As you scroll through your favorite website, shop online, or check social media, an entire parallel internet is operating within the shadows. It is five thousand times bigger than what you encounter every day. IT IS THE DARK WEB – an invisible digital universe that is expanding faster than we ever anticipated.
The dark web is not the stuff of cyberthrillers anymore. It’s a real ecosystem that impacts millions of people on a global scale. Now, let’s take a look at the dark web statistics in 2026 to see the level of growth it has achieved so far.
Whether you are a cybersecurity specialist or you own a business but are worried about anyone collecting your data or exposing anything about you, don’t stop reading. What we have in this article will show you what the dark web is all about and how far it has gone beyond what you imagine.
Top 10 Dark Web Statistics and Trends
- The estimate of the total yearly revenue which the dark web makes from illegal activities is $1.5 billion. This huge amount of money is higher than the gross revenue of many companies that fall under Fortune 500, simply proving that underground criminal economies are more massive than people think.
- The people in the United States using the dark web make up 21.43% of all daily users of the space globally. With hundreds of thousands of Americans accessing hidden networks daily, the US leads the world in both legitimate privacy protection and harmful illegal activities.
- Bitcoin represents over 98% of all dark web transactions. The cryptocurrency has become the go to currency which hidden networks use for their financial transactions. According to available information, almost all the illegal marketplaces & services all over the world are using it.
- The number of stolen credentials that existed on the dark web in the first half of 2022 was more than 15 billion. This massive breach represents enough compromised login details to give every person on Earth two stolen accounts.
- The number of websites working actively on the dark web in 2025 increased by 44% year-over-year, hitting nearly 30,000. The hidden internet is growing so much faster than the regular internet. It is seeing more and more activities over the years than the normal web.
- Approximately 60% of all dark web websites engage in illegal activities or contain stolen data. More than half of hidden network content involves criminal enterprises, making it a predominantly illicit digital ecosystem.
- An estimated 20% of all drugs sold globally are now distributed through dark web platforms. This figure represents a well organized network distributing drugs internationally which already makes up to billions in US dollars every year.
- Cybercrime-as-a-Service products grew by 300% from 2016 to 2022. Criminal services have changed from they were to become more professional in their dealings making it easier for criminals without much skills to carry out sophisticated attacks on the internet.
- The dark web is now bigger than the normal web many people know and use by 5,000 times. The hidden internet vastly dwarfs the regular internet in terms of content volume and accessible information.
- Over 2.5 million unique individuals access dark web platforms daily. This represents a substantial global user base consistently engaging with hidden networks for both legitimate and illegal purposes.
Key Dark Web Stats
- The Dark Web Intelligence Market reached USD 520.3 million in 2023. Some estimations say it will increase to USD 2,921.8 million by 2032. That’s a 21.8% increase in most tech industries.
- It is estimated to be 5,000 times larger than the surface web you use every day. It is like comparing the size of a small town to that of an entire continent.
- Over 1.5 billion people access the dark web per year. That is greater than a few small countries worth of people searching and in this hidden area.
- Approximately 60 percent of all websites on the dark web are used for illegal purposes.
- It was reported in 2024 that the average total revenue for illegal activities on the dark web online per year is an estimated $2 billion.
- For context, this number is larger than the gross revenue of some Fortune 500 companies.
- Bitcoin is the preferred currency within the Dark Web, where it is used for over 98% of all transactions. There are about 30,000 active hidden services on the dark web.
- The US has the highest number of users on the Dark Web, followed by Germany, France, and the UK.
What is the Dark Web?
Before we really talk about the statistics, let’s try and understand what this seemingly mysterious space means. You can liken the dark web to an iceberg that has many layers, meaning that you see something different on the surface, not knowing it has more to it than that.
The main deal exists as an encrypted section of the internet that is completely invisible to regular search engines, such as Google or Bing. You can’t just enter a web address and find it. You must have specialized software to access this hidden network.
The one software you need, which everyone knows as a “dark web browser,” is the popular one called Tor (The Onion Router). Tor has many layers of encryption through which it bounces your internet connection to stop other people or monitoring tools from seeing your movement on the internet.
You can think of it as the VIP section of the internet – except instead of celebrities and champagne, you will find anonymity seekers, privacy supporters, and a lot of illegal activity.
Size and Explosive Growth of the Dark Web

The dark web online presence is growing in perpetuity in a way that is simply remarkable. These numbers represent an ecosystem that is not only surviving – it is thriving and growing at rates that are unprecedented.
Today, researchers estimated that there are roughly 30,000 active websites on the dark web. But here’s the kicker – that number has increased 44% year over year.
These comparisons from the hypothetical past show that the dark web online growth is outpacing the growth of the regular internet. In terms of dark and black markets, the on-line drug trade alone supports roughly 1,000 active marketplaces.
That is 1,000 separate online retailers of products ranging from prescribed medications to dangerous narcotics. Each market is similar to online commerce, but with rating and review systems, customer service support and money-back guarantees.
Breach of Data
The most worrisome component about dark web online growth in use is the growth in stolen data. Security researchers have indicated that in the first half of 2022 they identified over 24 billion stolen credentials being transacted on dark web online platforms.
That’s enough stolen login details to give everyone on the planet two compromised accounts. Take a moment to consider your own digital life. Your email passwords, banking information, social media accounts – some of that information could already be available in these darkened marketplaces.
