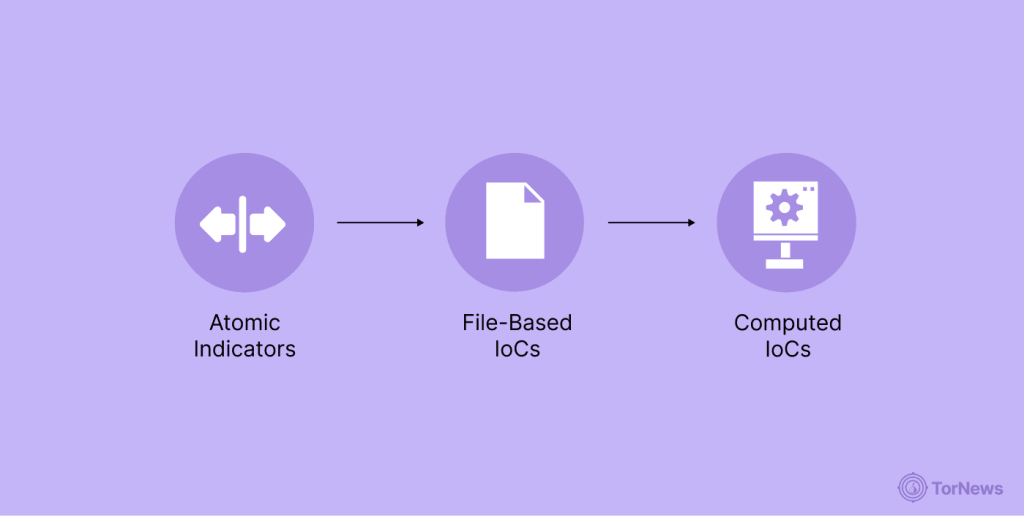
In the world of cybersecurity, Indicators of Compromise (IoCs) can manifest in a variety of ways across an organization’s digital environment.
To ensure that the organization detects and responds to threats effectively, security practitioners will classify indicators based on a “Pyramid of Pain“. Indicators that are higher on the pyramid are generally more valuable for a defender.
Atomic Indicators
The first layer of this pyramid is that of atomic indicators, which are single data points that represent specific evidence of adversary activity.
Atomic indicators are the easiest to detect, but also the easiest for an adversary to manipulate. The reason is that they are easy to detect, and also represent a defender’s initial line of sight into a potential compromise.
File-Based IoCs
- File Hashes: A file hash (e.g., MD5, SHA-1, SHA-256) is a uniquely identifying string for a file created through a cryptographic process. A known malicious hash and a hash of a file that match it indicates the evidence of malware.
- File Names and Paths: Attackers will use unique file names or odd file locations to run their malicious code. Whether it be a file’s name or its location that is odd (eg, in a temp folder or a misspelled name directory (eg, svch0st.exe)), any file that links to malware would be suspicious.
Network-Based IoCs
- Malicious IP Addresses and Domains: Any connection to an IP address or domain that links with command-and-control (C2) servers or malware distribution is an atomic IoC.
- Email-Based IoCs: Emails can hold IoCs and are representative of the initial access attempt. Email IoCs can include a suspicious sender email, a malicious link or attachment, and/or a phishing domain in the contents of the email. It’s also worth noting that these same malicious links and phishing domains are increasingly shared through social media platforms. That makes social monitoring a key part of early detection. For a deeper look at this, explore our guide on social media monitoring.
Computed IoCs
Continuing up the pyramid, defined IoCs are harder for an adversary to adjust. They are observations that the security experts derive from processing data through logic. A SIEM system frequently computes defined IoCs when correlating multiple data points into a defined context or “picture” of the threat.
- Registry IoCs: Attackers often modify Windows Registry keys to maintain persistence on a given system and ensure their malicious program runs on a restart of the computer.
