-
A newly advertised malware tool on dark web forums automates the theft of TRON blockchain cryptocurrency.
-
The drainer bot exploits TRON’s energy rental system to steal funds without victims needing TRX in their wallets.
-
Most of the crypto wallets used regularly are at risk, including Binance Web3, Trust Wallet, as well as TronLink.

On January 19, 2026, a threat actor with the name “KOLLEKTOR” published an advert on an underground marketplace for a 100% automated bot built to syphon virtual currency out of TRON wallets.
The major specialty of the tool is hunting for TRX and USDT, two of the key virtual assets on the TRON network. Considering the billion-dollar transactions that TRON handles every month and its role in moving stablecoins around, this drainer is a chronic issue. Anyone holding assets on TRON should be paying attention right now.
A Complete Theft Toolkit
So what exactly does this bot do? It’s packed with features that would make any crypto thief’s job easier. The malware can check wallet balances for both USDT and TRX holdings. It maintains a unified database tracking all confirmed target wallets. An integrated parser continuously monitors for approvals granted on vulnerable wallets, alerting operators the moment an opportunity appears.
The draining functionality itself is disturbingly versatile. Attackers can sign contracts that extract either specific amounts or completely empty a compromised wallet. The bot offers both manual control for surgical strikes and automated draining at the press of a button.
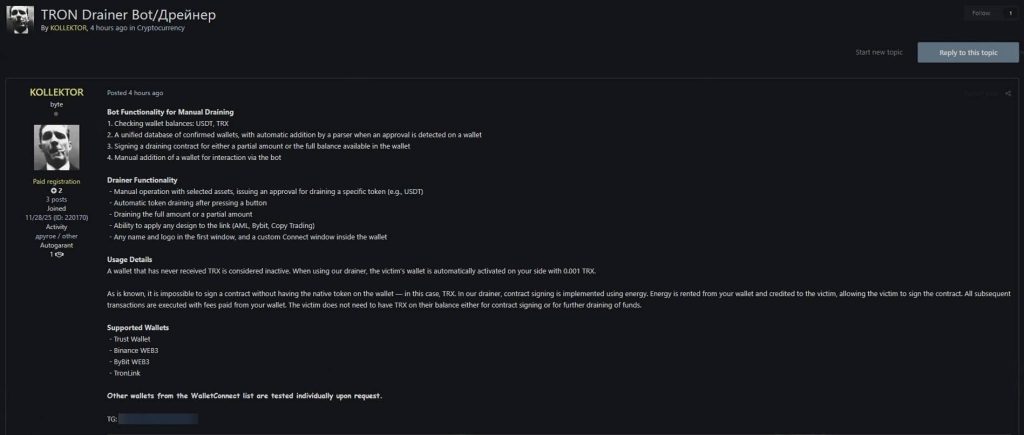
The drainer comes with built-in social engineering tools. Operators can customize phishing designs to mimic legitimate services. We’re talking about fake AML verification pages, counterfeit ByBit exchange interfaces, and bogus copy trading platforms. This focus on stealing stablecoins aligns with a broader shift among cybercriminals, who now favor these assets for their illicit operations.
Criminals can slap on custom names and logos to create convincing fake websites. Victims think they’re connecting to a trusted service. Instead, they’re handing over access to their entire wallet.
The Clever Energy Rental Exploit
The attack method reveals some genuinely clever criminal engineering. TRON’s blockchain uses an energy rental system for transactions. Normally, you need TRX tokens in your wallet to pay for these transactions. That’s been a natural barrier for scammers. Not anymore.
The drainer automatically identifies wallets that have never received TRX. These are considered inactive wallets. The bot then activates them by sending a tiny amount from the attacker’s own resources. Just 0.001 TRX does the trick.
This solves a major problem for cryptocurrency thieves. Victims no longer need to hold native tokens for transaction fees. The energy needed to sign the draining contract gets rented from the attacker’s wallet and credited to the victim.
The victim unknowingly signs the contract. After that, criminals can withdraw funds through additional contract signatures or execute further draining operations. It’s a complete workaround of typical blockchain security assumptions.
The malware works with several widely used wallets. Trust Wallet users are vulnerable. So are people using Binance Web3, ByBit Web3, and TronLink. The developer even mentioned that other wallets supporting the WalletConnect protocol can be tested on request. The potential reach extends far beyond the wallets explicitly named in the listing.
Safety Measures Amid Tension
This drainer bot showcases how sophisticated crypto theft tools have become. The combination of automated victim detection, convincing phishing capabilities, and technical bypasses for transaction fees creates an all-in-one attack platform. Even low-skill criminals can now execute complex crypto heists—a far cry from the earlier eras of cybercrime when simply moving dormant assets, like the recent $3.1 million in Silk Road Bitcoin, could make headlines.
If you’re holding assets on TRON, extreme caution is necessary right now. Be incredibly suspicious before connecting your wallet to any decentralized application or website. Don’t grant wallet approvals carelessly. Regularly review your wallet permissions and revoke anything unnecessary. If an offer seems too good to be true and requires a wallet connection, it probably is.
As blockchain finance continues expanding, we’re seeing specialized attack tools grow right alongside it. Better user education and stronger wallet security features aren’t optional anymore. They’re essential for protecting digital assets in this evolving threat landscape.