Dark Web General Statistics Worldwide
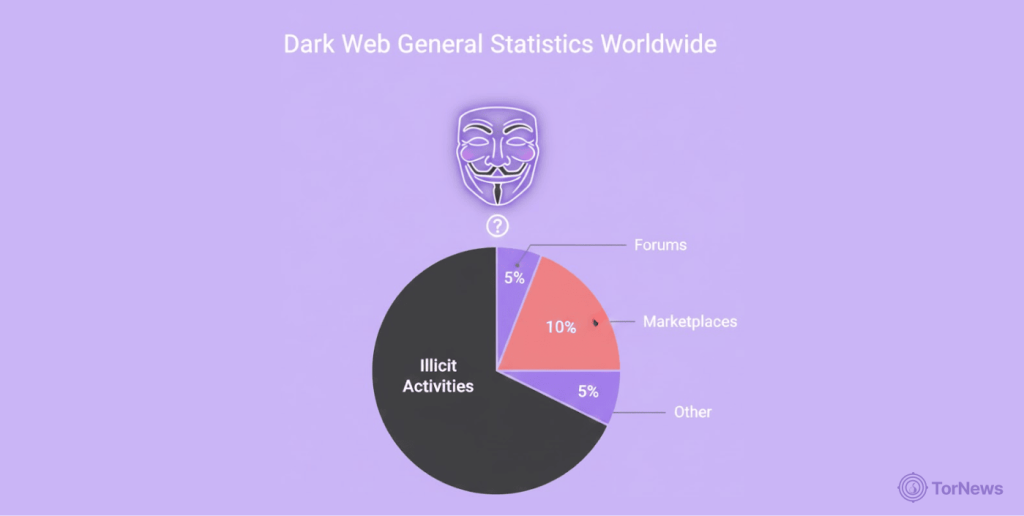
- The dark web is a breeding ground for illicit activities, with approximately 56.8% of its content being illegal.
- It’s estimated that 2.5 million people visit the dark web daily, and around 28% of the population in BRICS countries are familiar with it.
- Cybercriminals can purchase premium quality malware attacks in bulk, with 1000 attacks costing around $5000.
- Stolen credit card data is also readily available, selling for as low as $25.
- Phishing is the general method most criminals use to gather people’s financial data and weak passwords like “qwerty” & “123456” are often easy to get on the dark web.
- Many researchers expect the market for dark to reach $1.3 billion by 2028, showing it grows at a yearly compound rate of 22.3%.
- Hidden Wiki was the most popular search engine on the dark web and it recorded a leak that exposed more than 1.2 million payment cards in 2022.
- Cybercriminals heavily utilize dark web data for attacks, with 65% of active criminals relying on it.
- A staggering 80% of email data has been leaked to the dark web, and male users outnumber female users on the platform.
- Furthermore, 78% of users rely on commercial threat intelligence feeds for information.
- The dark web also sees a significant number of domains impersonating major e-commerce platforms like Amazon and Alibaba.
- In the US, 52% of companies have implemented dark web threat intelligence policies to combat these threats.
Average Number of Tor Users Daily by Country
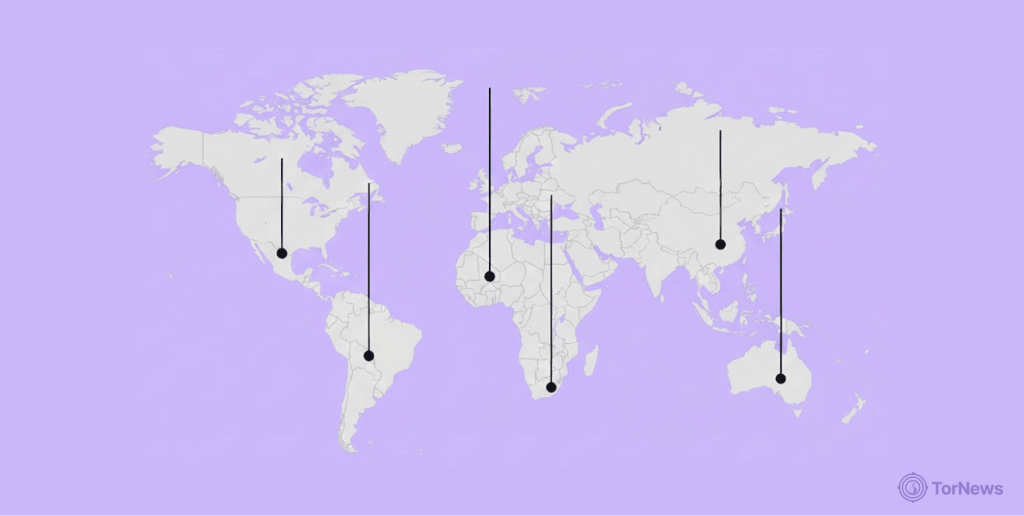
- The United States leads the world with approximately 21.43% of global dark web online users, potentially hundreds of thousands of daily repeat users! America also has a unique combination of many users who want legitimate privacy protection, but simultaneously lead in many categories that pertain to the most harmful illegal activities.
- Germany follows America, including 12.93% of users. This situation has a significant influence in both privacy awareness in internet users and law enforcement advancements. German citizens place more importance on their privacy than many other countries, maybe due to their history and of course several laws that protect data in the country.
- Finland has a surprisingly high prevalence at 5.22% – astonishing for a nation of only 5.5 million. This indicates that Finns are likely some of the most privacy-conscious internet users in the world.
- At a regional level, Europe has higher overall dark web online adoption, as France has 3.43%, Netherlands at 2.71% and the UK at 2.58% that all contribute a baseline use.
The European region may be reflecting specific privacy laws and attitudes around digital rights.
- Asia shows very diverse usage rates in relation to everything else.
- The rate for India cut-down by its enormous population is at 3.97%.
- Indonesia is contributing 3.02%.
Countries with more advanced sovereign internet censorship often have higher usage rates because their citizens tend to seek the most unencumbered access to potential information sources.