- Anomalous Network Activity: An anomalous network event is classified as a computed IoC. An example of the various events could include: an unusually high amount of outbound network traffic, an application that is suspicious and is using an unobserved port, or a high volume of DNS requests that closely resemble C2 traffic patterns.
Behavioral IoCs
At the top of the “Pyramid of Indicators” are behavioral indicators of compromise (IoCs). These are the ones that most represent the attacker’s Tactics, Techniques, and Procedures (TTPs), and are the aspects of behavior that, aside from identity theft, are the hardest for attackers to alter.
While atomic IoCs and computed IoCs tell you what the attacker used, behavioral IoCs tell you how and why they are acting.
- Lateral movement: After successful initial access, the attacker begins to move deeper into the network. Behavioral IoCs could include an account attempting, for the first time, to access resources on a different machine or an account performing reconnaissance utilizing internal tools like PowerShell.
- Privilege Escalation: A user or process tries to attain access to privileges greater than what they normally have access to inside the organization. The eyes of the user account may have “Low Level” permissions, yet it is attempting to access a sensitive administrative file or accessing a sensitive administrative database.
- Suspicious user behavior: The activity patterns are different from established user behaviors. This might include accounts registering failed logins over and over, logging in from a strange or unusual geographic location, and an account suddenly accessing files and sensitive systems that it had never previously interacted with.
All these types of IoCs do not stand alone; they form a chain of evidence. A single cyberattack is usually multi-phased, and a single phase leaves its own digital footprint.
First, consider a phishing email (email IoC) that causes a malicious file to be downloaded (file IoC), which then modifies Windows registry keys to achieve persistence (computed IoC).
After that, it will establish a connection to a C2 server (network IoC), and then the final phase of the attack could be the attacker trying to perform privilege escalation or lateral movement on the infected host. At that stage, the forensic analysts are left with only behavioral IoCs.
This is why current security products like SIEM and XDR that allow a security analyst to correlate data across the various constraints of IoCs are so important.
By putting together all the pieces, security teams can tell the whole story of the attack and make accurate and informed responses to remediate the incident.
IoCs vs. Indicators of Attack (IoAs)

While both IoCs and Indicators of Attack (IoAs) are vital for detecting cyber threats, they represent distinct phases and focuses of malicious activity.
Understanding the Core Differences
Indicators of Compromise (IoCs) and Indicators of Attack (IoAs) serve distinct yet complementary roles in cybersecurity:
IoCs (Indicators of Compromise)
- Timing: IoCs are identified after an attack has completed; they are forensic proof of a previous breach.
- Focus: IoCs evidence compromise, these are static artifacts or data points that the adversary left behind.
- Nature: Reactive.
- Use case: Forensic investigations, guidance to incident response, and banning known malefactors in the post-breach phase.
- Examples: Malicious IP addresses, specific hashes of malware files, suspicious domains.
- Context: Generally, less contextual and relies on exact matching to some known data point.
IoAs (Indicators of Attack)
- Timing: IoAs focus on identifying adversary behaviors in real-time or evidence of imminent or active attack.
- Focus: IoAs aims to uncover the adversary’s behaviors and intentions, specifically their techniques, tactics, and procedures (TTPs).
- Nature: Proactive.
- Use case: Detection and disruption of cyber-attacks before real damage occurs.
- Examples: A phishing campaign (before clicking), failed logins from abnormal locations (multiple attempts), or a system trying to escalate privilege.
- Context: Highly contextual; considerations for the ordered sequence of behaviors.
IoAs and IoCs can be useful adjuncts to a mature security posture, providing information of different strengths and weaknesses around threats and vulnerabilities.
IoCs, IoAs, and MITRE ATT&CK
The MITRE ATT&CK® framework is a curated database of adversary Tactics and Techniques, which is publicly available based on real-world observations.
The ATT&CK framework outlines adversary behaviors throughout their lifecycle, commonly known in cybersecurity as Tactics, Techniques, and Procedures (TTPs):
- Tactics: The adversary’s technical objectives (“what” and “why”), e.g., credential access.