Statistics for Illegal Activities on the Dark Web
Drug Trade Stats
The illegal drug trade is by far the single largest area of illegal activity associated with dark web online platforms. Current estimates suggest that about 20% of all drugs are sold globally via dark web online platforms. This isn’t just small scale personal use – it’s a sophisticated international drug distribution network whose annual valuations are in the billions of dollars.
By 2022, experts found over 44,000 drug advertisements, not ads in a classified or storefront way, websites with multiple listings of different products, descriptions, prices, and photographs, and in some cases customer reviews. Almost all of the vendors provide equally good customer service, money back guarantees, and dispute resolution services to their customers.
Cybercrime Services
If illegal drugs weren’t concerning enough, you start to see the emergence of offerings by companies that are operating in the “Cybercrime-as-a-Service” vertical.
From 2016-2022, the availability of these services expanded by 300%, indicating substantial professionalization of cybercrime.
What does this mean, practically? You can now ‘hire’ a cybercriminal like any service. Hacked email? It’s a service. DDoS attacks to take down a website?
You can find multiple vendors with competitive rates. Stolen credit card numbers? You can now buy botnets to execute premium quality malware attacks, exploring online offers for lower deals – like purchasing 1000 attacks for $5,000.
Financial Fraud
Financial fraud activities make up more than 34%, and follow illicit drug sales as the second largest category of the dark web online.
Here are some staggering financial fraud statistics from the dark web online:
- Over 100 million compromised credit card details were available for purchase in 2022.
- Stolen credit card number as low as $25?
- In 2022, law enforcement seized more than $22 million worth of counterfeit currency in the United States that was linked to dark web online activities.
- Data breaches reported estimated global losses of $2.7 billion in 2021.
Weapons Trafficking
Weapons trafficking reports illustrate the dark sides of humanity, even though it only represents 0.3% of all dark web online content.
Researchers uncovered more than 35,000 weapons criminals listed for sale across dark web online marketplaces in 2022. Some of the weapons they found for sale were ammunition, explosives, firearms, and many other types.
Checking the sales of weapons by geographical locations revealed a shocking pattern which showed that the US alone sold 58% of the weapons while Europe and Russia covered 11% and 7%.
This information can clue law enforcement on trafficking routes, and help them in their interdiction efforts.
Human Trafficking and Exploitation Stats

There are disturbing human trafficking statistics as reported on dark web online platforms.
Although the International Labor Organization (ILO) estimates there are 25 million human trafficking victims, it is difficult to estimate what subset of this is facilitated through online transactions in the dark web considering these crimes occur in the dark.
What we do know is troubling: For example, 79% of human trafficking cases are for sexual exploitation, and 18% of trafficked people are trafficked for forced labor.
Dark web online platforms allow traffickers to coordinate with each other, perform payment transactions for an illegal service, and recruit victims and clients.
Dark Web Stats by Categories
Understanding what actually gets traded on Dark Web online platforms requires examining the specific categories of content and commerce.
These dark web statistics reveal a disturbing hierarchy of illegal activities.
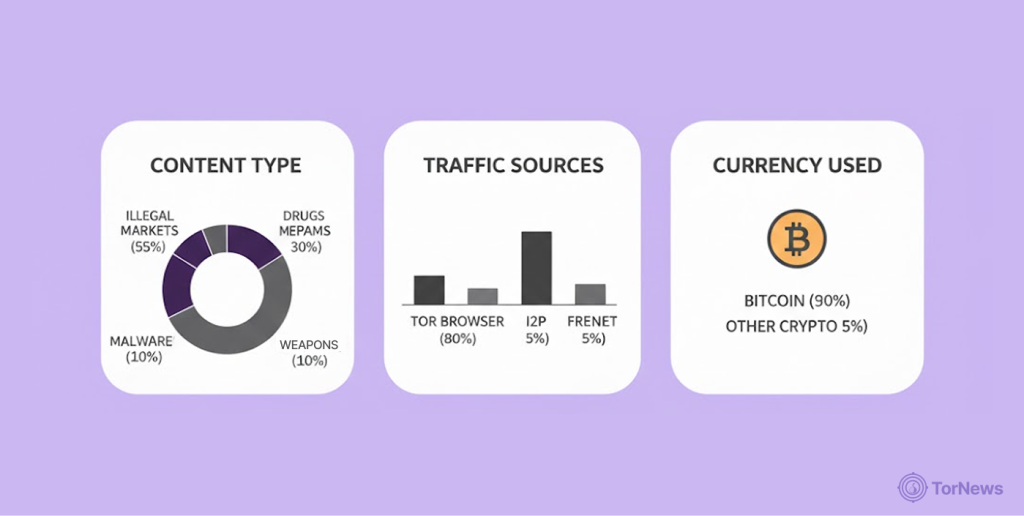
Illegal File Sharing (29%)
The largest category, representing nearly one-third of all dark web content. Among them are pirated software, copyrighted materials, and digital content that other people sold without getting the authority to sell from the owners.
While this might seem like nothing when you compare to other categories, it still means that legitimate businesses lost billions of dollars due to these underhand activities.
Leaked Data (28%)
Almost matching illegal file sharing, leaked data comprises stolen databases, personal information, and confidential records from various data breaches. This category directly affects millions of innocent people whose information was stolen from legitimate businesses.
Financial Fraud (12%)
Representing over one-tenth of dark web content, financial fraud includes stolen credit card information, banking details, and methods for conducting fraudulent activities.
The sophistication of these operations rivals legitimate financial services.
News Media (10%)
This category includes platforms sharing illicit activities, cybercrime news, and underground developments. While some might serve legitimate journalistic purposes, much focuses on facilitating criminal coordination.
Promotions (6%)
Dedicated to advertising various illicit products and services, this category shows how Dark Web online markets have adopted sophisticated marketing techniques.
Discussion Forums (5%)
This is where users simply talk about illegal activities, techniques to hack people’s accounts and other sensitive subjects. These forums simply train criminals that are still trying to learn the ropes of the game.
Drugs (4%)
Despite media attention, drug sales represent only 4% of dark web content by volume, though they likely represent a much higher percentage by transaction value.
Hacked Accounts (3%)
These are accounts that sell login credentials & personal information, which they stole from other people and sell in bulk to criminal buyers.
Pornography (1%)
Illegal and exploitative materials that represent some of the most disturbing aspects of dark web content.
Weapons (0.3%)
Looking at the volume, this category seems small but it is the most dangerous as dangerous weapons exchange hands for illegal activities. These percentages show how the dark web economics function and how users react to its products.
For instance, the high number of file sharing & leaked data show that more people on the dark web buy and sell information rather than physical goods. This digital focus makes transactions easier, faster, and harder for the authorities to do their work properly.
Dark Web Statistics 2025 by Country
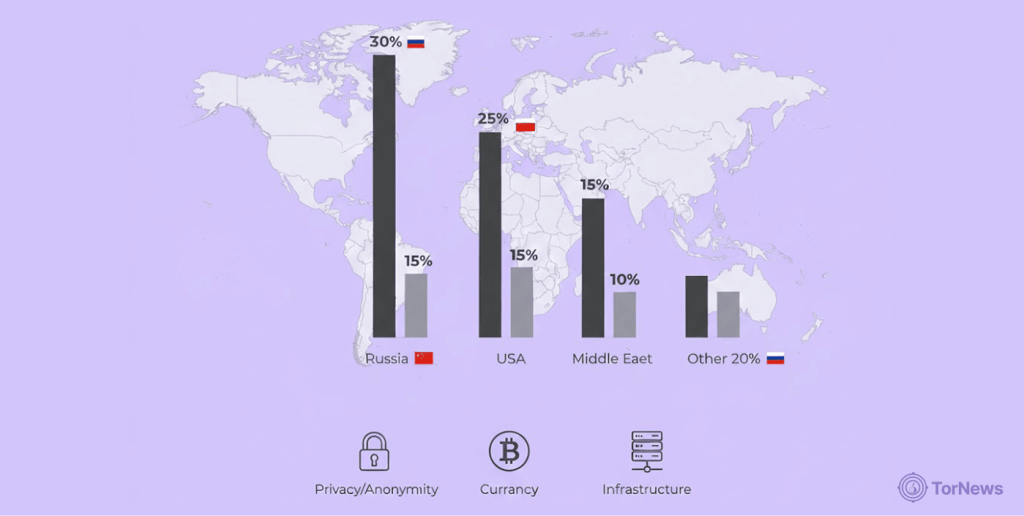
When someone asks “which country has the most dark web users“, the answer provides an interesting perspective on digital privacy, internet freedom, and security in different countries.
Let’s examine dark web statistics 2025 by country in much greater detail, revealing how different nations interact with hidden networks and what these patterns mean for global cybersecurity.
United States
The US leads virtually every dark web metric, but the details reveal a complex relationship with hidden networks:
- American vendors dominate weapons sales (60% of all listings) and financial fraud operations
- 52% of US companies have implemented dark web threat intelligence policies, showing growing business awareness
- Over 15 billion stolen credentials discovered in the first 6 months of 2022 alone, with American data heavily represented
- Approximately 80% of email data has been leaked to dark web platforms, affecting virtually every American with an email address
- Strategic intelligence remains the most difficult type of data to collect from US dark web operations
Germany
Germany’s relationship with the dark web reflects both high privacy consciousness and serious law enforcement efforts:
- 7.16% of global dark web users, translating to approximately 171,009 daily users
- German police dismantled Hydra Market, seizing $25 million in Bitcoin and shutting down a platform facilitating $1.34 billion in annual transactions
- Hydra Market alone had 17 million customer accounts and 19,000 registered sellers before its takedown
- High adoption rates reflect German cultural emphasis on privacy rights and data protection
United Kingdom
The UK’s dark web landscape reveals interesting patterns:
- Approximately 5% of UK internet users have accessed dark web platforms at some point
- UK authorities shut down DarkMarket in 2020, which had over 2,400 vendors and nearly 500,000 users
- Cybercrime costs the UK economy an estimated £27 billion annually, with dark web platforms playing a significant role
- 24% of UK dark web listings are drug-related, showing this remains a primary use case
France
- The Netherlands has a significant presence on the dark web.
- Approximately 6.92% of dark web users worldwide are connected from the Netherlands.
- This percentage translates to an estimated 165,281 users per day.
Russia
Russia’s influence on dark web content far exceeds its user percentage:
- Russia-based anonymous websites comprise over 36% of collected dark web intelligence
- Over 300 million pages in Russian language have been indexed across anonymous networks
- Only 3.50% of daily users, showing how content creation and consumption patterns differ
Netherlands
The Netherlands shows remarkably high dark web engagement:
- 6.92% of global dark web users from a country of only 17 million people
- Approximately 165,281 Dutch users access dark web platforms daily
- Dutch users are more interested in electronics on the dark web, narcotics, buying and selling of firearms and hard drugs.
Emerging Markets and Regional Patterns
- 28% of the people living in Brazil, Russia, India, China, & South Africa now have more knowledge of the dark web. This shows that more people all over the world know that it exists.
- Countries like Indonesia (3.02%) and India (3.97%) are also coming to know about the dark web although they are not yet using it much because they might not have the infrastructure to use it or their knowledge of the digital world is still not much.
- European countries altogether show a higher rate of adoption proving they value their privacy and have more digital knowledge across the region.