- Techniques: Describes “how” an adversary achieves a tactical goal, and is often through using existing acceptable system functions (aka: living off the land).
- Sub-techniques: More granular descriptions of techniques.
- Procedures: The specific instance of how a technique is recorded in an observation.
In ATT&CK, we see a transition away from only searching for static IoCs (indicators of compromise) to more actively looking for signs of adversary behavior.
IoCs (e.g., hash of a malware file, malicious URLs) are just artifacts of past compromise, and only provide a limited understanding on their own. A list of IoCs or ATT&CK tactics/techniques without the relevant contextual technical details has less actionable value.
On the other hand, IoAs (indicators of attack) are much more closely aligned with ATT&CK’s TTPs (tactics, techniques, procedures). This is because they aim to gain an understanding of what the attackers did and wanted to do during an active attack based on the attacker’s changed behavior.
An IoC (e.g., malicious file hash), mapped to an ATT&CK technique (e.g., “PowerShell Execution”), provides significant context around what an adversary intended to do. That is how the bad actor used the hash, which is a transformation from low-fidelity IoC to high-fidelity threat intelligence.
The real value of ATT&CK mapping is providing defenders with the comprehensive vocabulary to describe the behaviors that produce IoCs. This allows defenders to go beyond signature matches to an awareness of the larger adversarial strategy. Instead of simply focusing on static IoCs, this guidance looks for chains of anomalous or suspicious behaviors.
Its purpose is first to identify the initial compromise, and then of the subsequent post-compromise and “living off the land” tactics and techniques. This holistic, behavior-based approach, guided by ATT&CK insights, enables a more contextual and proactive cybersecurity defense.
Table: IoCs vs. IoAs: Comparative Overview
| Aspect | Indicators of Attack (IoAs) | Indicators of Compromise (IoCs) |
|---|---|---|
| Timing | Proactive—Prioritizes real-time attacker behavior, or during or before it occurs. | Reactive—Detected following an attack occurrence. |
| Focus | Attacker intent and behavior (e.g., TTPs) | Evidence of compromise (e.g., static artifacts) |
| Nature | Follow dynamic intent and behavior—Proactive | Follows known threat patterns—Reactive |
| Use case | Real-time threat detection, understanding attacker patterns, and avoiding damage | Incident response, forensic investigations, and blocking known threats |
| Examples | Phishing campaign, privilege escalation attempt, multiple failed login attempts, C2 beaconing (before data exfiltration), lateral movement. | Malicious file hash, unusual DNS request, C2 IP address, compromised user account, suspicious registry key |
| Context dependence | More context-focused, analyzes behavior resulting in an attack | Less contextual, depends on known data points |
IoCs and IoAs are complementary elements of a holistic system of defense against a cyber-attack.
Indicators of Compromise provide the “what” – specific evidence of an actual incident in the past to inform what measures the experts should put in place for prevention in the future. Indicators of Attack provide the “how” and “why” information and the TTPs that an attacker is engaging in. This allows a defender to intervene before the bad actors take further action that can lead to irreversible consequences.
A complete picture of an adversary’s campaign often involves several IoCs and IoAs. In such cases, one IoA may be evidence of some initial reconnaissance, leading to IoC, evidence of malware, followed by further IoA evidence of lateral movement.
A mature security organization will leverage both: IoCs as a method of hardening their defensive posture and evidence for forensic investigation. Then, they will use IoAs for a dynamic and live environment by disrupting or intervening in new attacks on their organizations.
What are the benefits of IOCs?
The identification, analysis, and response to any Indicators of Compromise can offer great advantages for organizations. These advantages extend beyond incident response but also affect the overall posture of the organization’s cybersecurity.
Faster Incident Response and Shortened Dwell Time
Perhaps the most important benefit of IoCs is the ability to have faster incident response and significantly shorten the dwell time of the threat actor on a network.