Recent Developments
Law enforcement agencies all over the world are developing new and harder ways of handling the crimes that take place on the dark web online.
The global law enforcement community is trying to assess and understand how they can carry out their jobs on hidden networks, the challenges they have faced in the past and the successes achieved.
Law Enforcement Operations
- In 2020, law enforcement agencies started what they called “Operation Disruptor,” a strong effort to take down dark web marketplaces that sell illegal goods and services.
- The operation brought in good results, with authorities seizing more than $6.5 million in cash & virtual currencies. They also caught many people carrying out the dark web activities, causing a heavy blow to the underground market.
Market Consolidation
- In 2021, the authorities closed “ Evolution Marketplace”, one of the largest dark web marketplaces.
- This very operation interrupted the buying and selling of illegal goods, including drugs & data stolen from web users. The success of the move caused dark web transactions to reduce a lot.
Funding
- Cybersecurity companies are receiving huge amounts of funds to develop high-class dark web monitoring tools.
- For instance, DarkOwl received $10 million to improve the dark web intelligence platform, helping businesses find out more about cyber threats and also prevent it on time.
Market Size
- The dark web economy is massive, even with the efforts of the authorities to stop some of their activities.
- It hasn’t been easy to pinpoint the main size of that hidden web due to how they operate in secret but some experts estimate that it makes billions of dollars each year. All this money comes from selling illegal goods & services of which drugs, counterfeit items, & stolen data are part of it.
Innovation in Crypto Technologies
- Dark web users are now relying on some cryptocurrencies that focus more on privacy to carry out transactions in secret and avoid the authorities’ eyes. Some of these assets they use in place of money are Monero and Zcash.
- These coins believe in hiding the transactions of their users and offer them more security than traditional ones like Bitcoin, meaning they are more suitable for illegal activities that go on between users on the dark web.
Regulatory Efforts
- Governments all over the world are trying to reduce the threats of the dark web by relying on legislative measures to fight those bad actors and boost the defence of cybersecurity.
- Some of these efforts are the move to watch more of their activities, increase the penalty against those who commit cybercrimes. They are also joining hands with international authorities to intervene in the activities on the dark web.
Deep Look on Dark Web Attacks: Understanding Cyber Threats in the Modern Times

Malicious hackers working on Dark Web online platforms now use very advanced techniques to carry out cyber attacks, breach people’s security, and steal data
Understanding the methods they use in their attacks is very important in fighting against cyber threats in this modern times.
Malware Attacks
Dark web hackers a lot of malicious software that they create to harm or gain access to computer systems:
- Keyloggers: These programs secretly record all the keystrokes someone makes on any computer that has the hacker’s software in it. The aim of this is to capture people’s passwords, credit card numbers, and other information an individual or organization wants to keep private. Dark web vendors sell very advanced keyloggers that can overcome many antivirus software and go on with their target activity for months and no one will notice.
- Ransomware: This particular attack can really devastate the victim because it encrypts the files on the target device and asks them to pay money before they send a key to unlock them. Modern ransomware activities now work like a business that even has a customer care office and even some agreements in between.
- Trojan Horses: These programs come in a package that seems like they’re legitimate but secretly gives the bad actors a back door to steal from the systems they enter. Some of the trojans from high class criminals can even steal data, install more malware, and open up a door through which their owner can continue stealing from the target network.
DDoS Attacks
Distributed Denial of Service attacks hits the target networks with a high flow of traffic, preventing real users from accessing the victim’s websites & online services. Dark web criminals use several top-notch ways:
- Botnet operations: Criminal networks own and use thousands or millions of computers infected with viruses (called “bots”) that they use to attack specific targets.
- Interested persons can buy, sell or rent these botnets, on Dark Web online marketplaces like any other product we use.
- Amplification attacks: Sophisticated dark web operators use techniques that multiply the impact of their attacks, allowing relatively small botnets to generate massive amounts of attack traffic.
- Targeted business disruption: Many dark web DDoS services specifically target businesses during critical periods like Black Friday sales or product launches, maximizing financial damage.
Social Engineering
Dark web criminals increasingly focus on manipulating people rather than just attacking technical systems:
- Phishing evolution: Phishing attacks in this modern times use information criminals gather from dark web data breaches to carry out communications that usually seem so real and truthful. Criminals can mention some specific details about a targets’ lives, making it harder for the victim to suspect they’re frauds.
- Phone-based attacks: Dark web forums share methods which criminals can use to carry out misleading phone calls that convince victims to reveal their secret information or carry out actions that lead them to doomsday.
- Pretexting Operations: Criminals create elaborate fake scenarios and identities to manipulate targets into providing information or access. These operations often involve multiple dark web specialists working together over weeks or months.
Credential-Based Attacks
With billions of stolen credentials available on Dark Web online platforms, credential-based attacks have become increasingly common:
- Credential stuffing: Automated systems try stolen username/password combinations across thousands of websites, exploiting people’s tendency to reuse passwords across multiple accounts.
- Account takeover: Once criminals steal your credentials and open your account, they change the password and the recovery information, removing the original account owner and taking over completely.
- Lateral movement: If criminals enter a business environment, they use credentials they stole from the employees to enter internal networks and perform high levels of data thefts there.
Advanced Persistent Threats (APTs)
Some highly criminal organizations that are very organized and sophisticated carry out long-term, quiet campaigns:
- Multi-stage attacks: These operations go on over months or years, with criminals gradually gaining more access & gathering intelligence before they carry out the final attacks.
- Supply chain infiltration: Advanced dark web groups target sellers of software & services, using infected products to attack end users indirectly.
- Zero-day exploit trading: Dark web markets facilitate trade in previously unknown software vulnerabilities, allowing criminals to launch attacks before victims can deploy protective measures.
Industries Most Vulnerable to Dark Web Attacks
While no organization can completely avoid dark web threats, certain industries face more risks due to the nature of their data, how they operate, & their security infrastructure.
Education and Research
Educational institutions have become the primary target of dark web criminals, experiencing a 43% increase in attacks during 2022 compared to 2021:
- Why Schools are vulnerable: Educational institutions often keep little money for cybersecurity. Secondly, they usually have different user bases including students & faculties with different levels of technical skills,& large amounts of personal data including social security numbers, financial information, & academic records.
- Attack methods: Dark web criminals target schools using ransomware, data theft operations, and credential harvesting attacks. Student information is particularly valuable because it includes young people who may not monitor their credit reports regularly.
- Long-term impact: Attacks on educational institutions can cause harm to thousands of students & faculty members, wreaking havoc on both their privacy and finances which affects the larger communities.
Healthcare and Pharmaceuticals
Attacks from dark web operators on the healthcare industry increased by 86% year-over-year, making it the second most targeted sector:
- High-value data: Medical records sell for significantly more than basic financial information on Dark Web online marketplaces. Complete medical profiles can fetch hundreds of dollars each, compared to stolen credit card numbers that sell for under $25.
- Life-safety implications: Dark web attacks on healthcare systems don’t just threaten privacy – they can directly endanger patient lives by disrupting critical medical systems and delaying emergency care.
- Pharmaceutical targeting: Drug companies face different kinds of threats which might come in the form of stealing of intellectual property, breaching of data from clinical trials & attacks that cause issues in drug supply chains.
Finance and Insurance
Despite heavy security investments, financial institutions remain prime dark web targets:
- Direct financial value: Successful attacks on banks and financial institutions can provide immediate financial returns for dark web criminals through fraudulent transactions and account takeovers.
- Trust and reputation: Financial institutions face severe reputational damage when customer data appears on Dark Web online platforms, potentially leading to customer defection and regulatory penalties.
- Regulatory scrutiny: The regulatory requirements which the authorities place on financial institutions for data protection is usually high making data breaches from dark web particularly costly because it makes the institutions violate these laws and pay penalties.
Public Administration
Government agencies face unique dark web threats:
- National security implications: Data breaches that take place in government institutions can affect national security, diplomatic relations, & public safety in ways that are deadlier than individual privacy concerns.
- Citizen data exposure: Government agencies hold massive databases of citizen information, making them a hunting ground for brokers operating on the dark web data.
- Critical infrastructure: Any attack on government systems can lead to serious interruptions to important public services like emergency response during catastrophes, public health systems for the citizes, & social services.
Retail Sectors
Retail companies face significant dark web threats due to their extensive customer databases:
- Payment card information: Retail companies process millions of payment card transactions, creating attractive targets for dark web financial fraud operations.
- Customer profiling: Retail customer data helps dark web criminals create detailed profiles for identity theft and targeted fraud operations.
- Supply chain vulnerabilities: Retail companies often have complex supply chains with multiple technology vendors, creating numerous potential attack vectors.
Emerging Target Industries
Several industries are experiencing growing dark web threat levels:
- Technology companies: Ironic given their security expertise, tech companies face increasing attacks targeting intellectual property, customer data, and internal communications.
- Legal services: Law firms possess sensitive client information and confidential legal documents that command high prices on Dark Web online marketplaces.
- Real estate: Real estate companies handle significant financial transactions and maintain detailed personal information about buyers and sellers.
Dark Web Trend Outlook for 2025: What’s Coming Next
The dark web has continued to change very fast , and a thorough understanding of these changes can help different organizations and individuals prepare for future threats. Some very important developments will influence the future of the hidden internet.
Evolution of Cybercrime Motivations
Dark web criminal motivations have evolved significantly over the decades:
- 1980s Foundation: Early hackers were primarily motivated by curiosity and technical challenges, breaking into systems to prove it could be done rather than for financial gain.
- 2000s Commercialization: Microsoft’s decision to pay “white hat” hackers for finding out the vulnerabilities in Windows made ethical hacking legal. At the same time it showed the criminals that they can actually make money through hacking.
- 2010s Ransomware Revolution: The increase in ransomware method of attacks, especially “big game hunting” operations that attack large corporations & government agencies, showed that committing crimes on the web could help criminals make huge amounts of profits.
- 2025 AI Integration: Dark web criminals in this modern times are using more of artificial intelligence (AI & machine learning (ML) to make attacks automatic, select targets, & carry out their evil activities without detection by systems on ground.
Technological Advancement Trends
- Artificial intelligence proliferation: Dark Web online platforms are adding AI tools that make social engineering attacks automatic these days. These tools also help them create phishing content that victims believe easily, & also make their criminal operations very successful. At the end, they go away with huge profits without any authority catching them.
- Quantum computing reparations: While still years away before implementing it practically, quantum computing threatens the encryption standards that exist now. Dark web communities are already talking about post-quantum cryptography & preparing for a future where the security measures of today will no longer work.
- Mobile-first criminal operations: As the use of smartphones continues to grow all over the world, dark web criminals are developing platforms that are accessible through mobile phones plus techniques to attack mobile devices & applications.
Market Structure Evolution
- Professional service standards: Dark Web online marketplaces are now using highly advanced business methods such as having customer service guarantees, carrying out professional dispute resolution, offering standardized pricing methods, & using performance metrics that are almost better than legitimate businesses.
- Geographic decentralization: Criminal operations are spreading to different jurisdictions that have enforcement practices against those committing cybercrimes thereby making things more difficult for law enforcement cooperation among international bodies.