IoCs also provide concrete, actionable artifacts that security teams are able to look for, such as a file hash or IP address. When there are concrete indicators, analysts are able to establish scope within hours, not days/weeks. This differs from if you received high-level indicators, such as descriptions of techniques with the Kill Chain, blocking any meaningful response for a prolonged period of time.
When analysts need to perform a post-incident scope, a concrete indicator can lead to a fast, meaningful response, or supposedly possible response. The speed at which an organization can determine the extent of the attack will minimize the overall impact of the attack.
If an attacker is present on a network for an extended period of time, they are more likely to achieve their malicious goal: data theft or system disruptions. The faster an organization removes an attacker from a network, means less time they have to either escalate privileges in the network, move laterally, or cause damage. Hence, it minimizes the damage that could result from an attack.
How to Identify Indicators of Compromise: Practical Guide

In order to effectively protect your network, you need to do more than just react when you receive alerts; you need to hunt for the digital breadcrumbs left behind by a breach. Finding these Indicators of Compromise (IoCs) involves having the right tools, a methodical process, and knowing what to look for.
Here is a usable step-by-step guide to finding and tracking IoCs.
Step 1: Lay the Technical Foundation
Before you can begin hunting for IoCs, you need to have the technical foundation to base your hunt on. This is where modern security solutions are critical.
- Utilize a SIEM: A Security Information and Event Management (SIEM) tool is your central nervous system. It aggregates logging and event data from throughout your IT infrastructure—servers, firewalls, and endpoints. In other words, you need all the aggregated data to help you see the larger context and correlate events that may not have any direct relation.
- Utilize an EDR solution: A SIEM gives you a view of your network, whereas an Endpoint Detection and Response (EDR) solution gives you depth of visibility to spot activity happening on individual devices. EDR solutions run continuously on their respective endpoints to capture activity and allow detection of malicious processes, unauthorized file changes, and suspicious activity on the host.
- Connect a threat intelligence feed or TIP: A Threat Intelligence Platform (TIP) is the critical connective tissue between your internal data and the external cybersecurity community. Develop and configure to integrate a TIP into your SIEM. You will be able to cross-reference your internal logs against a managed list of IoCs that may include malicious IP addresses, domain names, and hashes.
Step 2: Start Thinking Like a Threat Hunter
Rather than just waiting for an alert, a threat hunter starts with a hypothesis, which enables the threat hunter to identify threats that automated tools may not have detected.
- Create a hypothesis: Your hunt will always start with a hypothesis—a clear question and an indication of what kind of activity you are trying to identify. For example: “There has been a new phishing campaign aimed at our sector. Have we had any anomalous traffic directed to any of the malicious domains associated with the phishing campaign?”
- Look for IoCs: Use your SIEM to construct queries that indicate known, specific indicators of compromise. Look in your network logs for any connections to known bad IP addresses or URLs. In your endpoint detection and response logs, look for files whose hashes match known malware. In one query, you can invalidate the hypothesis or find confirmations, which is very valuable information.
Step 3: A Real-World Example: From Alert to Action
To see how this plays out, let’s look at a real-world example:
- Alert: Your email gateway classifies a suspicious email as a distribution list of several employees. The email contains a link to a domain that is not on your threat intelligence feed.
- Network log: You immediately go to your network logs. You query for any traffic to the suspicious domain. You notice that two user machines have successfully connected to it. This is your first IoC.
- Endpoint analysis: Now, you pivot to your EDR and look at the two compromised machines. You look for any newly created files, processes, or registry keys created around the time of the connection the machines made to the network. You find a new executable file created, with a suspicious file hash.
- Cross-reference the IoC: You cross-reference the hash of the file and find it to be on a newly released threat intelligence list. You also see that the EDR tool indicates that the file attempted to create a new administrative user account, which is a behavioral IoC, and you now have a complete outline of the attack.