- Niche market development: Dark web markets that specialize in different crimes, customer segments or geographic regions are popping up making it very difficult to detect & disrupt them.
Privacy Technology Arms Race
- Enhanced anonymization: New privacy technologies beyond Tor are emerging that offer even stronger anonymization features, making user tracking nearly impossible even for sophisticated law enforcement agencies.
- Blockchain integration: Dark web platforms are boosting their activities more with blockchain technologies & decentralized systems that makes taking them down with the usual methods much more difficult.
- Cryptocurrency evolution: More people are using those cryptocurrencies that protect users’ privacy on Dark Web online platforms. These crypto coins make sure that those who use them for transactions stay more anonymous than even what Bitcoin offers.
Societal Impact Predictions
- Mainstream privacy awareness: The increase in surveillance concerns & incidents of data breaches are pushing more legitimate users to consider privacy technologies, which is indirectly leading them to use the dark web more.
- Regulatory response intensification: Governments all over the world are developing more effective approaches to regulating the dark web and some of them include more international cooperation frameworks & new technologies for surveillance.
- Corporate defense evolution: Businesses are investing more money into dark web monitoring & those intelligent services that help them detect threats, and this is creating a legitimate cybersecurity industry focusing more on defending organizations against threats coming from hidden networks.
The Future of Cybersecurity on the Dark Web

The fight that has been going on between criminals on the dark web and cybersecurity experts will not stop any time soon as both sides are developing more powerful tools & methods to outsmart the other one.
Artificial Intelligence & Machine Learning Integration
- Criminal AI adoption: Criminals on the Dark Web are leaning heavily on artificial intelligence to enable them to select their victims, exploit their vulnerabilities and attack them automatically. AI-powered tools can pick the targets that are more vulnerable, create social engineering attacks that are more personal to the target, and utilize attack techniques that will work in real-time to confuse detection systems.
- Defensive AI response: Experts in cybersecurity are developing defense systems that have AI capabilities that can analyze communications on the dark web, identify the likelihood of threats in these communications, and predict attack patterns before they occur. These systems process huge amounts of data from the dark web to provide warning of imminent attacks earlier before they occur.
- Machine learning arms race: Both criminals and defenders are using machine learning algorithms to stay ahead of their opponents. Criminal ML systems learn from successful attacks and adapt to new security measures, while defensive ML systems learn from attack patterns and develop predictive models.
Enhanced Social Engineering Tactics
- Psychological profiling: Dark web criminals are coming up with advanced techniques for psychological profiling that study people’s posts on social media, their public records, and their past data that leaked mistakenly to create personality profiles of potential victims.
- Deepfake technology: Advanced dark web operations are beginning to use deepfake audio and video technology to impersonate trusted individuals in social engineering attacks, making deception much more convincing.
- Multi-channel campaigns: Social engineering attacks these days pass through many communication channels – email, phone, social media, & text messages – to create consistent narratives that are much harder for victims to perceive as a threat.
Privacy and Anonymity Evolution
- Next-generation anonymization: Dark web users and operators are developing anonymization technologies that go beyond current Tor capabilities, including quantum-resistant encryption and distributed systems that make traffic analysis nearly impossible.
- Decentralized platform architecture: Future Dark Web online platforms may operate on fully decentralized architectures that make traditional takedown operations ineffective, requiring entirely new law enforcement approaches.
- Privacy rights balance: Society must achieve a balance between legitimate privacy needs against their concerns for security, especially as privacy technologies become more effective & easily available.
Cybersecurity Defense Evolution
- Proactive threat hunting: Organizations are no longer pursuing security measures that react after an attack. Instead, they’re now hunting threats in their networks & on the dark web regularly to prevent attacks from occurring.
- Threat intelligence integration: Modern cybersecurity operations combine dark web intelligence with traditional security monitoring to provide threat awareness that covers every aspect of criminal activities & develop approaches to respond to threats.
- Collaborative defense: threat sharing initiatives that broadens to industry level allow organizations under such industries to join hands against threats from the dark web by sharing attack indicators & techniques to defend against them.
Protecting Dark Web Sites & Businesses
Safeguarding an organization against threats that come directly from Dark Web online platforms need a broader multi-layered approach that will handle problems in the technical operations of the organization & mistakes that human beings caused.
Dark Web Monitoring: Your Early Warning System
- Continuous surveillance: An attentive monitoring of the dark web platforms to notice when people mention your organization, when there is a leak in employee credentials, and other proprietary information is a good step in detecting early warning signs of potential threats. Some important things to do here is to go through marketplaces, check forums, and other channels of communication where criminals carry out their attacks and sell stolen data.
- Automated alert systems: Implementing monitoring systems that can scan Dark Web online platforms automatically for specific keywords related to the industry, domain names, or data patterns will notify you instantly when your organization’s information appears in criminal networks.
- Brand protection: Monitoring to find counterfeit products, infringements of trademark, & impersonation of brand on dark web marketplaces helps protect both your organization & your customers from fraud & damage to reputation.
Dark Web Monitoring Services: Professional Protection
- Comprehensive coverage: Dark web monitoring services that operate professionally provide surveillance of hidden networks 24/7, with special tools & expertise that individual organizations cannot get and maintain internally.
- Threat intelligence integration: These services combine dark web intelligence with broader cybersecurity threat feeds, providing clearer information about attack techniques, criminal groups, & industry-specific threats that are gradually taking shape in the space.
- Incident response support: When your data does appear on the Dark Web, professional monitoring services provide you with instant response support to the incident and this will involve assessing the threat, notifying the customers and coordinating an operation to recover any loss.
Law Enforcement Collaboration: Working Together
- Reporting procedures: Creating a clear plan on how an organization can report dark web crimes to the authorities that will handle it is a faster way to respond to any criminal activity that affects your organization.