Step 4: Advanced Analysis – Go Further Than the Basics
For advanced threats that defeat traditional defenses, you will need to use more advanced techniques:
- Memory forensics: Attackers frequently try to run their malicious code directly inside a computer’s volatile memory (RAM) so they will not be detected by any disk-based scanning tools. Memory forensics is the analysis of a machine’s RAM for evidence of injected code, suspicious processes, or rootkit artifacts.
- Behavioral analysis: Advanced threats build their tactics around multiple behaviors (TTP, Tactics, Techniques, and Procedures) and do not exclusively rely on IoCs. By analyzing repetitive patterns (e.g., a user logging in unsuccessfully multiple times, having success on the next attempt but from an unusual physical location; an account escalating its privileges suddenly), we can find evidence of multi-stage attack activities that would lag under static defenses.
Key Tools and Technologies for IoC Identification

Successful IoC identification requires specialized cybersecurity tools, such as:
- Security Information and Event Management (SIEM) Systems: Focusing on centralizing, aggregating, and analyzing log data collected from throughout the environment in near real-time. They help correlate events to known IOCs, prioritize alerts, and can pull in threat intelligence feeds to help with the analysts’ decision-making process.
- Endpoint Detection and Response (EDR) Solutions: Constantly monitor endpoint devices (e.g., laptops, servers) for local suspicious activity and alert on anomalous processes, file movements, or access attempts.
- Extended Detection and Response (XDR) Platform: An XDR platform provides a comprehensive view by aggregating telemetry data across multiple security monitoring levels (e.g., endpoints, networks, email, cloud), providing a singular view of contextual data and promoting quicker investigations (time to confirm or eliminate).
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): Scan network traffic for malicious activity and proactively alert on signatures or patterns (signature-based); or if they observe communications outside of baseline behavior (anomaly-based). IPS can block suspect threats from occurring.
- Threat Intelligence Platforms (TIPs): Enumerate and normalize threat data from a wide variety of sources (e.g., Open Source Intelligence (OSINT), commercial threat feeds, Industry Specific (ISACs), and other vendors) and offer real or near real-time data on potential known threats or vulnerabilities. TIP includes IoCs to enrich contextual data. Much of this intelligence is gathered from places where cybercriminals communicate and sell stolen data. To understand where these IOCs often come from, it helps to know about the hidden corners of the internet they operate in. Our beginner’s guide on the dark web here explains this ecosystem in plain English.
- Malware sandboxing tools: Develop separate compartments to safely open suspicious files and review their live behavior, recording network activity, system changes, and exporting IoCs.
- Forensic analysis tools: For deeper investigations, analysts use tools like Exterro FTK and memory analysis frameworks such as Volatility to collect and preserve digital evidence, extract IoCs, and reconstruct the attack timeline.
Challenges and Limitations of IoCs
Indicators of Compromise offer a lot of opportunities, but they can also present issues and limitations. Taking time to recognize these issues and limitations will be important during the development of an approach to cyber resilience that doesn’t strictly rely on IoCs.
False Positives and Alert Fatigue
One challenge in managing IoCs is the risk of false positives, where legitimate activity is flagged as a threat. When security teams face too many of these, they can experience “alert fatigue.”
Alert fatigue occurs when analysts become desensitized and exhausted from constant low-priority, redundant, or irrelevant security notifications. This can result in:
- Burnout and staffing issues: Cognitive fatigue, emotional fatigue, and attrition rates can go up.
- Missed high-priority alerts: Actionable alerts getting buried will extend the time to make a response against the activity and increase the chance for a breach to go unnoticed.
- Decreased predictive AI performance: AI models will perform worse if they are trained on noisy data.
Alert fatigue often occurs when unfiltered telemetry overwhelms security tools, multiple poorly integrated tools create confusion, or teams rely on manual triage. Organizations can pursue strategies such as smarter alert prioritization, greater reliance on AI, and hyper-automation to manage alerts.