- Intelligence sharing: Participating in attempts to share information with others in the same industry helps law enforcement to understand the threat patterns that exist on the dark web & also provides your organization with more knowledge on a particular threat.
- Evidence preservation: Keeping evidence safe until cases against dark web criminals goes to court is very important. Understanding how to do this will make it even easier for prosecutors to win the cases.
Best Practices in Cybersecurity: Building Strong Defenses
- Multi-factor authentication: Ensuring that all systems in an organization have strong multi-factor authentication is a way to protect employee credentials even if they appear on Dark Web online marketplaces.
- Regular security assessments: Carrying out a full security assessment helps identify areas where an organization is vulnerable before dark web criminals notice and exploit them.
- Employee Training Programs: Training the employees regularly helps them recognize social engineering attacks that criminals craft with data they gathered during dark web breaches.
- Incident response planning: Developing & regularly testing incident response plans is a surefire way to respond faster when there are threats from the dark web against your organization.
Education and Awareness: Human Firewall Development
- Security awareness training: Training programs an organization designs to train employees should cover everything about how dark web threats take place, how to recognize social engineering, keeping passwords secure, & how to report incidents properly.
- Phishing simulation: Organizations should simulate phishing attempts regularly using techniques from Dark Web online platforms to help employees develop practical skills to recognize & respond to attacks.
- Threat intelligence sharing: Making sure employees know the current threats coming from the dark web & how criminals attack their victims helps them stay vigilant against the continuous developments in criminal tactics.
- Personal digital hygiene: Teaching employees how they can handle cybersecurity effectively even as individuals in an organization protects both their own information and reduces risks to your organization.
Browse Safely with the Right Security Systems

To protect yourself from dark web threats, you must combine security tools & practices in an effective manner. Even if you never intend to do anything on the Dark Web online platforms directly, criminals operating in hidden networks are very risky to everyone’s security on the web.
Essential Security Tool Categories
- Password management: Using passwords that are not common and very hard to crack for your online accounts, is very important especially now that criminals sell billions of credentials on the dark web. Password managers are very necessary here because they will help you create a strong password and also store them so no one accesses them easily.
- Multi-factor authentication: Making sure your important accounts have 2-factor authentication will protect your information even when your passwords appear in dark web data breaches.
- Security software: Getting security software that covers all loopholes is very necessary. The right one should offer malware protection in real time, web filtering, and be capable of fighting phishing attempts coming from dark web criminal operations.
- VPN services: Virtual private networks also help to protect your privacy while using the web as they don’t allow criminals to get access to your communication or the history of your activities online.
Advanced Protection Strategies
- Dark web monitoring: Relying on a personal dark web, monitoring service is also a good idea as it will go through hidden networks to check if your email addresses, phone numbers, and other personal information appear there and then gives you a message if it finds that your data appeared in criminal databases.
- Credit monitoring: Since financial fraud represents a major category of dark web crime, comprehensive credit monitoring helps detect unauthorized accounts or transactions quickly.
- Identity theft protection: Specialized identity protection services make use of dark web monitoring and recovery assistance plus insurance coverage for incidents where someone’s identity was stolen.
- Secure communication: Using communication tools that offer encryption protects your messages from criminals as they can’t intercept them. This approach protects your sensitive information and keeps them away from Dark Web online platforms.
Browsing Safety Fundamentals
- Software updates: Always making sure you update your operating systems, browsers, and applications with the latest security patches blocks criminals from getting to you through them when there are loopholes about them shared on dark web forums.
- Cautious link clicking: Never clicking on links or downloading attachments that appear suspicious protects your devices against malware distributed through dark web networks.
- Privacy settings: Configuring strong privacy settings on social media and online accounts reduces the amount of personal information available to dark web criminals for social engineering attacks. Reviewing bank & credit card statements regularly is a simple way to know when a transaction by fraudsters on the Dark Web has taken place on your account.
Building a Security-Minded Lifestyle
- Threat awareness: Knowing the current threats coming from the dark web helps you recognize & respond the right way to emerging risks.
- Digital minimization: Keeping the amount of personal information you share online to the barest minimum reduces your level of exposure when data breaches take place and information ends up on dark web platforms.
- Regular security reviews: Reviewing & updating your security practices from time to time is a way to make sure you can defend threats from the dark web whenever they occur especially as they keep changing over time.
- Incident response preparation: Understanding what to do if your information appears on Dark Web online platforms helps minimize damage and accelerate recovery.
Recommended Security Solutions
Choose security software that is mainly suitable for addressing those threats that come directly from the dark web including top-notch malware detection, web protection, & threat monitoring in real time.
Select VPN services that come with very tough encryption, never log your history, and have servers in many jurisdictions to protect your traffic on the internet so that dark web criminals can’t find you during their surveillance.
Put your money into services that actually pay attention to Dark Web online platforms to know if your personal information is anywhere there, providing you with early warning when your data appears in criminal networks.
Strengthen your web browser with strong security settings which might include script blocking, protection against tracking protection, and automatic security updates.
FAQs
The deep web refers to non-indexed parts of the internet, while the dark web is a subset focused on hidden activities. The deep web includes private databases and online banking, whereas the dark web is associated with illicit activities.
A majority are! But, not everything happening on the dark web is bad as some people that are not criminals do legal things there too. Some of them just go there to communicate with others in a secure manner and also browse secretly without anyone noticing them.
The dark web online is even 5,000X more massive than the surface web everybody uses.
21.43% of dark web online users were in the United States. At 12.93%, Germany was the second largest. Finland at 5.22% was third in dark web online traffic.
About 60% of all dark web online websites engaged in some illegal activity; and almost as much, again, contained both leaked data and stolen information.