Reactive Nature and Evasion Techniques
IoCs act reactively, revealing that an attack has already occurred or a system has been compromised. When security experts detect an IoC, it often means some damage has already taken place.
Advanced threat actors and attackers continuously evolve to avoid detection based on IOCs:
- Short lifespan: Attackers will either change IP addresses, domain names, or file hashes, which are the most visible IOCs. That’s why Indicators of Compromise lists lose their effectiveness quickly — they become outdated shortly after each update.
- Polymorphic and metamorphic Malware: Polymorphic malware that impacts code or appearance each time it spreads (static polymorphic), once it infects a host, or metamorphic malware that rewrites its own code. All may evade effective defensive controls and detection based on signatures and IOCs after it has taken hold.
- Obfuscation: Attackers use obfuscation to hide malicious code through techniques, encryption, compression, dead code, XOR, etc., to evade effective detection.
- Living off the Land Attack (LotL): Attackers leverage legitimate, pre-built system tools (“LOLBins”) to now conduct malicious actions through “normal” administrative behavior with little, if any, index of an IOC.
- Fileless Malware: Operates exclusively in memory; therefore, it writes no files onto disk. This also means file-based IoCs are ineffective, as the malware will not leave behind an identifiable artifact.
- Zero-Day attacks: Exploit vulnerabilities that are unknown and unpatched; no signature of the plugin or vulnerability exists, so it completely circumvents detection systems.
Because of the complexity involved, security teams should implement IoCs as part of a broader detection strategy that includes behavioral analysis, anomaly detection, and advanced threat intelligence. A comprehensive detection implementation enables organizations to identify not only artifacts of compromise but also the various behaviors and TTPs of the attacker, providing resilient defenses.
Tips and Best Practices for Using IoCs
To use Indicators of Compromise effectively, organizations should adopt a continuous improvement approach involving all aspects of an incident response program.
Integration with the Incident Response Lifecycle
IoCs are a key element of the incident response lifecycle:
- Preparation phase: IoCs drive the development of an incident response plan, assign roles for the Computer Security Incident Response Team, and the selection of tools to help with detection and investigation. Threat Intelligence is essential to remain current.
- Detection & analysis phase: IoCs are located during this stage. Responders look for IoCs or surprising behavior using various security tools (IDS, IPS, SIEM, EDR) and use all their data to classify the incident threat type and ascertain severity.
- Containment & mitigation phase: Once an incident is confirmed based on the IoCs, the security team takes appropriate steps to contain an event from spreading (isolating a compromised system, blocking an IP, disabling an account, etc.).
- Investigation & eradication phase: A full forensic investigation occurs here, and IoCs can be useful to recreate all the specifics of the attack (when it happened, how it happened, what data was lost, and so forth), and how the team removed the attacker or malware.
- Recovery & remediation phase: The focus shifts to restoring normal operations. The experts restore data and configurations from a trusted and reliable backup, ensuring there are no viruses or backdoors (discovered through IOCs).
- Post-incident activity / Lessons learned: Analyze why the event occurred and ways you can prevent further occurrences. The use of IOCs can inform you about techniques the attackers used, which can be mapped to your security tools, incident response capabilities, and procedures to generate learning.
Proactive Threat Intelligence and Threat Hunting
IoCs create the building blocks for proactive threat intelligence and threat hunting:
- Threat intelligence: Threat intelligence, specifically tactical intelligence, focuses mainly on the first steps of immediate action. Purpose-built IoCs, such as IPs, domains, hashes, etc., are used to respond rapidly and efficiently to threats and need to be remedied.
- Threat hunting: IoCs are starting points that threat hunters leverage to actively look for indicators of compromise (IoCs) that went undetected by the automated solutions. Threat hunters are looking for specific artifacts on the network that indicate compromise and can help limit the damage that the threat actors cause by stopping incidents as early as possible.
- Sharing and standardization (STIX/TAXII): IoCs can be shared in a responsible manner across organizations to protect the community from imminent threats. There are standards, such as Structured Threat Information eXpression (STIX) and Trusted Automated eXchange of Intelligence Information (TAXII). They serve as a transport for threat intelligence and also as a shared language between organizations.
- Defensive signature creation: IoCs you have detected should all help to create a defensive signature that could exist in some sort of security tool. Some examples are with YARA rules, which classify malware based on patterns. Sigma rules provide a common way to describe detection rules across SIEM systems, and Snort rules provide a way to detect suspicious network traffic. By clearly embedding IoCs into these rules, the team may detect or stop the risk swiftly as a proactive measure against incoming threats.
Managing High Volume IoCs and Alert Fatigue
The management of a significant number of IoCs and the resulting alert fatigue lead to specific management processes that are cumbersome.
The following best practices are some mitigation potential actions:
- Automated detection tools: Using SIEM, EDR, and XDR capabilities to automate log and endpoint to find known IoCs, correlate events and rank, and prioritize alerts significantly reduces the manual workload.
- Intelligent alert prioritization: Automating alert prioritization allows for the highest priority alerts or most critical threats based on what could happen, threat intel context, asset importance, and attacker behavior, allowing teams to focus on the biggest problems.
- Contextual enrichment: Automatically collect and correlate multiple sources of data (User identity, asset characteristics, threat intelligence, including IoCs and TTPs, vulnerability information, historical data), then join that information together to give teams a better sense of the alert relevance.
- Customizing alert thresholds and rules: Customizing the alert thresholds and detection rules with the security tools to fit the organization’s environment and risk appetite will reduce false positives.
- Using AI and automation (SOAR): Artificial Intelligence capabilities in Security Orchestration, Automation, and Response (SOAR) platforms automate many SOC workflows. These workflows process high inbound alert volume by using natural language processing (NLP) to mine and correlate events. Human analysts can divert their focus to complex threats and use proactive threat hunting.
Continuous Improvement and Adaptation
Cybersecurity is an ever-changing landscape, with threat actors always changing. Therefore, IoC procedures must be managed on an ongoing basis.
- Regular updates: IoCs can become outdated rapidly because attackers change their IPs, domains, and file hashes constantly. So, an organization must update detection rules and threat feeds regularly.
- Behavioral analysis and anomaly detection: A broader detection strategy that includes both behavioral analysis and anomaly detection is an important approach to build upon. By establishing normal activity and identifying deviations from that established normal activity, unknown threats can be identified.
- Integration into the continuous improvement cycle: Incident response, based on IoCs, needs to be integrated and undertaken in a continuous improvement cycle.
Conclusion
Indicators of Compromise (IoCs) are important digital forensic indicators of a cyber-breach. While normally reactive, IoCs provide significant intelligence for proactive defense. Thus, in today’s cybersecurity landscape, organizations must advance. They are moving away from simply detecting static IoCs or behavior using AI/ML to enhancing IoAs and including frameworks such as the MITRE ATT&CK framework.
IoCs should be implemented through the incident response engineering life cycle and used in conjunction with your proactive threat intelligence function. With these concepts in mind, you can now turn reactive evidence into an adequate reaction and a defense-in-force, adaptable, and AI/ML proactive measure.
FAQs
Indicators of Compromise (IoCs) are traces of a breach that has been executed. A good example would be a malicious file hash or suspicious IP address. Indicators of Attack (IoAs) are, instead, focused on how an attacker behaves and his or her intent, suggesting that there is an attempt to carry out an attack. Both types of “indicators” are important to have in a robust security framework.
Certainly, IoCs can be false positives, which means that they can have characteristics of real activity that cause an alert for a benign event. This is why you need to correlate many indicators and additional context to support an actual breach before taking action, and potentially cause alert fatigue.
Many TIPs, security blogs, and ISAC-type information sharing communities all assemble lists of the latest IoC in cybersecurity related to ongoing threats. These feeds combine and normalize threat data from multiple sources to provide real-time information.